COMPUTER APPLICATION TECHNOLOGY GRADE 12 PAPER 2 QUESTIONS - NSC PAST PAPERS AND MEMOS NOVEMBER 2017
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupCOMPUTER APPLICATIONS TECHNOLOGY PAPER 2
GRADE 12
NOVEMBER 2017
NATIONAL SENIOR CERTIFICATE
INSTRUCTIONS AND INFORMATION
- This question paper consists of:
SECTION A (25 marks)
SECTION B (75 marks)
SECTION C (50 marks) - Answer ALL the questions.
- Number the answers correctly according to the numbering system used in this question paper.
- Start EACH question on a NEW page.
- Do NOT write in the right-hand margin of the ANSWER BOOK.
- Leave a line after EACH subquestion.
- In general, a mark is allocated per fact. A 2-mark question would therefore require TWO facts, et cetera.
- Write neatly and legibly.
SECTION A
QUESTION 1: MULTIPLE-CHOICE QUESTIONS
Various options are provided as possible answers to the following questions. Choose the answer and write only the letter (A–D) next to the question number (1.1.1–1.1.10) in the ANSWER BOOK, for example 1.1.11 D.
1.1 Which hardware device can create electronic copies of documents by capturing an image?
- Printer
- Scanner
- Stylus
- Monitor (1)
1.2 Which CPU in the following list is the best choice for video-editing?
- i3
- i7
- Pentium
- Celeron (1)
1.3 Which storage device will be more likely to break when it is accidentally dropped?
- HDD
- USB flash disk
- SSD
- MicroSD card (1)
1.4 Non-responding programs are best closed using ...
- Disk Cleanup.
- System Restore.
- Task Manager.
- Disk Defragmenter. (1)
1.5 If the display on a monitor appears to be the wrong size or out of focus, it may be corrected by changing the … of the monitor.
- position
- brightness
- resolution
- contrast (1)
1.6 The function =SUM(A1:B2) will add values in …
- all cells in rows 1 and 2.
- cells A1, A2, B1 and B2.
- cells B1 and B2.
- all cells in columns A and B. (1)
1.7 Using a wizard to get data from a CSV file into an application is called …
- exporting.
- spooling.
- importing.
- compressing. (1)
1.8 Which ONE of the following devices in a LAN is more likely to have a built-in firewall?
- Printer
- Router
- Mobile client
- Workstation (1)
1.9 A pattern of change in data over time is best described by the term …
- trend.
- process.
- thread.
- graph. (1)
1.10 Which ONE of the following processes is useful when analysing data?
- Recycling
- Cleaning
- Archiving
- Comparing (1)
[10]
QUESTION 2: MATCHING ITEMS
Choose a term/concept from COLUMN B that matches the description in COLUMN A. Write only the letter (A–T) next to the question number (2.1–2.10) in the ANSWER BOOK, for example 2.11 U.
| COLUMN A | COLUMN B |
| 2.1 Unit of measurement applicable to bandwidth 2.2 An example of a commonly used aspect ratio 2.3 A stage in the information processing cycle 2.4 A technology used in devices for paralysed users 2.5 The reason why a computer screen switches off after a set time 2.6 A medium for a fast and stable Internet connection 2.7 Compression of files for long-term storage 2.8 A malware program that poses as a useful application 2.9 Cache memory is found here 2.10 A monthly limit to data used over an Internet connection |
|
(10 x 1) [10]
QUESTION 3: TRUE/FALSE ITEMS
Indicate whether the following statements are TRUE or FALSE. Write 'true' or 'false' next to the question number (3.1–3.5) in the ANSWER BOOK. Correct the statement if it is FALSE. Change the underlined word(s) to make the statement TRUE. (You may not simply use the word 'NOT' to change the statement. NO mark will be awarded if only FALSE is written down.)
