Information Technology P2 Grade 12 Memorandum - NSC Exams Past Papers and Memos September 2019 Preparatory Examinations
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupMEMORANDUM
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1
1.1.1 Audit trail ✔ (1)
1.1.2 Destructor ✔ (1)
1.1.3 Smartwatch ✔ (1)
1.1.4 Robotics ✔ (1)
1.1.5 Compiler ✔ (1)
1.1.6 BitTorrent ✔ (1)
1.1.7 Internet of Things ✔ (1)
1.1.8 Transaction Processing System/TPS ✔ (1)
1.1.9 Green Computing ✔ (1)
1.1.10 Webinars ✔ (1)
1.2
1.2.1 B ✔ a sequence of logical steps that will solve a problem (1)
1.2.2 D ✔ 9 (1)
1.2.3 B ✔ A dynamic link library file (1)
1.2.4 D ✔ Denial-of-service attack (1)
1.2.5 B ✔ Encapsulation (1)
TOTAL SECTION A: 15
SECTION B: SYSTEM TECHNOLOGIES
QUESTION 2
2.1
2.1.1
- Cache is a small amount of high speed memory ✔ where data and instructions likely to be used next by the CPU is stored, eliminating the need to fetch it from the slower RAM. ✔
Concepts:- High speed memory
- Saving time in fetching instructions (2)
- Cache is embedded on the processor / It is built on the processor and is not removable. ✔
Concept:- not removable / embedded (1)
- Any TWO ✔✔
- Faster at boot up time / faster access time
- No moving parts and is less easily damaged/longer life span /lasts longer/more reliable
- Uses less power
- Generates less heat
- Smaller dimensions (2)
2.1.2
- Any TWO ✔✔
- Provides a user interface
- I/O management
- Process management
- File management
- Security
- Manages system memory
- Optimises efficiency/speed (2)
-
- Android is designed for mobile devices ✔ such as smartphones and tablets. (1)
- Linux Ubuntu is designed to be used in a network or server or desktop environment (not by mobile devices). ✔ (1)
2.2
2.2.1 Any ONE ✔ (1)
- Manage/Maintain/Control computer resources
- Adds more functionality for specific management tasks
- Performs routine maintenance and administration tasks in a computer (1)
2.2.2 Any ONE ✔
- Internet filters
- Spam blockers
- Pop-up blockers
- Anti-spam programs
- Phishing filters
- Any other filtering tool (1)
2.3
2.3.1 Fast and reliable Internet connection ✔ (1)
2.3.2
- Cloud application – is software where most of the processing of the software is done in the cloud by one or more servers on the Internet. ✔
- Local application – is the software/program that is stored and runs on a computing device. ✔ (2)
2.3.3 Any THREE ✔✔✔
- Scalability
- Ubiquity (Anywhere/Anytime)
- Enables collaboration
- Outsources maintenance and upgrades of hardware
- Outsources software and installation and upgrades (3)
2.3.4
- Cloud-based apps ✔ – software that runs on remote servers on the internet ✔
- Downloadable, local installed apps ✔ – software that you rent is downloaded and runs on your local computer✔
- Integrated products ✔ – combine cloud-based software and locally installed software ✔ (6)
TOTAL SECTION B: 23
SECTION C: COMMUNICATION AND NETWORK TECHNOLOGIES
QUESTION 3
3.1 Any TWO ✔✔
- High level of expertise is needed to set it up
- Need a high level of security
- Malware can spread very easily
- If network develops a problem, no one can work
- A central problem with server could lead to loss of connection to network/ non-availability of resources if the server is down/offline
- Cost of hardware (2)
3.2
3.2.1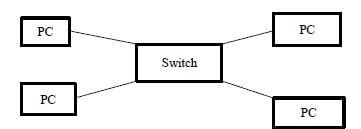
- Switch/Central connection point ✔
- Computers/nodes ✔
- Separate connection to the switch ✔ (3)
3.2.2 Any TWO: ✔✔
- Easy to troubleshoot
- Easy to set-up
- Easy to add new devices
- Faster transmission of data to correct computer through a switch
- Can remove any computer that does not work without affecting the network (2)
3.3
3.3.1 Any ONE ✔
- Cheap to install
- Easy to install
