INFORMATION TECHNOLOGY PAPER 2 GRADE 12 MEMORANDUM - NSC PAST PAPERS AND MEMOS FEBRUARY/MARCH 2017
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINFORMATION TECHNOLOGY
PAPER 2
GRADE 12
NSC PAST PAPERS AND MEMOS
FEBRUARY/MARCH 2017
MEMORANDUM
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1
1.1.1 D ✔ (1)
1.1.2 B ✔ (1)
1.1.3 C ✔ (1)
1.1.4 A ✔ (1)
1.1.5 C ✔ (1)
1.1.6 B ✔ (1)
1.1.7 B ✔ (1)
1.1.8 A ✔ (1)
1.1.9 D ✔ (1)
1.1.10 D ✔ (1)
1.2
1.2.1 Creative Commons License ✔
1.2.2 World Wide Web consortium (W3C) ✔ (1)
1.2.3 Click farms ✔ (1)
1.2.4 Overclocking ✔ (1)
1.2.5 Robotics ✔ (1)
TOTAL SECTION A: 15
SECTION B: SYSTEMS TECHNOLOGIES
QUESTION 2
2.1
2.1.1 Threads are part of the same program ✔ that runs simultaneously and independently. ✔ (2)
2.1.2 Process management is the task of making sure that each process gets enough CPU time and access to memory, storage and other hardware so that it can work without interfering with, or being interfered with, by other processes.
Concepts:
- Access to CPU, memory, storage ✔
- No interference with other processes ✔ (2)
2.1.3 No ✔
- Each core can process one task at a speed of 1.58 GHz ✔ (2)
2.1.4
- Cache memory is special high speed memory ✔ close to or on the CPU ✔ (2)
- To prevent a slower medium ✔ from slowing down the performance ✔ of a faster medium
OR
The speed of the CPU is higher than most motherboards and RAM. So extensive use is made of cache to keep the CPU running at optimum capacity. (2)
2.2
2.2.1 Solid state drive ✔ (1)
2.2.2
- There is no physical moving parts when writing or reading on an SSD ✔ (1)
- There is no time spent to move to the position where file is saved/can access it immediately. ✔ (1)
2.2.3 Set up the SSD as the system/primary drive on which the operating system ✔is installed for faster boot up and system performance. ✔
Set up the HDD as a secondary drive ✔ which contains all your music/video files. ✔ (4)
2.3 Any TWO ✔✔
- To ensure that the latest viruses will not attack the system
- New features of the virus are added
- Update the virus database (2)
2.4
2.4.1 PCI-E expansion slot on the motherboard ✔ (1)
2.4.2 The built-in video card is used when doing routine tasks ✔ because it uses much less power and battery life
The video adapter will be used when programs require high resolution/good graphics✔ (2)
2.5
2.5.1 Any ONE ✔
- Too many applications open
- Programs too large to run from available RAM (1)
2.5.2 No, ✔
- access to virtual memory is slower than access to RAM ✔ (2)
TOTAL SECTION B: 25
SECTION C: COMMUNICATION AND NETWORK TECHNOLOGIES
QUESTION 3
3.1
3.1.1 Any TWO ✔✔
- Short distance
- Cheap
- Easy to install (2)
3.1.2
- A router makes communication possible between different networks/Allows access to the Internet. ✔
- A switch makes communication possible between devices on a network ✔
- School needs both router and switch since there may be gamers who will participant online from outside the school's network. ✔ (3)
3.1.3
- TCP/IP is primarily used for a point-to-point set up, meaning it allows for communication from one point (server) ✔ in the network to another point (client). ✔ (2)
3.2
3.2.1 A cellular network ✔
Also accept: WAN and 4G (1)
3.2.2 Any TWO ✔✔
- Microwaves
- Light
Also accept Electro-magnetic waves (2)
3.3
3.3.1 Global positioning system ✔ (1)
3.3.2 The GPS will receive signals sent by at least three satellites ✔and triangulate the position ✔using trilateration. (2)
3.4
3.4.1 It is storage space in the cloud ✔ to which you are given access once you purchased the media. ✔ (2)
3.4.2 High bandwidth ✔and a lot of data are required to watch movies online ✔ (2)
3.5
3.5.1 A Rich Internet Application is a web application ✔ that is designed to deliver the functions and features of a traditional desktop application. ✔ (2)
3.5.2 Any ONE ✔
- Google Docs
- Microsoft Office Live (1) TOTAL SECTION C: 20
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
4.1
4.1.1 Foreign key ✔ (1)
4.1.2 Answer C – any number of games per day ✔ (1)
4.1.3
- There is a relationship between tblPlayers table and tblGamesPlayed table. ✔ The PlayerID F566 is contained in the tblGamesPlayed table and therefore cannot be deleted from the table where it is a primary key. ✔ (2)
- All records containing PlayerID F566 must first be deleted from tblGamesPlayed table ✔ and then only can this record be deleted from tblPlayers table. ✔ (2)
4.2
4.2.1 SELECT * FROM tblGames WHERE TimePlayed >= #12:00# AND TimePlayed <= #15:00#
- ✔ SELECT *
- ✔ FROM tblGames
- ✔ WHERE TimePlayed >= #12:00#
- ✔ AND TimePlayed <= #15:00# (4)
4.2.2 UPDATE tblGamesPlayed SET Score = Score * 1.15 WHERE GameID = "G103"
- ✔ UPDATE tblGamesPlayed
- ✔ SET Score
- ✔ = Score * 1.15
- ✔ WHERE GameID = "G103" (4)
4.3
4.3.1 The highest score ✔ achieved for each game ✔ sorted from highest to lowest according to the score ✔ (3)
4.3.2
- 1 ✔
- MF ✔
- s- ✔
- 156 ✔ (4)
4.4 We only need the IDNumber field since the date of birth can be derived ✔ from the first six digits of the IDNumber field. ✔ (2)
4.5 Any TWO ✔✔
- Validate data fields.