EXAMPLES:
| QUESTION | ANSWER |
| Google is the world's most popular search engine. | True |
| An NIC has slots for hardware components, such as the CPU. | False – motherboard |
3.1 An asterisk used in search criteria is called a wild card. (1)
3.2 Linux is a proprietary operating system. (1)
3.3 Formatting a USB flash disk will back up any data stored on it. (1)
3.4 Grouping can be used to automatically highlight specific values in a spreadsheet according to a rule. (1)
3.5 The spreadsheet functions LEFT and RIGHT can be replaced by the function CONCATENATE to get the same result. (1)
[5]
TOTAL SECTION A: 25
SECTION B
QUESTION 4: SYSTEMS TECHNOLOGIES
4.1 State TWO disadvantages of wireless keyboards (2)
4.2 State TWO ways in which the GUI of a mobile app differs from the desktop version of the same app. (2)
4.3 What kind of desktop computer is a result of convergence? (1)
4.4 Suggest TWO ways to fix a mouse pointer that moves in an unpredictable way, without replacing the mouse. (2)
4.5 Give TWO reasons why many modern notebooks no longer include an optical drive. (2)
4.6 State TWO uses of NFC on smartphones. (2)
4.7 What should a user do when the trial period of a software product has expired? (1)
4.8 PDF is a popular file format.
4.8.1 State ONE advantage of using the PDF file format. (1)
4.8.2 How would you convert an office suite document to PDF? (1)
4.8.3 You receive two documents in PDF format. Both are one page long.
Explain why they have different file sizes AND why it is not possible to do a text search in one of the two. (2)
4.9 Explain TWO ways to find a program on your computer, OTHER than using the Start Menu. (2)
4.10 Explain how a POS device finds the price of a product after it is scanned. (2)
4.11 Name TWO features to look for in laptop computer hardware that will make upgrades easier in future. (2)
4.12 Virtual reality (VR) equipment is becoming more affordable.
4.12.1 Name TWO pieces of equipment one would need for VR. (2)
4.12.2 State ONE way in which VR can be used. (1)
[25]
QUESTION 5: INTERNET AND NETWORK TECHNOLOGIES
5.1 Name a device that connects a LAN to a WAN. (1)
5.2 State TWO disadvantages of using Bluetooth to connect devices in a home area network (HAN). (2)
5.3 Give TWO reasons why a school may not want to use cloud storage for storing large volumes of data. (2)
5.4 Name ONE type of technology that uses radio waves for data transfer. (1)
5.5 What is the function of a network switch? (1)
5.6 User access rights can limit what a user can do on a network.
Give TWO examples of access rights that restrict a user on a network. (2)
5.7 Which software is required to access a company's intranet? (1)
5.8 The Internet is increasingly being used to make voice calls.
5.8.1 Give an example of a program that supports VoIP, other than Skype. (1)
5.8.2 Why is it not recommended to use VoIP for emergency calls? (1)
5.8.3 Why would a user reduce the quality of VoIP calls? (1)
5.9 Suggest TWO ways in which a user can listen to music on a smartphone that has no headphone jack (port). (2)
[15]
QUESTION 6: INFORMATION MANAGEMENT
6.1 Why would an author's name not be enough to consider a source trustworthy? (1)
6.2 An Internet search returned a link from an advertiser at the top of the set of results.
Give a reason why it may not be a good idea to follow this link. (1)
6.3 The graphs below represent the change in male and female learner numbers over a period of time.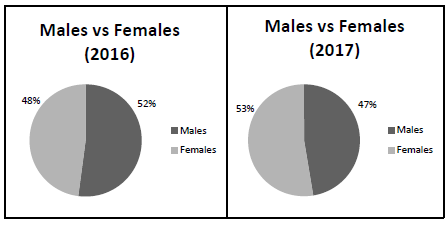
