Information Technology P2 Grade 12 Questions - NSC Exams Past Papers and Memos September 2019 Preparatory Examinations
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINSTRUCTIONS AND INFORMATION
- This paper consists of SIX sections:
SECTION A: Short questions (15)
SECTION B: System Technologies (23)
SECTION C: Communication and Network Technologies (25)
SECTION D: Data and Information Management (22)
SECTION E: Solution Development (26)
SECTION F: Integrated Scenario (39) - Read ALL the questions carefully.
- Answer ALL the questions.
- The mark allocation generally gives an indication of the number of facts/reasons required.
- Number the answers correctly according to the numbering system used in this question paper.
- Write neatly and legibly.
QUESTIONS
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1 Give the correct word/term for each of the following descriptions. Write only the word/term next to the question number (1.1.1–1.1.10) in the ANSWER BOOK.
1.1.1 A record made to keep track of who made changes to a database and when those changes were made (1)
1.1.2 A method in object oriented programming used to clear the object in memory (1)
1.1.3 A device worn on the wrist that offers additional computing power, sensors as well and can interface with your smartphone, tablet or computer (1)
1.1.4 Performance of physical tasks, commonly repetitive or dangerous ones, by computer controlled machines rather than by human beings (1)
1.1.5 Software that translates programming instructions written in high-level language into a file with an “.exe” extension that can be run independently of the programming language (1)
1.1.6 A peer-to-peer protocol used to transfer and share large files across a network such as the Internet (1)
1.1.7 The concept that more and more devices and objects are being connected to the Internet, with the ability to communicate with other devices and objects and to take intelligent decisions based on the input received (1)
1.1.8 A software system that captures and processes data from everyday business activities (1)
1.1.9 Initiatives to design, use and dispose of technology in an environmentally friendly way (1)
1.1.10 Online seminars which users in remote locations can participate in, using online conference technologies (1)
1.2 Various options are provided as possible answers to the following questions. Choose the answer and write only letter (A–D) next to the question number (1.2.1–1.2.5) in the ANSWER BOOK, for example 1.2.6 D.
1.2.1 An algorithm is …
- a set of instructions written in a computer language that will solve a problem.
- a sequence of logical steps that will solve a problem.
- the source code of a computer program that will solve a problem.
- a sequence of plans for the developing and selling of a computer program. (1)
1.2.2 What will the value of iResult be when the following statement is executed?
iResult := 3 + 5 * 9 div 3 – sqr(3);
- -7
- 6
- 7
- 9 (1)
1.2.3 A file with a .dll extension is …
- used to implement direct links to LAN servers.
- a dynamic link library file.
- used to provide communication to peripheral devices.
- the source code for a database management system. (1)
1.2.4 The deliberate disruption of computer access to an Internet service such as the Web or e-mail by overloading the network with large number of requests is known as a …
- zombie.
- virus hoax.
- trojan Horse.
- denial-of-service attack. (1)
1.2.5 The concept of packaging data and procedures into a single object to prevent access from outside the object is called …
- an object code.
- an encapsulation.
- an object program.
- a control structure. (1)
TOTAL SECTION A: 15
SECTION B: SYSTEMS TECHNOLOGIES
QUESTION 2
Your uncle has decided to start a small business. He wants to run a computer shop and Internet café.
2.1 Your uncle is considering the use of a notebook computer to run the business.
2.1.1 The notebook that is being considered contains 2.16 GHz processor with 2 MB cache memory and 1TB HDD.
- Briefly explain why the use of cache memory inside a processor enhances the performance of the system. (2)
- Why it would not be possible to upgrade the 2 MB cache memory in the CPU of the notebook? (1)
- Give TWO reasons why a notebook with an SSD would be a better option than one that contains a conventional HDD. (2)
2.1.2 The notebook computer will be issued with Windows 10 Enterprise operating system.
- The management of caching and networking capabilities are some of the functions of an operating system.
Name TWO other primary functions of an operating system. (2) - Besides windows operating systems, there is a range of other operating systems.
Briefly state what area(s) of application each of the following operating systems were primarily designed for:- Android (1)
- Linux Ubuntu (1)
2.2 System software consists of utility software.
2.2.1 Explain the general purpose of utility software. (1)
2.2.2 Name ONE type of utility software that is used to avoid other windows from appearing on the screen, while you are browsing the Internet. (1)
2.3 One of the buzzwords in computing is cloud.
2.3.1 What do you need to be able to use cloud computing? (1)
2.3.2 Differentiate between a cloud application and local application. (2)
2.3.3 Give THREE broad benefits of cloud computing. (3)
2.3.4 There are many forms of software as a service.
List and briefly explain THREE applications of software as a service. (6)
TOTAL SECTION B: 23
SECTION C: COMMUNICATION AND NETWORK TECHNOLOGIES
QUESTION 3
3.1 Networking has many advantages in a business environment and there are challenges from a set-up and management point of view.
