INFORMATION TECHNOLOGY PAPER 2 GRADE 12 QUESTIONS - NSC PAST PAPERS AND MEMOS NOVEMBER 2021
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINSTRUCTIONS AND INFORMATION
- This question paper consists of SIX sections:
SECTION A: Short Questions (15)
SECTION B: System Technologies (25)
SECTION C: Communications and Network Technologies (30)
SECTION D: Data and Information Management (20)
SECTION E: Solution Development (20)
SECTION F: Integrated Scenario (40) - Read ALL the questions carefully.
- Answer ALL the questions.
- The mark allocation generally gives an indication of the number of facts/reasons required.
- Number the answers correctly according to the numbering system used in this question paper.
- Write neatly and legibly.
QUESTIONS
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1 Various options are provided as possible answers to the following questions. Choose the answer and write only the letter (A–D) next to the question numbers (1.1.1 to 1.1.5) in the ANSWER BOOK, e.g. 1.1.6 D.
1.1.1 Software that translates programming instructions written in a high-level language into an executable file is called a …
- compiler.
- assembler.
- driver.
- interpreter. (1)
1.1.2 Which data type for variable x in the following expression is CORRECT?
x := 13 mod 3 = 0;
- Integer
- Real
- Boolean
- Char (1)
1.1.3 An update to correct a specific bug in software is called a …
- purge.
- patch.
- backup.
- rollback. (1)
1.1.4 … refers to the simulation of human thinking in machines that are programmed to think like humans and mimic their actions.
- A simulator
- A learning algorithm
- Artificial intelligence
- Human-computer interaction (1)
1.1.5 What value will be displayed?
iCount ← 9
While iCount < 10 do
iCount ← iCount + 1
End While
Display iCount
- 9
- 10
- 11
- Nothing will be displayed (1)
1.2 Choose a term from COLUMN B that matches the description in COLUMN A. Write only the letter (A–T) next to the question numbers (1.2.1 to 1.2.10) in the ANSWER BOOK, e.g. 1.2.11 U.
| COLUMN A | COLUMN B |
| 1.2.1 Used to help detect errors in manually entered data, such as bank account numbers 1.2.2 A peer-to-peer protocol used to share large files over the internet 1.2.3 Storage space used by the operating system when there is insufficient RAM 1.2.4 A component that is best suited to display the content of a two-dimensional array with multiple rows and columns 1.2.5 An error that causes a break or termination in the running of a program 1.2.6 Data capturing technique that stores more data and is more interactive than conventional barcode systems 1.2.7 When a record in a database is open, either for editing or for inserting, the record is flagged as 'in use' 1.2.8 People are manipulated to divulge confidential information 1.2.9 Part of the memory that stores user preferences for the boot-up sequence 1.2.10 Providing large amounts of data that may leave the user confused and unable to make decisions |
|
(10 x 1) (10)
TOTAL SECTION A: 15
SECTION B: SYSTEM TECHNOLOGIES
QUESTION 2
2.1 Journalists are issued with laptops when they start working at a magazine publishing company. The company only uses free open-source software (FOSS).
2.1.1 Explain the concept open source in the context of FOSS. (2)
2.1.2 Give ONE example of a free operating system the company could install on a laptop. (1)
2.1.3 State TWO disadvantages of using free open-source software. (2)
2.2 The laptops are equipped with either an HDD or an SSD.
2.2.1 Users of laptops equipped with HDDs are advised to defragment the HDD regularly.
Briefly explain what defragmentation is. (2)
2.2.2 Write out the abbreviation SSD in full. (1)
2.2.3 Explain why an SSD accesses the data faster than an HDD. (2)
2.3 The journalists can access their data remotely using virtualisation or Software as a Service (SaaS).
2.3.1 Define the term virtualisation. (1)
2.3.2 Office365 is an example of SaaS.
- Except for remote data access, state TWO benefits of using SaaS. (2)
- Describe how the license model of SaaS works. (2)
2.4 The company takes precautionary measures to protect the magazine's data.
2.4.1 An incremental backup strategy has been implemented to safeguard data. Explain how an incremental backup strategy works. (2)
2.4.2 The company considers installing biometric readers on all the laptops. How would a biometric reader help safeguard the data on a laptop? (1)
2.5 Power outages and power surges are often experienced in rural areas where journalists work.
2.5.1 What device can be used to ensure that journalists are not affected by unexpected power outages? (1)
2.5.2 If the USB ports of a laptop are damaged due to a power surge, how could a user get his/her peripheral devices to connect to the laptop? (1)
2.6 The journalists use their laptops for word processing, research and to upload articles to the company's electronic database only.