6.3.1 What conclusion can be made based on the data above? (1)
6.3.2 What type of graph would you use to combine the information in the graphs above? (1)
6.4 How does the number of respondents affect the outcome of a survey? (1)
6.5 Give ONE reason why the values in the Name column and Marks column in the data below were not sorted correctly.
| Original data |  | Sorted data | ||||
| Surname | Name | Marks | Surname | Name | Marks | |
| Tlou | Lerato | 54 | Harms | Frikkie | 54 | |
| Hlongwana | Bulisa | 89 | Hlongwana | Bulisa | 89 | |
| Rhadebe | Julius | 28 | Howell | Liam | 28 | |
| Harms | Frikkie | 17 | Rhadebe | Julius | 17 | |
| Howell | Liam | 43 | Tlou | Lerato | 43 | |
6.6 Identify THREE problems in the wizard below that will affect the quality of data when the import process is completed. 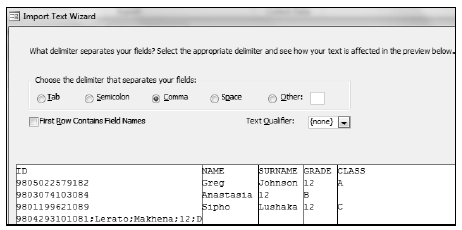 (3)
(3)
[10]
QUESTION 7: SOCIAL IMPLICATIONS
7.1 Name the computer crime that has to do with posting false information/ accusations about another person online. (1)
7.2 Suggest TWO rules for an acceptable use policy (AUP) in a school computer centre that has Internet access. (2)
7.3 While installing software, you were not required to enter a product key.
Give TWO reasons why this occurred. (2)
7.4 A company stores the personal information of its clients.
Suggest TWO guidelines for the company to ethically manage client data. (2)
7.5 Study the picture below and answer the questions that follow.
NOTE: Assume that BANKZA is the name of a legitimate South African bank.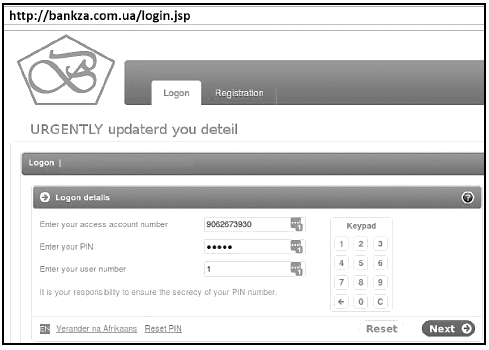
7.5.1 Identify the type of scam represented in the picture above. (1)
7.5.2 State TWO ways in which a user can identify this as a scam. (2)
[10]
QUESTION 8: SOLUTION DEVELOPMENT
8.1 Why would one turn on the formatting symbols, as is done in the screenshot below? ![]() (1)
(1)
8.2 Look at the screenshot of a table below and answer the questions that follow.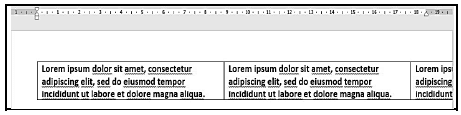
8.2.1 What is the current width of the page without the margins? (1)
8.2.2 Suggest a way to reduce the number of cells in the table WITHOUT deleting any text. (1)
8.2.3 State TWO general ways to configure the spell checker to get rid of the automatic underline. (2)
8.2.4 The table in the screenshot above is too wide to display correctly.
Suggest ONE way to make the table fit on the page. (1)
8.3 The ACTUAL size of an image called 'google.jpg' is 1080x900.
This image should display smaller when the following HTML code is executed:
<img src="/google.jpg" width="540" height="50" />
8.3.1 How does the image size specified in the HTML code affect the original size of the image saved on a disk? (1)
8.3.2 Why does the displayed image appear distorted? (1)
8.3.3 Comment on the accessibility of the image in the web page for blind users. Motivate your answer. (2)
8.4 Look at the screenshot of a spreadsheet below and answer the questions that follow.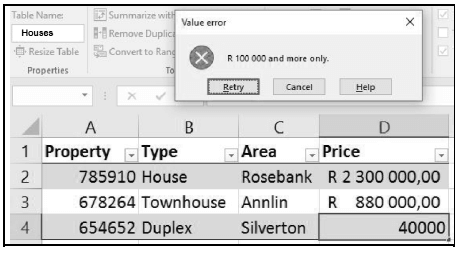
8.4.1 Give the term for the feature that was applied to give the 'Value error' dialog as a result. (1)
8.4.2 What is the purpose of the dropdown buttons next to the column headings in the image? (1)
8.4.3 A named range has been defined in the spreadsheet above.
What is this named range called? (1)
8.4.4 You need to export the data in the spreadsheet to a database.
Which field would you choose as a primary key? Explain the reason for your choice. (2)
[15]
TOTAL SECTION B: 75
SECTION C: INTEGRATED SCENARIO
QUESTION 9
The local municipality asked you to use your knowledge of ICTs to help them implement an effective water-saving campaign.