Name TWO of these challenges. (2)
3.2 Star topology is a popular choice for the set-up of networks for businesses.
3.2.1 Draw a simple diagram to illustrate a star topology. (3)
3.2.2 State TWO advantages of using a star topology. (2)
3.3 The technician will use UTP cables to set up the computers at the business.
3.3.1 Give ONE advantage of using UTP cables. (1)
3.3.2 Signal attenuation is one of the weaknesses of UTP cables. State TWO other weaknesses of UTP cables. (2)
3.3.3 If UTP cables are to be used over a long distance, suggest how the signal attenuation problem can be solved without replacing them with fibre-optic cables. (1)
3.4 Data transmission is governed by protocols.
3.4.1 Which protocol is used for secure websites? (1)
3.4.2 What is the function of the VoIP? (1)
3.5 Study the representation of a network below which can be used by a small business.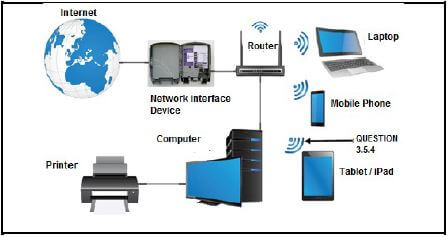
3.5.1 What does VOD stand for? (1)
3.5.2 What is the name given to the physical location in a public area where users may be granted Wi-Fi access, to connect wirelessly to the Internet on the mobile devices? (1)
3.5.3 What is the function of an ISP? (1)
3.5.4 What does the symbol indicated by the arrow head labelled QUESTION 3.5.4 in the above diagram represent? (1)
3.6 Your cousin was accessing a website when a message appeared warning that the website’s digital certificate has expired.
3.6.1 Briefly explain what a digital certificate is and the function it performs. (2)
3.6.2 Give ONE name of a third party organisation which issues digital certificates. (1)
3.6.3 State ONE responsibility of a third party organisation other than issuing digital certificates. (1)
3.6.4 Name FOUR items typically found on a digital certificate. (4)
TOTAL SECTION C: 25
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
A central database has been designed to record employee and departmental information.
4.1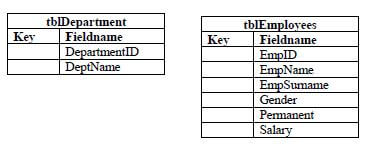
4.1.1 In the tblEmployees table, the Permanent field is used to identify the employment category of an employee.
Name the data type that can be assigned to the field Permanent. (1)
4.1.2 Redraw both tables in you ANSWER BOOK and answer the following questions.
- Identify the primary key field in both tables. Write PK in the first column next to the applicable field in both tables which is a primary key. (2)
- Add a field which is a foreign key to the applicable table. Add FK next to the recent added field in column 1. (3)
- Create a relationship for the tables. Relationship type must be specified when you are linking the tables. (2)
4.2 A poorly designed table or database can result in anomalies.
Name the THREE common types of anomalies that occur in the context of record processing and explain the problem that each of them presents. (3)
4.3 Data integrity is the common term associated with database design and operations.
4.3.1 Distinguish between physical integrity and logical integrity. (2)
4.3.2 Give TWO hardware schemes or devices that can help ensure the physical integrity of data. (2)
4.4 Data independence is another term commonly associated with database management systems.
4.4.1 Name TWO main levels on which data independence can be attained. (2)
4.4.2 Give THREE main advantages or aims of data independence. (3) 4.5 Differentiate between rollback and record lock. (2)
TOTAL SECTION D: 22
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
5.1 The following is an example of a GUI used to record patient information. Study the design and answer the questions that follow.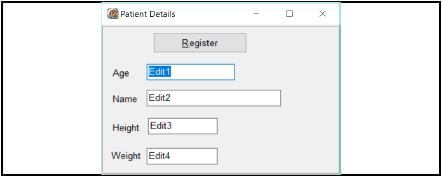
List TWO ways in which the design layout and user friendliness can be improved. (2)
5.2 Various errors can occur while coding and executing a program.
5.2.1 Identify the type of error for each process below. (3)
Type of error | ERROR | Error |
(a) … | No semicolon entered at the end of an instruction | Missing semicolon |
(b) … | The stock amount is calculated incorrectly. The formula is: | No error message |
(c) … | A variable is created as an integer data type to store the number of items. When the program runs, the user enters the word instead of a number in a component | Data-type mismatch |