2.6.1 Would you classify these journalists as power users or SOHO users? (1)
2.6.2 Explain how multithreading is applied in a word processor. (2)
2.6.3 The processing speed of the computers at head office is very low. Explain why installing more RAM could improve a computer's performance. (2)
TOTAL SECTION B: 25
SECTION C: COMMUNICATIONS AND NETWORK TECHNOLOGIES
QUESTION 3
The magazine publishing company has branches all around the world that operates on a large scale.
3.1 Having a large computer network presents potential challenges.
3.1.1 Describe what a computer network is. (2)
3.1.2 What type of network could be used by an international company such as this? (1)
3.1.3 State TWO disadvantages of using a computer network. (2)
3.2 It was decided that a network with a star topology will be installed in their building at head office.
3.2.1 Define the term topology. (1)
3.2.2 Explain what a star topology entails. (2)
3.3 It was suggested that VoIP technology be utilised by the company when communicating with clients.
3.3.1 Give TWO reasons why a company would benefit from using VoIP technology. (2)
3.3.2 Besides the device you are using, state ONE other requirement needed to make a phone call using VoIP software. (1)
3.4 Journalists need to use the internet to do research for their articles.
3.4.1
- What is the purpose of a web browser? (1)
- Why can a web browser not be used on its own when searching for information? (1)
3.4.2 Cookies are used to improve the browsing experience of users.
- What is a cookie in this context? (2)
- Explain how a cookie will enhance the browsing experience of users. (1)
3.4.3 While browsing the internet, a journalist discovered that smaller magazine companies get many more likes on social media than bigger, more popular magazine companies. This could be due to the activities of click farms.
Explain what a click farm is. (2)
3.5 The company needs to renew their contract with their internet service provider (ISP). For this purpose, they need to evaluate the range and bandwidth provided by their current ISP, as well as other practices that their ISP implements that could affect internet access, such as shaping and throttling.
3.5.1 Differentiate between the terms range and bandwidth. (2)
3.5.2 Differentiate between shaping and throttling in this context. (3)
3.6 The company requires a digital certificate, issued by a certificate authority (CA), before launching their website.
3.6.1 Explain the purpose of a digital certificate when SSL encryption is used. (1)
3.6.2 How would you identify a website that is encrypted with a secure connection? (1)
3.7 Using the internet presents dangers such as being subjected to hacking and computer worms.
3.7.1 Define the term computer worm. (1)
3.7.2 State ONE activity performed by your electronic device that indicates that the device could be infected with a computer worm. (1)
3.7.3 Briefly explain how a firewall can protect a network from being hacked. (2)
3.7.4 Give the term used to describe a person that is hired by a company to hack into the company's network to test their level of security. (1)
TOTAL SECTION C: 30
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
SCENARIO A media company is responsible for managing the publishing of a wide variety of local and international magazines. An MS Access database is used to manage the distribution of magazines published by several publishers. |
The database contains two tables which are designed as follows:
Table: tblPublishers
Field name | Data type | Description |
PublisherID (PK) | Text | An ID that uniquely identifies the publisher |
PublisherName | Text | The name of the publisher |
Address | Text | The address of the publisher |
PublisherContactNo | Text | The contact number of the publisher |
Table: tblMagazines
Field name | Data type | Description |
MagazineCode (PK) | Text | A code that uniquely identifies the magazine, e.g. MC001 |
Title | Text | The title of the magazine |
Type | Text | The type of magazine (sport/business/fashion/ leisure/other) |
NumPrinted | Text | The number of magazines printed |
ReleaseDate | Text | The release date of the magazine |
Price | Text | The price per magazine |
eMagazine | Text | True if the magazine is available in e-format and false if not |
