INFORMATION TECHNOLOGY GRADE 12 PAPER 2 QUESTIONS - NSC PAST PAPERS AND MEMOS SEPTEMBER 2017
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINFORMATION TECHNOLOGY
GRADE 12
PAPER 2
NSC PAST PAPERS AND MEMOS
SEPTEMBER 2017
INSTRUCTIONS AND INFORMATION
- This paper consists of SIX sections:
SECTION A: Short questions (15)
SECTION B: System Technologies (24)
SECTION C: Communication and Network Technologies (25)
SECTION D: Data and Information Management (24)
SECTION E: Solution Development (21)
SECTION F: Integrated Scenario (41) - Read all the questions carefully.
- Answer ALL the questions.
- The mark allocation generally gives an indication of the number of facts/reasons required.
- Number the answers correctly according to the numbering system used in this question paper.
- Write neatly and legibly.
QUESTIONS
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1 Give ONE word/term for each of the following descriptions. Write only the word/term next to the question number (1.1.1–1.1.10) in your ANSWER BOOK.
1.1.1 The protocol that defines how webpages and their content are transferred across the Web (1)
1.1.2 A collection of 8 bits (1)
1.1.3 Collection of programs designed to use administrator rights to gain control of a computer for dangerous purposes (1)
1.1.4 An update that can be downloaded to fix a specific bug in software (1)
1.1.5 The electronic equivalent to junk mail (1)
1.1.6 A part of a larger program that runs independently but simultaneously with other parts of the same program (1)
1.1.7 The layout of the physical connection of the computers in a network (1)
1.1.8 The posting of short text entries (140 characters or less) usually via a cellphone or smartphone. (1)
1.1.9 The latest generation of cellular communication technology (1)
1.1.10 The total amount of data that can be transferred from one point to another in a given period of time (1)
1.2 Various options are given as possible answers to the following questions. Choose the answer and write only the letter (A–D) next to the question number (1.2.1–1.2.5), for example 1.2.6 D.
1.2.1 Copyright law is NOT broken when you ...
- copy music from your friend's computer to your mp3 player.
- borrow a CD from a friend and copy it to your computer.
- find and download music from the Internet.
- copy your own CD to play on your mp3 player. (1)
1.2.2 An algorithm is ...
- a set of instructions written in a computer language that will solve a problem.
- a sequence of logical steps that will solve a problem.
- the source code of a computer program that will solve a problem.
- a sequence of plans for the developing and selling of a computer program. (1)
1.2.3 A cookie is a(n) …
- binary file that allows a program to run.
- HTML file that contains Internet settings.
- text file that stores information relating to websites.
- file that stores information about a database table. (1)
1.2.4 Which ONE of the following refers to an encryption process used to authenticate the identity of the sender of an e-mail message?
- Digital certificate
- Digital divide
- Digital handshake
- Digital signature (1)
1.2.5 Which ONE of the following is NOT a suitable application of Bluetooth technology?
- Wireless communication between a mobile phone and a hands free headset
- Wireless communication between PCs in different rooms.
- Wireless communication with PC input and output devices
- Wireless communication between mobile devices which are in line of sight. (1)
TOTAL SECTION A: 15
SECTION B: SYSTEMS TECHNOLOGIES
QUESTION 2
Your friends have been telling you to replace your computer for the past year because of its slow performance. However you are considering upgrading it and have been doing a lot of research about the advantages and disadvantages of upgrading.
2.1 You have been advised to replace the RAM of the computer in order to enhance its performance.
2.1.1 How will you ensure that the new RAM is compatible with the current motherboard? (1)
2.1.2 One of your friends is of the opinion that, if there was enough virtual memory, there is no need to upgrade the RAM.