5.2.2 Explain what is meant by debugging a program. (2)
5.3 Explain the purpose of the following code segment:
5.3.1 AssignFile(txtFile, ‘Payroll.txt’); (2) 5.3.2 Reset(txtFile); (2)
5.4 Arrays have indexes.
5.4.1 Distinguish between array and index. (2)
5.4.2 Give another name for an index. (1)
5.5 Study the class diagram below and then answer the questions that follow.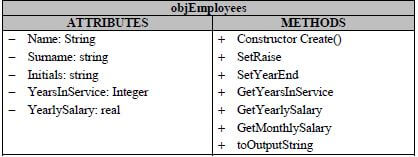
5.5.1 What does it mean to instantiate an object? What is the name of the method used to instantiate an object? (3)
5.5.2 Explain the purpose of an Auxiliary method and list ONE example from the class diagram. (2)
5.6 Examine the following code and answer the question that follows.
var
iCount, iNumber : Integer;
begin
for iCount := 1 to 5 do {1}
begin
iNumber := iCount * iCount; {2}
redOut.Lines.Add(IntToStr(iNumber)); {3}
end; //for
end;
Line numbers are indicated in curly brackets. Copy the trace table below into your ANSWER BOOK and complete it to determine the output.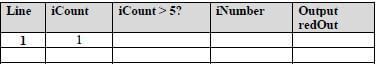
(21 ÷ 3) (7)
TOTAL SECTION D: 26
SECTION F: INTEGRATED SCENARIO
QUESTION 6
A local community ICT training centre is offering a variety of ICT related courses to the local community. The expansion of their network ICT centre has made it possible to better utilise new technologies and ICT.
6.1 One of the students sent an e-mail with the following e-mail address to the training centre manager:
This email address is being protected from spambots. You need JavaScript enabled to view it.
6.1.1 State the domain name of the e-mail. (1)
6.1.2 Name the e-mail recipients below who will not be disclosed in the e-mail for others. (1) 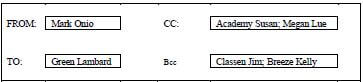
6.1.3 What is the name of the malware that refers to the forging of an e-mail header, so that the e-mail appears to originate from a different source? (1)
6.2 The ICT centre has a website where students can download, make payments, view balances and academic related information.
6.2.1 Briefly explain what a SSL is. (2)
6.2.2 Automatic encryption is something that happens without you consciously choosing to use software to encrypt data. This encryption can be built into both hardware devices and various types of software.
State TWO places where automatic encryption is used. (2)
6.3 Name TWO IT-related jobs that will be created when setting up and expanding the network. (2)
6.4 Access to the server room must be controlled. The staff members use biometrics to gain access to the server room.
6.4.1 Explain the term biometrics. (1)
6.4.2 Give an appropriate example of biometrics to be used in this scenario. (1)
6.4.3 It has been suggested that the other staff members use RFD cards to gain access to the resource centre. State TWO disadvantages of using RFID cards for this application. (2)
6.5 There are concerns about privacy issues with respect to using drones and traffic issues exist where there is high drone activity.
6.5.1 Briefly explain the concept computer drone. (1)
6.5.2 State ONE advantage of using computer drones. (1)
6.5.3 Computer drones are used in the ICT environment, making significant contributions to Big Data. List THREE ICT environments where computer drones are used. (3)
6.6 The ICT training centre uses a management system that uses distributed database system.
6.6.1 What is a distributed database? (2)
6.6.2 State TWO advantages of using a distributed database. (2)
6.7 The most well-known example of a wiki is Wikipedia.
6.7.1 Explain what a wiki is. (1)
6.7.2 State TWO main advantages of wikis. (2)
6.7.3 Give TWO reasons some universities, colleges and schools do not allow their students to use Wikipedia as a source of information in research projects. (2)
6.8 A search engine works as an information locator. Briefly explain what click farms are. (2)
6.9 The community is concerned about children’s exposure to social networking sites and cybercrime.
6.9.1 Suggest TWO ways of using social networking sites responsibly. (2)
6.9.2 A general crime people commit is using unsecured Wi-Fi Internet connections without permission. What term is used to describe this crime? (1)
6.10 Many companies use telecommuting, even in IT departments. Explain what telecommuting is. (2)
6.11 Some people are under the impression that a virtual office exists only as an idea and is not a physical reality. Explain what a virtual office in the context of IT is. (2)
6.12 It is important to keep informed about the developments and trends in IT and we should also keep our software updated. List THREE advantages of updating software. (3)
TOTAL SECTION F: 39
GRAND TOTAL: 150