PublisherID (FK) | Text | An ID that uniquely identifies the publisher |
4.1 It is advised that a relational database should be created.
4.1.1 What is a relational database? (1)
4.1.2 Name and explain ONE anomaly that can occur in an operational database if the database is not normalised. (2)
4.2 Identify THREE fields in the table tblMagazines that require more suitable data types.
Suggest a more suitable field name and data type for EACH field that you identified. (3)
4.3 Draw an ERD of tblPublishers and tblMagazines showing the following:
- The relationship type between the entities
- A suitable action verb describing the relationship (3)
4.4 Many database management systems (DBMSs) have built-in integrity controls that help to maintain the data integrity in the database.
4.4.1 Explain what data integrity entails. (2)
4.4.2 Apart from normalisation, state ONE other way to ensure data integrity in a database. (1)
4.5 State TWO ways in which the company can benefit from the use of a database management system. (2)
4.6 Human error results in many issues when entering information into a database.
Suggest ONE way to minimise user input. (1)
4.7 Explain why using a server-based database instead of a desktop database management system would be the better option for a company. (2)
4.8 Data warehousing plays an important role in data maintenance.
How does data warehousing affect the size and speed of a database? (2)
4.9 The company's database is used for data mining.
State the role of a human in the data mining process. (1)
TOTAL SECTION D: 20
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
Applicants for a software engineering position at the magazine company need to answer some questions on software development.
5.1 Indicate whether the following statements are TRUE or FALSE. Write only 'true' or 'false' next to the question numbers (5.1.1 to 5.1.3) in the ANSWER BOOK.
5.1.1 An array can only store elements of the same data type. (1)
5.1.2 The index value for the first element in a Delphi array is always one. (1)
5.1.3 The value 23 will be displayed in the rich edit component when the following code is executed:
var
arrNumbers : array[1..5] of Integer = (4,2,3,1,8);
iValue : Integer;
begin
iValue := arrNumbers[2]+ arrNumbers[3];
redOutput.Lines.Add(intToStr(iValue));
end; (1)
5.2 The following algorithm written in pseudocode has been provided to enter integer values into variable A and B, swap the contents of the two variables and display the values:
Input A
Input B
A ← B
B ← A
Display A
Display B
5.2.1 What will be displayed if the value of 5 is entered into variable A and the value of 6 is entered into variable B? (2)
5.2.2 Rewrite the algorithm so that the content of the variables will be swapped correctly. (3)
5.3 A group of friends gathers once a week to have dinner at a local restaurant. They throw a six-sided dice three times to decide what type of meal they will have.
The following rules apply:
- If the number of the first throw is larger than the number of the second throw, they will eat chicken, or else
- If the number of the third throw is less than the number of the first throw, they will eat fish, or else
- They will eat burgers.
The following incomplete Delphi solution is provided for the scenario above:
var
iFirst, iSecond, iThird : Integer;
sMeal : string;
begin
iFirst := Inputbox('Enter value of first throw', '', '');
iSecond := Inputbox('Enter value of second throw', '', '');
iThird := Inputbox('Enter value of third throw', '', '');
// Complete the program (Question 5.3.2)
showMessage(sMeal);
end.
5.3.1 Explain why a syntax error will be displayed when the provided part of the program is executed. (1)
5.3.2 Complete the missing part for the program provided, to assign the correct type of meal to the sMeal variable according to the rules in the scenario above.