- Explain what virtual memory is. (2)
- Explain why virtual memory will not be the solution to improve performance. (1)
2.1.3 The statement, “Upgrading RAM means more cache memory is available”, was made.
- Explain the role cache memory plays in the performance of a CPU. (2)
- Give THREE reasons why this statement is NOT true. (3)
2.2 Most of the peripheral devices required are connected to the computer using USB ports. Standard drivers are used.
2.2.1 Write down the full term for the acronym USB. (1)
2.2.2 Name ONE port other than the USB port, that can be used to connect a digital video camera to a computer. (1)
2.2.3 Define a driver in the context of computing. (2)
2.2.4 What is meant by the term standard driver? (1)
2.2.5 Name ONE device that makes use of a standard driver. (1)
2.3 It is suggested that you can buy a laptop to do everything that your desktop computer can do.
2.3.1 Do you agree with this statement? Motivate you answer. (1)
2.3.2 List TWO advantages and TWO disadvantages of a laptop. (4)
2.4 The CPU is considered as the brain of the computer system.
2.4.1 State the two main aspects of the CPU that must be considered because they have a direct influence on the system performance. (2)
2.4.2 The CPU sometimes overheats. List TWO ways in which overheating can be prevented. (2)
TOTAL SECTION B: 24
SECTION C: COMMUNICATION AND NETWORK TECHNOLOGIES
QUESTION 3
Your friends encourage you to buy another computer by saying that they can be networked together with your tablet, phone, printer and even your work computer.
3.1 You will need an Internet connection.
3.1.1 Name ONE type of broadband Internet connection that could be used. (1)
3.1.2 State TWO advantages of the type of broadband connection mentioned in QUESTION 3.1.1. (2)
3.2 A router will also be a requirement for your network setup.
3.2.1 Briefly explain why a router is able to manage the bandwidth of a network efficiently. (2)
3.2.2 State TWO other functions of a router. (2)
3.3 You will need to setup a wireless network for your devices.
3.3.1 Name ONE advantage of a wireless network. (1)
3.3.2 List TWO disadvantages of a wireless network. (2)
3.4 You mention to your friends that you are going to need a website for your business and then optimise it for popular search engines.
3.4.1 State what a search engine does. (1)
3.4.2 Explain the purpose of search engine optimisation. (2)
3.4.3 List THREE ways in which search engine companies try to improve the searching of content on the Web. (3)
3.4.4 Describe ONE of the ways stated in QUESTION 3.4.3. (2)
3.5 You discover that you will need to use HTML, JavaScript and Cascading Style Sheets to make your website responsive.
3.5.1 Differentiate between HTML and JavaScript. (2)
3.5.2 You might also need a server side scripting language. Give TWO examples of server side programming languages. (2)
3.5.3 Indicate why one would prefer server side technology over the other technologies. (2)
3.5.4 Give ONE advantage of using Cascading Style Sheets. (1)
TOTAL SECTION C: 25
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
During some weekends you run a small business at the regular local open market. Your business involves selling second hand items that your friends and customers bring. You add a 30% mark-up to the value of all the goods that you sell, as profit. To keep track of sales and stock, you decide to use the MS Access database system.
4.1 One of your friends suggests that you hire a database administrator to help you create the proposed relational database.
4.1.1 List THREE duties that are carried out by a database administrator. (3)
4.1.2 What is a relational database? (1)
4.2 In order to design the database, you must identify the possible sources of data.
4.2.1 List TWO possible sources of data for your database. (2)
4.2.2 What is involved in data maintenance? (1)
4.3 Whilst designing the database, the following table called Stock_DetailsTB structure is proposed for your database. 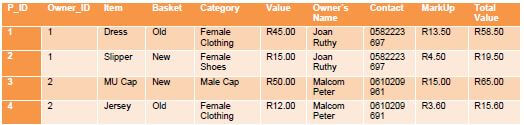
4.3.1 You will need to normalise this table. What is the general aim of normalisation? (1)
4.3.2 Which field would you regard as redundant? Motivate your answer. (2)
4.3.3 Use a diagram to split the databases into TWO tables. Clearly indicate the table names, primary and foreign keys as well as the relationship between the tables. (6)
4.4 In order to create queries to the table Stock_DetailsTB, SQL is used.
4.4.1 Write a statement to show all the information from the table arranged in ascending order according to the price. (2)
4.4.2 Write a statement that will delete the Item in the old basket called Dress. (3)
4.4.3 Malcolm Peter's phone number has changed. Change the contact number to 0715624117. (3)
TOTAL SECTION D: 24
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
You are organising a small LAN event. The participants will have to complete a registration form. The information will be used to keep track of their results as well as food orders. Access codes will be needed to gain access to the premises where the event will take place.
