INFORMATION TECHNOLOGY PAPER 2 GRADE 12 QUESTIONS - NSC EXAMS PAST PAPERS AND MEMOS NOVEMBER 2020
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINFORMATION TECHNOLOGY PAPER 2
GRADE 12
NOVEMBER 2020
NATIONAL SENIOR CERTIFICATE
INSTRUCTIONS AND INFORMATION
- This question paper consists of SIX sections:
SECTION A: Short Questions (15)
SECTION B: System Technologies (25)
SECTION C: Communications and Network Technologies (30)
SECTION D: Data and Information Management (20)
SECTION E: Solution Development (20)
SECTION F: Integrated Scenario (40) - Read ALL the questions carefully.
- Answer ALL the questions.
- The mark allocation generally gives an indication of the number of facts/ reasons required.
- Number the answers correctly according to the numbering system used in this question paper.
- Write neatly and legibly.
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1 Various options are provided as possible answers to the following questions. Choose the answer and write only the letter (A–D) next to the question numbers (1.1.1 to 1.1.5) in the ANSWER BOOK, e.g. 1.1.6 D.
1.1.1 A person who studies an organisation's current computer systems and procedures and then designs information system solutions to help the organisation to operate more efficiently is a …
- systems analyst.
- database analyst.
- system administrator.
- programmer. (1)
1.1.2 A device that can be used to connect many different peripheral devices with a single connector is known as a USB …
- adapter.
- flash drive.
- hub.
- port. (1)
1.1.3 The process of discovering new patterns in data using sophisticated software is known as ...
- data warehousing.
- information processing.
- big data.
- data mining. (1)
1.1.4 The following variable name is NOT valid in Delphi:
- _dSalary
- dSalary
- 1dSalary
- salary1 (1)
1.1.5 Determine the value of y declared as an integer if the following Delphi statement is executed:
y := ceil(25.0/6) + 30 mod 6 – round(15.0/4);
- 3
- 2
- 6
- 1 (1)
1.2 Choose a term from COLUMN B that matches the description in COLUMN A. Write only the letter (A–R) next to the question numbers (1.2.1 to 1.2.10) in the ANSWER BOOK, e.g. 1.2.11 S.
| COLUMN A | COLUMN B |
| 1.2.1 A technique where two or more disks are grouped together by a special controller to minimise the possible loss of data 1.2.2 A field in a database table that can be used to identify records, but not used in the table as a primary key 1.2.3 Security based on the identification of unique physical characteristics of a person 1.2.4 An encryption protocol which encodes data that is sent over the internet 1.2.5 The gap between people that have access to computers and technology and people who do not 1.2.6 The reorganisation of files on a hard disk drive that speeds up access to the files 1.2.7 Software that enables the operating system to communicate with hardware devices 1.2.8 The protocol used to transfer large files between remote computers that have an internet connection 1.2.9 An operation that reverses a database transaction and restores the data to its previous state 1.2.10 Programs that are part of system software and are used for maintenance and administrative tasks |
|
(10 x 1)
(10)
TOTAL SECTION A: 15
SECTION B: SYSTEM TECHNOLOGIES
QUESTION 2
SCENARIO
The owner of a start-up importing/exporting business asked your advice on a number of IT-related issues.
2.1 The computer technician who will assemble the computers to be used in the office suggested that each computer should have a solid-state drive and a hard drive.
2.1.1 State ONE advantage that a solid-state drive has over a conventional hard drive. (1)
2.1.2 State ONE disadvantage of a solid-state drive compared to a conventional hard drive. (1)
2.2 Each of the office computers will be equipped with 8 GB of RAM and Windows 10 as the operating system.
2.2.1 RAM is considered to be volatile memory. What does volatile mean in this context? (1)
2.2.2 The owner has heard that some computers can only use 4 GB of RAM. He is concerned that he will be paying for hardware that will not be utilised.
Explain why these office computers will be able to utilise all 8 GB of RAM. (1)
2.2.3 The computer technician needs to start installing the operating system for the office computers.
- Indicate whether the hard disk drive or the solid-state drive would be the best option on which to install the operating system. (1)
- Give TWO reasons why you recommend the drive in your answer to QUESTION 2.2.3(a). (2)
2.3 The business' computers will run on Microsoft Windows 10, but there are applications that the owner wants to use that can only run on MacOS.