- Avoid entering SQL statements into data fields.
- Restrict access to the database.
- Avoid disclosing database error information. (2)
TOTAL SECTION D: 25
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
5.1
5.1.1 Text file ✔ (1)
5.1.2 One-dimensional array ✔ (1)
5.1.3 Two-dimensional array ✔ (1)
5.1.4 Variable ✔ (1)
5.2
5.2.1 Restricting access to a class's attributes ✔ by declaring the attributes as private ✔ (2)
5.2.2 Any TWO ✔✔
- Developers can work on separate modules of the software independently/save time/get the project done faster
- Code can be written once and re-used
- Code can be debugged easily/Less code to work through with debugging. (2)
5.2.3
- TRUE ✔ (1)
- FALSE ✔ (1)
5.3
Counter ? 1 ✔
NumberOfRows? input from keyboard ✔ Any order
Loop K from 1 to NumberOfRows ✔
RowLine ? "" ✔
Loop L from 1 ✔ to 2 * K – 1 ✔
RowLine ? RowLine ✔+ Counter + " " ✔ Must be in this order
Increment (Counter) ✔
Display RowLine ✔ (10)
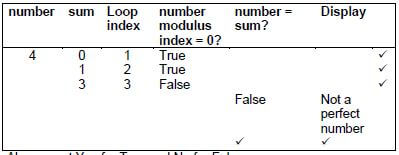 5.4
5.4
5.4.1 (5)
Also accept Yes for True and No for False
5.4.2 Line 6: ✔ If number = sum – number ✔ (2)
TOTAL SECTION E: 27
SECTION F: INTEGRATED SCENARIO
QUESTION 6
6.1
6.1.1 windermere.co.za ✔ (1)
6.1.2 Marlene Heyns and Kerry Mansen ✔ (1)
6.1.3 Spoofing ✔ (1)
6.2
6.2.1 Secure Sockets Layer is an encryption protocol ✔ for managing the transmission of sensitive data over the Internet. ✔ (2)
6.2.2 Any TWO ✔✔
- Identification information of the user
- Identification details of the website used
- The validity period of the digital certificate
- Serial number of digital certificate
- Digital signature of issuer
- Name of issuer
- Owners of public key (2)
6.3
6.3.1 Files are compressed on the same disk ✔ and the original file is deleted thereby creating space. ✔
OR
Old/unused files are usually moved to a secondary storage device (other computer/hard drive dedicated for this purpose
Concepts:
- Compressed/moved to secondary storage
- Original files deleted (2)
6.3.2 No, ✔
- a virtual server will not save space as it uses the resources of the existing machine ✔
OR
Yes, If the cloud is used as a server.
NOTE:
The first mark is only awarded if the justification is correct. (2)
6.4
6.4.1 Any ONE ✔
- Turn down the quality settings to a lower setting.
- Adjust the operating systems built-in content distribution network used for streaming large files. (1)
6.4.2 A firewall could be configured to allow specific/authorised ✔ incoming/outgoing traffic. ✔
Also accept
- A firewall could be configured to block specific/unauthorised incoming/outgoing traffic. (2)
6.4.3 With BitTorrent parts of the file ✔are downloaded from multiple clients. ✔ (2)
6.4.4 No, BitTorrent itself is merely a file sharing protocol ✔ and is not illegal to use however the user must guard against downloading illegal software. ✔ (2)
6.5
6.5.1 NFC is a set of communication standards which allow peer-to-peer data exchanges ✔ between two closely held end points. ✔ (2)
6.5.2 RFID (Radio Frequency Identification) ✔ (1)
6.6
6.6.1 Each Operating system uses different architectures✔ and has different ways of interfacing with software ✔so a different 'version' has to be written for each OS platform. (2)
6.6.2 An example would be if a game was installed using Windows 7 ✔ it must still work if the operating system was updated to Windows 8 or Windows 10. ✔ (2)
6.7
6.7.1 The ability of the server to access more resources when required ✔ and to decrease the use when no longer required so that the game does not hang/stop when many users ✔ are playing.
Concepts:
- Adapt to requirements
- Continuous changes (2)
6.7.2 The data does not pass through any central point. ✔ (1)
6.8
6.8.1 Apps are programs designed to run on mobile devices. ✔ (1)
6.8.2 Any TWO ✔✔
- Dedicated access/immediate access/faster access.
- Can register from anywhere using a mobile device.
- Allows users to receive automatic notification as soon as the registration has been done/immediate notification. (2)
6.9
6.9.1 Software ✔ that is permanently installed ✔ on a ROM chip. (2)
6.9.2
- A plug in is software that adds a specific feature/functionality ✔ to an existing software. (1)
- If this device supports plug-ins, a program from the web can be used to play embedded audio and video files without the need for a dedicated media player. ✔ (1)
6.9.3 Any TWO ✔✔
- Movement
- Sound
- Light (2)
6.9.4 Artificial Intelligence ✔ (1)
TOTAL SECTION F: 38
GRAND TOTAL: 150