9.1 They want to create an information booklet with images for the campaign.
9.1.1 Name an application that can be used to design such a booklet. (1)
9.1.2 Why would A2 size paper be a bad choice for printing the booklet? (1)
9.1.3 Suggest TWO ways to save ink when printing a project. (2)
9.1.4 Recommend a cost-effective alternative to printing to distribute a large number of booklets. (1)
9.1.5 A digital camera will be used to take photographs for the booklet.
Name TWO types of storage media one can use with the digital camera for saving the photographs. (2)
9.2 The municipality will publish an online list of citizens who saved or wasted the most water for the month.
9.2.1 Which TWO objects in a database program could be used to enter water usage by each customer? (2)
9.2.2 Identify a field in the list below in which the same data has to be entered repeatedly AND suggest a property that one can set to avoid manual capturing of duplicate data.
| Customer_ID | Usage_Period | Water_Used |
(2)
9.2.3 Which database technique could the municipality use to determine the top ten water savers? (1)
9.2.4 Which website feature could provide municipal customers with automatic updates each time the top ten list changes? (1)
9.2.5 Discuss TWO implications of posting the names of the top ten offenders online. (2)
9.2.6 Name TWO design principles that would make the municipal website easy to use. (2)
9.2.7 How can a hacker force the municipal website to go offline? (1)
9.2.8 Explain how it is possible that the website is attacked from a customer's computer, without the customer's knowledge. (2)
9.3 The municipality wants to conduct a water awareness survey.
9.3.1 State TWO problems regarding the use of the question below that appeared in the survey.
| How do you save water at home? __________________________ __________________________ __________________________ |
(2)
9.3.2 State TWO methods to conduct this water awareness survey. (2)
9.3.3 What are the implications for the survey findings if the same people can submit more than one survey response? (1)
[25]
QUESTION 10
Your municipality has formed a committee to deal with disaster management.
10.1 Mobile emergency officers will receive ICT equipment.
10.1.1 What Internet connection should the officers get? (1)
10.1.2 Give TWO reasons for using an SSD rather than a traditional hard drive on laptop computers for the officers. (2)
10.1.3 Give a specification of the laptop computer screen that will affect its use in sunlight. (1)
10.1.4 What popular instant messaging service can be used to create groups for sharing disaster alerts for the area? (1)
10.2 Local government wants to develop an app that people can use to report an incident as soon as it happens. They will rely on the community to fund the project.
10.2.1 State TWO disadvantages of crowd-funding for the individual who contributes money. (2)
10.2.2 What technology would citizens use to determine the precise location of a natural disaster they may witness? (1)
10.2.3 What information does a pin on a map provide in a mapping service app such as Google Maps? (1)
10.3 People may have to leave their homes when disaster strikes. They will be accommodated in community halls or churches.
10.3.1 State an advantage of using RFID tags for people that have been displaced as a result of a disaster. (1)
10.3.2 Biometric devices will be installed at the different venues.
Give TWO examples of biometric devices. (2)
10.3.3 State TWO ways in which having a user account, such as an account with Google, Apple or Microsoft, can be helpful when a smartphone is lost. (2)
10.3.4 What service can the municipality set up at the venues to provide free wireless Internet access to the people accommodated there? (1)
10.3.5 State TWO precautions one should take when using a public computer. (2)
10.4 The following message appears on a computer that was made available in one of the venues:
| We're sorry, but we encrypted (scrambled) ALL the files on your computer. To make your computer work again, please pay 3 Bitcoin to the provided account. You are helping the victims of hunger by paying this amount. We thank you. |
10.4.1 What type of software is to blame for the message above? (1)
10.4.2 What is Bitcoin? (1)
10.4.3 State an advantage of being paid in Bitcoin for the authors of the message. (1)
10.4.4 What action can the municipal IT department take to react to this threat? (1)
10.5 An example spreadsheet with natural disaster survivor details was drafted as follows: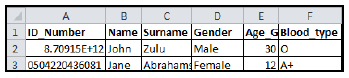
10.5.1 Why is the ID number in cell A2 displayed incorrectly? (1)
10.5.2 The following function will be used to calculate the average age of the survivors:
=AVERAGE(D2:D200)
Why would it not give the average age of the survivors? (1)
10.5.3 State TWO ways to fully display the word 'Age_Group' in cell E1. (2)
[25]
TOTAL SECTION C: 50
GRAND TOTAL: 150