2.3.1 Suggest a possible technology that can be used to run both operating systems without partitioning the hard drive. (1)
2.3.2 Someone recommended that the latest service pack should be installed for the Windows operating system.
Briefly explain what a service pack is. (2)
2.4 VB.NET is a high-level programming language.
2.4.1 Define a high-level programming language. (1)
2.4.2 Interpreters and compilers are used to 'translate' a high-level programming language into machine code.
- Explain the difference between interpreters and compilers by stating the difference in the approach they follow when 'translating' code. (2)
- Explain the difference between interpreters and compilers by stating the way each provides feedback and presents the result. (2)
- Does Delphi use an interpreter or a compiler? (1)
2.4.3 An API is used when coding in a high-level programming language. What is the function of an API? (2)
2.5 Because of modular design, the latest desktop computers have many slots and connectors to allow for computer components to be added.
Name the slot or connector used to add the following modules/components:
2.5.1 RAM (1)
2.5.2 DVD drive (1)
2.5.3 Graphics card (1)
2.6 Motherboards transfer a huge amount of data between various components at any given moment in time.
Explain how the system clock aids in coordinating the transfer of data on a motherboard. (2)
2.7 Consider the diagram below illustrating a process performed by the CPU: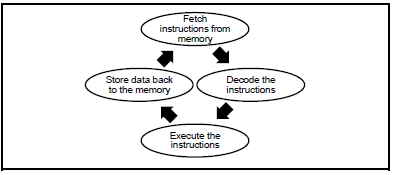
2.7.1 What is the process above called? (1)
2.7.2 The CPU and the RAM communicate with each other via a direct path/connection on the motherboard.
Name this direct path/connection. (1)
TOTAL SECTION B: 25
SECTION C: COMMUNICATIONS AND NETWORK TECHNOLOGIES
QUESTION 3
3.1 Wi-Fi, UTP cables and fibre-optic cables are network media that need to be considered when networks are set up. Fibre-optic cables have a greater bandwidth, but can be expensive.
3.1.1 Network bandwidth is measured in Mbps.
- Describe bandwidth in this context. (1)
- Expand the abbreviation Mbps. (1)
3.1.2 Apart from having a greater bandwidth and higher speed, name TWO other advantages of fibre-optic cables as opposed to UTP cables. (2)
3.1.3 Give TWO reasons why UTP cables are sometimes preferred in an office environment rather than Wi-Fi. (2)
3.1.4 Define the term network backbone. (1)
3.1.5 It has been stated that an NIC is a basic but essential piece of equipment to set up a network.
State the function of an NIC. (1)
3.2 YouTube and Netflix are examples of VOD services.
Explain what a VOD service entails. (1)
3.3 AUPs outline the rights and responsibilities of users which is an important requirement in network environments.
3.3.1 Explain why an organisation should include restriction details on the installation of BitTorrent applications in their AUP. (1)
3.3.2 State the condition that should be adhered to, to ensure that the use of BitTorrent is legal. (1)
3.4 Blogs are commonly used as a social media tool.
Give TWO reasons why information published on blogs could be inaccurate. (2)
3.5 The design of web pages can be static or dynamic.
How does a dynamic web page differ from a static web page from a user's perspective? (2)
3.6 Digital signatures are common in the world of electronically conducted business.
What is the purpose of a digital signature? (1)
3.7 Web developers use a variety of technologies, such as HTML, CSS and AJAX, to produce visually impressive websites.
3.7.1 What type of software on the client's computer is used to execute HTML instructions? (1)
3.7.2 Name TWO ways in which CSS files help to maintain uniformity across several web pages. (2)
3.7.3 What is the purpose of AJAX in the context of website development? (2)
3.8 DDoS attacks are typically performed by botnets. 3.8.1
Define the term botnet. (2)
3.8.2 Describe what happens in a DDoS attack. (3)
3.8.3 What is a zombie in the context of a botnet? (1)
3.9 Cybercrime is a common phenomenon in the modern world.
3.9.1 Briefly explain what a keylogger is. (1)
3.9.2 Suggest TWO safeguards that computer users can employ to avoid becoming the victims of cybercrime. (2)
TOTAL SECTION C: 30
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
SCENARIO
The import of plants can be dangerous as the plants may be invasive or introduce diseases to native plants and ecosystems. A rigid testing process must first be conducted before any alien plant may be taken across a country's borders.
