INFORMATION TECHNOLOGY GRADE 12 PAPER 2 MEMORANDUM - NSC PAST PAPERS AND MEMOS SEPTEMBER 2017
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINFORMATION TECHNOLOGY
GRADE 12
PAPER 2
NSC PAST PAPERS AND MEMOS
SEPTEMBER 2017
MEMORANDUM
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1
1.1.1 HTTP ✔ (1)
1.1.2 Byte ✔ (1)
1.1.3 Rootkit ✔ (1)
1.1.4 Patch ✔ (1)
1.1.5 SPAM ✔ (1)
1.1.6 Thread ✔ (Accept multithreading) (1)
1.1.7 Topology ✔ (1)
1.1.8 Microblogging ✔ (Accept tweeting) (1)
1.1.9 4G/LTE ✔ (1)
1.1.10 Bandwidth ✔ (1)
1.2
1.2.1 D ✔ copy your own CD to play on your mp3 player. (1)
1.2.2 B ✔ a sequence of logical steps that will solve a problem. (1)
1.2.3 C ✔ text file that stores information relating to websites. (1)
1.2.4 D ✔ Digital signature (1)
1.2.5 B ✔ Wireless communication between PCs in a different rooms. (1)
TOTAL SECTION A: 15
SECTION B: SYSTEMS TECHNOLOGIES
QUESTION 2
2.1
2.1.1 Any ONE fact ✔
- It must be of the same size (number of pins)/Must fit into the slots on the motherboard.
- The speed of the RAM must be compatible with the motherboard/FSB/System bus.
NOTE:
Also accept any mention of motherboard compatibility/checking/ comparing the specifications of the RAM. (1)
2.1.2
- The operating system’s use of secondary storage ✔ (hard drive) space as memory ✔ (temporary or simulated or additional RAM). (2)
- Any ONE fact why virtual memory is not the solution. ✔
- Virtual memory is slow/using hard disk space as memory slows down the performance
- Thrashing may occur
- To be effective the need for a large amount of secondary storage (hard disk space) arises (1)
2.1.3
- Any TWO correct facts about cache ✔✔
TWO MARKS FOR:- Instructions/data probably needed next by the CPU are placed in the cache memory which reduced time lost while waiting for instructions/data from the RAM and as a result it improves the performance of the CPU.
ONE MARK EACH FOR:- Cache memory is situated inside the CPU or close by.
- Cache faster type of memory – can feed the CPU with instructions at a faster rate.
- Instructions/data probably needed next by the CPU are placed in the cache memory. (2)
- Instructions/data probably needed next by the CPU are placed in the cache memory which reduced time lost while waiting for instructions/data from the RAM and as a result it improves the performance of the CPU.
-
- RAM and cache are different ✔ types of memory (DRAM and SRAM).
- Cache memory is found in the CPU; RAM on the motherboard. ✔
- Upgrading RAM means replacing DIMMs while upgrading cache means replacing the CPU. ✔ (3)
2.2
2.2.1 Universal Serial Bus ✔ (1)
2.2.2 Accept any ONE of the following: ✔
- Firewire (Windows)
- Thunderbolt (Mac)
- HDMI (1)
2.2.3
- Program ✔ that tells an operating system how to communicate with a specific device. ✔
ALSO ACCEPT: - Software designed to control a piece of hardware. (2)
2.2.4 Standard driver: Any ONE correct fact ✔
- Is already part of the operating system
- No need to load extra drivers (1)
2.2.5 Any ONE device that connects to USB port that can make use of standard/generic driver. ✔
Examples of devices:
- Mouse.
- Keyboard.
- External storage device (e.g. hard drive/flashdisk).
- Printer / scanner / camera (1)
2.3
2.3.1 Yes / No and a valid reason to justify their answer. ✔ (1)
2.3.2 Any TWO advantages:
- Powerful CPU ✔
- Full scale operating system ✔
- Expandable
DO NOT ACCEPT MOBILITY
Any TWO disadvantages:
- Size ✔
- Battery life ✔
- Not always on
- No built in cellular data (2 + 2) (4)
2.4
2.4.1 Speed (GHz) ✔ and Cores ✔ (2)
2.4.2 Any TWO correct facts about preventing overheating ✔✔
- Large heat sink on the CPU/North Bridge chipset.
- Using thermal paste
- Heat conductive plate over system bus.
- Additional cooling fans in case.