Assume that the syntax error referred to in QUESTION 5.3.1 has been corrected. (5)
5.3.3 Which sequence of throws (A, B, C or D) will result in the group of friends having burgers as a meal? (2)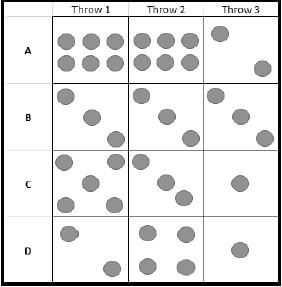
5.4 The following UML (unified modelling language) class diagram represents a magazine object.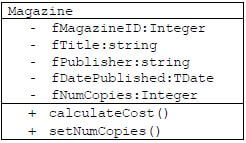
5.4.1 Give TWO reasons why an UML diagram is an important OOP modelling tool. (2)
5.4.2 What is the purpose of an accessor method? (1)
5.4.3 Give an example of a mutator method in the given class diagram. (1)
TOTAL SECTION E: 20
SECTION F: INTEGRATED SCENARIO
QUESTION 6
A magazine company needs to stay up to date with the latest trends in technology in order to deliver a relevant service to their customers.
6.1 The company has an online version of their magazine hosted on a website. Users can interact with videos and dynamic content which can be customised for each user. Local and server-side scripting, CSS and SQL are used on the website.
6.1.1 Give ONE example of a local or server-side scripting language. (1)
6.1.2 Explain the main purpose of running a CSS on a website. (2)
6.1.3 What is the purpose of using SQL statements on a website? (2)
6.1.4 As magazine readers are from different countries, they can access the website conveniently from any location.
- Name the type of computing which refers to software that is based on a user's location. (1)
- What satellite technology will enable an application to automatically update information displayed on a device based on the location of the user? (1)
6.2 The company regularly upgrades some of its devices and disposes of devices that are no longer in use.
6.2.1 Name TWO hardware components on the motherboard of a computer that can be upgraded. (2)
6.2.2 Some offices are equipped with desktop computers instead of laptops.
State TWO benefits of using desktop computers over laptops. (2)
6.2.3 After defragmenting their hard disks, some staff members complained that their computers are still functioning at a low speed.
Suggest a way, other than defragmenting the hard disks, to improve the speed of the computers without adding additional hardware components. (1)
6.2.4 Some of the devices replaced by the company need to be disposed of responsibly.
Suggest TWO ways in which the computers can be disposed of in an eco-friendly manner. (2)
6.3 Office automation has not been very popular amongst many workers in the magazine industry.
6.3.1 What is office automation? (1)
6.3.2 State TWO advantages of office automation to workers. (2)
6.4 The company is setting up a computer network at a new branch.
6.4.1 How would the employees be able to connect to the company's Wi-Fi network? (1)
6.4.2 Attenuation can be a problem in a cabled network.
- Why is attenuation a problem in networking? (1)
- What type of communication medium can be used to limit attenuation? (1)
6.4.3 Give TWO reasons why WiMAX technology is considered to be more suitable than Wi-Fi technology. (2)
6.5 The development of mobile technologies and devices promoted the use of social media and microblogging sites.
6.5.1 Describe the concept microblogging. (2)
6.5.2 The excessive use of social media can impact negatively on the health of users.
State TWO potential health problems caused by the extensive use of social media. (2)
6.6 IoT is one of the technologies that is investigated by the company to be used more effectively in future
6.6.1 Expand the abbreviation IoT. (1)
6.6.2 State TWO ways in which IoT devices connect to the internet. (2)
6.7 Distributed computing is being investigated by the company for possible implementation.
6.7.1 What is distributed computing? (2)
6.7.2 Give ONE example where distributed computing could be used. (1)
6.8 The company decided to do research on the blockchain technology.
Define the concept blockchain technology. (2)
6.9 A multi-factor authentication system is used to log onto a website to make payments for services rendered.
Explain how a multi-factor authentication system works. (2)
6.10 Why does electronic media use DRM? (1)
6.11 The following shared folder with permissions has been created: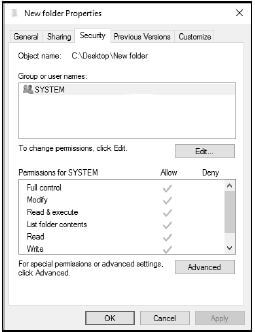
6.11.1 State TWO tasks that can be performed with files in the folder with Read permissions. (2)
6.11.2 Who would usually be allocated the 'Full control' permission? (1)
TOTAL SECTION F: 40
GRAND TOTAL: 150