A database is used to manage requests and keep track of the number of plants brought into the country. An application needs to be made and processed each time an importer wants to import plants.
The database contains two tables which are designed as follows:
Table: tblImporters
| Field name | Data type | Description |
| ImporterID | Short Text (10) | An ID to uniquely identify an importer entity |
| ImporterName | Short Text (10) | Name of organisation/person of the importer |
| ImporterCountry | Short Text (10) | Location/Country the importer is from |
| DateRegistered | Date/Time | Short date which indicates the date that the importer was registered |
Table: tblApplications
| Field name | Data type | Description |
| ApplicationID | AutoNumber | An ID to uniquely identify a log record/request to import plants |
| PlantName | Short Text (80) | The scientific name of the plant requested to be imported |
| Quantity | Number | The number of plants requested to be imported |
| Approved | Number | 0 indicates that the import request has been denied 1 indicates that the import request has been approved |
| DateReceived | Date/Time | The date on which the import request was made/the record was created |
| DateProcessed | Date/Time | The date on which the import request was approved or denied |
| ProcessedDuration | Number | The number of days it took for the request to be processed |
4.1 The database design is incomplete. Primary keys have not been identified yet and a relationship still needs to be created between the two tables, tblImporters and tblApplications.
4.1.1 State TWO specific requirements relevant to the content of a primary key field. (2)
4.1.2 A foreign key field needs to be identified in order to establish a relationship between the tables.
- Identify a suitable foreign key and give the name of the field and the name of the table that contains the field. (2)
- Name the type of relationship between tables tblImporters and tblApplications. (1)
4.1.3 Name the diagram used to illustrate the relationship between the two tables. (1)
4.2 Suggest a more appropriate data type for the Approved field in the tblApplications table. (1)
4.3 Explain why the ProcessedDuration field in the tblApplications table is redundant. (1)
4.4 During the beta version testing of the system, the DBA noticed inconsistencies in the capturing of the names of countries in the ImporterCountry field. For example, Canada's name was captured in the following different ways:
CA
Canada
Cannada
4.4.1 Explain what is meant by the term beta version. (1)
4.4.2 Suggest a way in which the system can be adapted so that the name of a country is captured uniformly in the ImporterCountry field. (1)
4.5 Ensuring the quality of the data involves extensive data validation and verification. Use the field Approved in the tblApplications table to explain the following:
4.5.1 Data validation (2)
4.5.2 Data verification (1)
4.6 Only authorised people should have access to the database server hosting the database.
Suggest any TWO physical ways in which access to the database server can be restricted. (2)
4.7 Data independence is a characteristic of a well-designed database.
4.7.1 Explain the term data independence. (2)
4.7.2 One level of data independence is physical independence.
Name another level of data independence. (1)
4.7.3 Give TWO important reasons for enforcing data independence. (2)
TOTAL SECTION D: 20
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
5.1 There are many types of errors that can occur in software development.
5.1.1 Differentiate between a syntax error and a runtime error. (2)
5.1.2 Give TWO guidelines on how a programmer can construct useful error messages. (2)
5.2 Several search algorithms are available to be used, e.g. binary and linear search algorithms.
What is the prerequisite for an array to be searched when using the binary search algorithm? (1)
5.3 A novice programmer was testing a concept and wrote the following segment of Delphi code: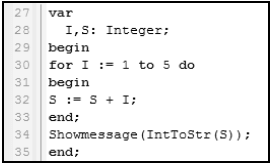
5.3.1 The programmer was expecting the final value of the variable S to be 15, but the dialog box showed the value of the variable S as 38319711.
Give a possible reason for this unexpected result. (1)
5.3.2 Suggest TWO ways in which to improve the code of the novice programmer to be more readable. (2)
5.4 Consider the following flowchart: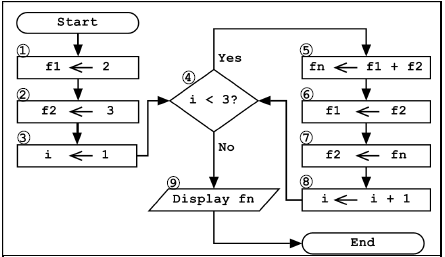
Redraw the following incomplete trace table into your ANSWER BOOK. Complete the trace table by tracing step by step through the flowchart depicted above.