- Alternative cooling systems – any sensible example. (2)
[24]
QUESTION 3
3.1
3.1.1 Accept any ONE: ✔
- 3G/LTE
- ADSL
- WiMAX (1)
3.1.2 Accept any TWO advantages of the connection mentioned in QUESTION 3.1.1 ✔✔
3G/LTE
- Widely available in South African cities
- Allows mobile devices an Internet connection
- Fast data transfer rate
- Only pay for data being downloaded/uploaded
ADSL
- Stable
- Fast data transfer rate
- High bandwidth available/capped bandwidth
- Simultaneous voice and data
- Low latency
WiMAX
- Fast data transfer rate
- Can provide broadband wireless access for up to 50 km for fixed stations and 15 km for mobile stations (2)
3.2
3.2.1 A router manages the bandwidth because it is able to inspect the data packets as they arrive and determine the correct destination ✔ of the data and forward it accordingly. ✔ (2)
3.2.2 Accept any TWO other capabilities of a router: ✔✔
- Connect different network types together
- Ensures the safe transfer of data between networks
- Mainly used to connect LAN’s into a WAN / Used to connect networks to the Internet
- Routers can also be used for port-forwarding (2)
3.3
3.3.1 Any ONE of the following: ✔
- No wires
- Mobility
- Easy to setup (1)
3.3.2 Any TWO of the following: ✔✔
- Limited range
- Can be hacked easily
- Interference
- Slower than wired network (2)
3.4
3.4.1 A search engine works as an information locator. ✔ It uses keywords or phrases entered by the user when looking for information. (1)
3.4.2 It is a technology/strategy ✔ used to obtain a high ranking placement in the search results page of a search engine. ✔ (2)
3.4.3 Any THREE of: ✔✔✔
- Profiled or customised searches
- Context-aware searches
- Mediated searches
- Semantic searches (3)
3.4.4 Any ONE explanation: ✔✔
- Profiled or customised searches – a technique used to customise your search results, matching them to advertisements that you are most likely to respond to.
- Context-aware searches – here the context or your current interests taken from your web surfing history is used in making search results relevant.
- Mediated searches – here third party software/humans assist in the process of organising the content.
- Semantic searched – for the future, it will allow searches to happen automatically, using metadata, contextual information to come up with results. (2)
3.5
3.5.1
- HTML – website document formatting language designed for browser ✔
- JavaScript – a scripting language designed to run in a web browser. ✔ (2)
3.5.2 Any TWO of: ✔✔
- Perl
- Ruby
- ASP.NET
- Python
- PHP (2)
3.5.3 Server side scripting makes dynamic creation of webpages possible, ✔ whilst connecting easily to a database. ✔ (2)
3.5.4 Any ONE of: ✔
- Easy formatting of text
- Consistent formatting of text (1)
[25]
QUESTION 4
4.1
4.1.1 Any THREE of: ✔✔✔
- Management
- Maintenance
- Security access rights
- Backup
- Installing software
- Configuring software (3)
4.1.2 A relational database that contains many tables linked together by relations. ✔ (1)
4.2
4.2.1 Any TWO of: ✔✔
- Existing documents
- Existing workflows
- Business plan (2)
4.2.2 Data maintenance involves keeping information up to date. ✔ (1)
4.3
4.3.1 Normalisation refers to the process of organising a database into separate tables in such a way as to avoid the duplication of data and also update/deletion anomalies. ✔ (1)
4.3.2 Markup or the Total Value fields ✔ as they can automatically be calculated when needed using a calculated field. ✔ (2)
4.3.3 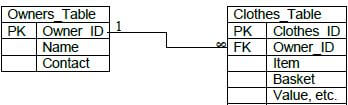
Table Names ✔✔
Primary Keys ✔✔
Foreign Key ✔
Relationship ✔ (6)
4.4
4.4.1 SELECT * FROM Stock_DetailsTB ✔Order BY TotalValue ✔ (2)
4.4.2 DELETE ✔ From Stock_DetailsTB✔ WHERE Item=’Dress’ ✔ (3)
4.4.3 UPDATE Stock_DetailsTB ✔ SET Contact = '0715624117' ✔ WHERE Owner's Name = 'Malcolm Peter'✔ (3)
[24]
QUESTION 5
5.1
Get the name and surname ✔
Initialise a blank string ✔
Get the length of name and surname ✔
Loop through the entire string ✔
If the character is not a vowel or a space then add to the blank string ✔
Change the first and last character to a capital letter ✔
Add a # to the end ✔ (7)
5.2
5.2.1 Indicates that the attributes are private fields ✔ (1)
5.2.2 Accessor methods are used to return the contents of an object's fields ✔ e.g. GetTeamName, ✔GetGender, GetDOB,