5.1 To create the access code the user will have to enter their name and surname. All the vowels and spaces need to be removed. The first and last character must be uppercase and a '#' must be added at the end. Write an algorithm to create the access code. (7)
5.2 The following UML diagram is given. Answer the following questions.
objLAN |
- Name |
+ constructor create |
5.2.1 What does the '-' indicate? (1)
5.2.2 What is the difference between a mutator and accessor method? Give an example of each making use of objLAN. (4)
5.2.3 What is the purpose of a constructor? (2)
5.2.4 What is the purpose of a tostring method? (1)
5.3 Understanding a flow chart is seen as basic knowledge a programmer should have. Another concept that is crucial is the ability to use a trace table to track the input, processing and the expected output.
Put your skills and knowledge to the test, by completing the trace table for the following flow chart.
Draw a trace table with the following headings:
The input values are the following:
1.8; 2.0; 1.0; 1.3; 1.0; 2.5; 2.0; 1.3; 1.8; 1.3; -1 (6)
TOTAL SECTION E: 21
SECTION F: INTEGRATED SCENARIO
QUESTION 6
Keeping track of goods, setting up a network system and identifying the appropriate software systems, is required for the success of your small second-hand weekend business.
6.1 It has been suggested by a trusted friend that in order to keep the stock safe at the stall, RFID tags must be attached to the clothing.
6.1.1 List AND explain the TWO parts that make up the RFID system. (4)
6.1.2 Differentiate between a passive and active RFID tag. (4)
6.1.3 Motivate whether it is advisable to use RFID tags for your stall management. (2)
6.2 In an attempt to effectively market your business, social networks are suggested.
6.2.1 Name TWO social networking sites that you could use to market your products. (2)
6.2.2 Social network sites also have a negative effect on concentration and productivity. Describe TWO such ways in which it can happen. (2)
6.2.3 Explain social engineering and how it can be used negatively in society. (2)
6.2.4 As you market your business to groups on the social networks, why is it important that you be careful of what you publish? (1)
6.3 A colleague has developed an app that you are using to keep track of your stock. Most of the information is on the server and one day he sends you a message to inform you that the site has been attacked, but he is working on solving the problem.
6.3.1 He mentions that it is a Distributed Denial of Service (DDS) attack. Explain what this is and how it works. (2)
6.3.2 He also mentions something about discovering the botnets used for this attack. Describe what a botnet does. (2)
6.3.3 Your cousin insists that this problem was caused by a troll on the network. Argue why this cannot be so. (2)
6.3.4 Suggest a possible name for the type of people who attack websites with malicious intent. (1)
6.4 In order to safely check bank balances and make payments online the bank’s website makes use of SSL encryption and decryption technology.
6.4.1 What does SSL stand for? (1)
6.4.2 What is meant by the term encryption? (1)
6.4.3 SSL uses a special form of encryption called Public Key Encryption. Briefly explain how a secure connection between a server and a browser is established using this method. (4)
6.5 Cloud computing has become very popular since the development and popularity of the internet and you have been considering it seriously.
Popular examples of these are online storage, online backup and file syncing services.
6.5.1 Define the term cloud computing. (2)
6.5.2 Differentiate between online file storage and online backup AND give an example of each. (4)
6.5.3 One of your friends believes that file syncing is the same as a backup service. State whether you AGREE or DO NOT AGREE with him. Substantiate your answer. (3)
6.5.4 Most ‘cloud computing’ apps have a local front end. What does the term local front end mean? (2)
TOTAL SECTION F: 41
GRAND TOTAL: 150