| Block Nr | f1 | f2 | i | i<3? | fn | Output |
| 1 | 2 | |||||
| 2 | 3 | |||||
| 3 | 1 |
(6)
5.5 Write an alternative line of Delphi code that will have the same effect as the following line of code:
i:= i+1; (1)
5.6 Consider the following class diagram:
| TEvent |
| - fLocation: String - fEventDate: String - fCapacity: integer |
| <<CONSTRUCTOR>> Create(location, eventDate: String; capacity: integer) + getLocation(): String + setLocation(location) + getEventDate(): String + setEventDate(eventDate: TDate) + getCapacity(): String + setCapacity(capacity: integer) + toString(): String |
5.6.1 What do the plus (+) and minus (-) symbols represent respectively? (2)
5.6.2 Identify TWO errors in the class diagram provided. (2)
5.6.3 Identify an auxiliary method in the class diagram provided. (1)
TOTAL SECTION E: 20
SECTION F: INTEGRATED SCENARIO
QUESTION 6
A small export company specialising in food-related products are considering upgrading their ICT systems. You are part of an IT company that assists them with advice.
6.1 There are many factors that can influence a computer's performance.
6.1.1 Give TWO reasons why the use of cache memory allows the CPU to perform tasks faster than when RAM is used. (2)
6.1.2 Name TWO other physical aspects of the CPU that have a direct influence on system performance. (2)
6.1.3 The available memory (RAM) also has an influence on a computer's performance. Therefore, the operating system allocates additional memory if the available memory is limited.
- What is the additional memory which is allocated by the operating system if required, called? (1)
- Explain how the operating system uses the additional memory when required. (2)
6.2 The company considers using free software as an alternative in order to save on licensing costs.
State TWO disadvantages of using an open and free operating system, such as Linux, as an alternative to an operating system such as Microsoft Windows. (2)
6.3 SaaS is a concept related to cloud computing, which in turn relies heavily on virtualisation technologies.
6.3.1 State TWO advantages associated with the use of cloud computing. (2)
6.3.2 State TWO virtualisation techniques employed by companies that offer cloud services. (2)
6.4 Marketing and e-communication play a major role in the company's daily activities.
6.4.1 State TWO advantages of using web-based e-mail rather than an ISP-based e-mail. (2)
6.4.2 The internet is used to search for suppliers of products to export.
- Explain how a search engine uses customised searching to customise search results according to a user's profile. (2)
- Explain what context-aware searches entails. (1)
- How can the business benefit from context-aware searches? (1)
6.4.3 Give TWO reasons why the company should invest in the development of a mobile app if a website has already been created. (2)
6.5 The business is currently using a centralised database. They have been advised to switch to a distributed database system.
Give TWO reasons why you would recommend that they do NOT switch to a distributed database system. (2)
6.6 An employee was exploring the system settings on his/her computer and encountered a screen displaying the following information: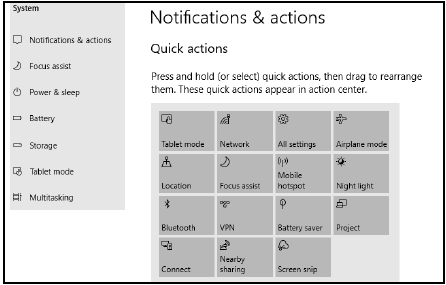
6.6.1 Why is a VPN useful to employees? (2)
6.6.2 Indicate ONE option in the screenshot above that is related to green computing. (1)
6.6.3 Define the term mobile hotspot. (2)
6.6.4
- Briefly explain what multitasking is. (2)
- How does multiprocessing differ from multitasking? (2)
6.6.5 Explain what nearby sharing in this context entails. (1)
6.7 As part of upgrading their ICT systems, the company considers cancelling their landline in favour of using VoIP for communication with their customers.
State TWO possible disadvantages of relying solely on VoIP for communication with customers. (2)
6.8 The company often needs to store food in their industrial fridges until it can be shipped for exporting.
Make TWO recommendations on how Internet of Things (IoT) technology can be used to ensure that the company does not suffer damage due to possible problems with keeping the temperatures in their fridges at optimal levels. (2)
6.9 The company uses security badges with embedded RFID tags to apply access control at its premises.
6.9.1 What medium is used by RFID to identify objects? (1)
6.9.2 State TWO advantages of using RFID rather than barcode technology. (2)
TOTAL SECTION F:40
GRAND TOTAL:150