Mutator methods are used to change the contents of an object's fields ✔ e.g. CalculateCost ✔ (4)
5.2.3 A constructor instantiates the object ✔and initialises the fields of the object. ✔ (2)
5.2.4 Compiles the objects attributes into a single string variable ✔ (1)
5.3
One mark per correct column. (6)
[21]
SECTION F: INTEGRATED SCENARIO
QUESTION 6
6.1
6.1.1 RFID tag ✔
- Contains the antenna, the circuit and microchip. ✔
RFID reader ✔
- The reader reads the radio signal sent by the tags. ✔ (4)
6.1.2
- Passive RFID tags, receive all their power from the reader. ✔ These tags do nothing until they enter into the magnetic field of the reader. ✔
- Active RFID tags, receive power from on-board batteries ✔ which allows them to communicate over long distances. ✔ (4)
6.1.3 RFID tags would not be advisable ✔ since it is a stall and people do not have a designated entry or exit point to check for the tags. ✔ (2)
6.2
6.2.1 Any TWO of: ✔✔
- Myspace
- Any other relevant answer. (2)
6.2.2
- Constant interruptions prevent you from focusing your attention on whatever task you are supposed to be doing. ✔
- Social networking can consume several hours of your time each day. ✔ (2)
6.2.3 Social engineering refers to ‘conning’ or tricking a person into giving out information willingly. ✔ This often includes sensitive information such as passwords or other information that can be used to commit identity theft. ✔ (2)
6.2.4 Whatever you publish is immediately public and ‘vulnerable’ in terms of being shared. ✔
ACCEPT ALSO:
Multiple people have access to that information – especially if the group does not have a controlled or limited membership. (1)
6.3
6.3.1 Distributed Denial of Service in an attack that make a website unavailable ✔ by the use of thousands or millions of computers to request data from the site at the same time. The servers become overloaded, unresponsive and effectively unavailable to everyone. ✔ (2)
6.3.2 A botnet is a remotely controlled zombie PC infected with malware ✔ that enables criminals to use it for launching DOS attacks, or sending spam. ✔ (2)
6.3.3 Trolling is sowing discord on the Internet by starting arguments or upsetting people, by posting inflammatory, extraneous, or off topic messages in an online community (such as a newsgroup, forum, chat room, or blog) with the deliberate intent of provoking the readers. ✔
Therefore, one cannot cause a DOS by doing this. ✔ (2)
6.3.4 ONE of: ✔
- Hacker
- Scriptkiddie
- Cyber-criminal
- Spammer etc. (1)
6.4
6.4.1 Secure Socket Layer ✔ (1)
6.4.2 Encryption is when clear and easy to read data is scrambled to protect it and make it unreadable. ✔ (1)
6.4.3
- The browser connects to the server using https and requests a secure connection✔ The server sends the browser its public key and its certificate to prove who it is. ✔
- The browser generates the secret key that will only last for the duration of the communication session, encrypts the key using the server’s public key and sends it to the server. ✔
- The server decrypts the secret key and now both has the secret key that they will use temporarily for the duration of this communication session. ✔ (4)
6.5
6.5.1 The use of resources offered as services over the Internet ✔ and shared between many users, including online file storage services and the running of programs. ✔ (2)
6.5.2 Online file Storage – Storing files on the internet, which can be accessed from multiple devices and shared with others ✔
Examples: Any ONE ✔
- OneDrive
- Dropbox
- iCloud
Online Backup – Used to backup data that you only access when disaster strikes, which may include your system settings. ✔
Examples: Any ONE✔
- Carbonite
- Acronis
- Crashplan (4)
6.5.3 DISAGREE ✔
- Syncing services do not offer an incremental structure ✔ and the security of a proper online backup service. ✔
OR - Backup services make a copy of the files. ✔
Syncing services automatically updates and make changes to the cloud storage so that it mirrors the hard drive. ✔ (3)
6.5.4 There is an application installed on the device ✔that runs to create the user interface and so reduce the amount of data that needs to be transferred. ✔ (2)
[41]
TOTAL SECTION F: 41
GRAND TOTAL: 150