- Flexibility of cables
- High bandwidth over short distances (1)
3.3.2 Any TWO ✔✔
- Electro Magnetic Interference (EMI)
- Crosstalk
- Eavesdropping (2)
3.3.3 Any ONE ✔
- Amplifier can be used to boost the signal quality
- Multiple Access Points added to increase the accessibility radius (1)
3.4
3.4.1 HTTPS ✔ (1)
3.4.2
3.4.1 Any ONE ✔
- Making video/audio/video calls over the Internet/network
- Provides a two-way multimedia communication over the Internet (1)
3.5
3.5.1 Video on Demand ✔ (1)
3.5.2 Hotspot ✔ (1)
3.5.3 To provide Internet access / to provide internet connection ✔ (1)
3.5.4 Wi-Fi / Wireless connectivity ✔ (1)
3.6
3.6.1
- Digital certificate – is an electronic document/ certificate issued by a third party ✔ to verify/authenticate the identity of a person or an organisation ✔ may be trusted for communication of sensitive information. (2)
3.6.2 Certificate Authority/CA ✔ (1)
3.6.3 Any ONE ✔
- Investigate and verify that the business or organisation is what it claims to be
- Its website exists at the IP address specified
- Its public key has not expired (1)
3.6.4 Any FOUR ✔✔✔✔
- Owner’s public key
- Owner’s name
- Expiration date of the public key
- Name of issuer (the Certificate Authority that issued the digital certificate)
- Serial number of the digital certificate
- Digital signature of the issuer (4)
TOTAL SECTION C: 25
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
4.1
4.1.1 Any ONE ✔
- Yes/No
- Boolean (1)
4.1.2 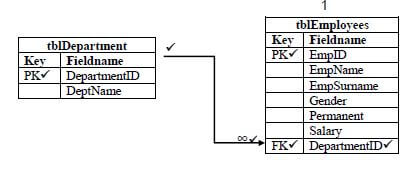
Concepts:
- PK ✔ in tblDepartment and PK ✔ in tblEmployees (2)
- FK, ✔ DepartmentID ✔ and tblEmployees ✔ (3)
- 1 ✔ and ∞✔ (2)
4.2
4.2.1
- Insert anomaly - the database design prevents a user from capturing data when they want or need to. ✔
- Delete anomaly – deleting one piece of data results in the simultaneous removal of other, unrelated data. ✔
- Update anomaly – when an item of data changes, it has to be altered/changed in multiple records in the table. ✔ (3)
4.3
4.3.1
- Physical integrity – overcoming practical issues such as power failure, mechanical failure, natural disasters and dealing with the physical storage and retrieval of data. ✔
- Logical integrity – correctness of data or data making sense in a particular context. ✔ (2)
4.3.2 UPS ✔ and RAID ✔ (2)
4.4
4.4.1 Physical independence ✔ and Logical independence ✔ (2)
4.4.2
- The actual data management is left to the DBMS software ✔
- Multiple applications can interface to the same data because the physical structure of the database is not a factor. ✔
- The use application cannot change the structure or format of the data ✔ (3)
4.5
- Rollback – happens when the DBMS gets the instruction to reverse a transaction or series of transactions and restores the data back to its previous state. ✔
- Record lock – happens when a record is open, either for editing or for inserting, the record is flagged as in use and no other user can make changes to that specific record. ✔ (2)
TOTAL SECTION D: 22
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
5.1 Any TWO ✔✔
- The button at the top should be placed at the bottom
- The edits should be empty
- The order is incorrect – put Name first
- Could use SpinEdits for age instead of an Edit (2)
5.2
5.2.1
| Type of error | ERROR | Error Message | |
| a | Syntax ✔ | No semicolon entered at the end of an instruction | Missing semicolon |
| b | Logical ✔ | The stock amount is calculated incorrectly. The formula is: StockAmount = quantity - ItemPrice | No error message |
| c | Runtime ✔ | A variable is created as an integer data type to store the number of items. When the program runs, the user enters the word instead of a number in a component | Data-type mismatch |
(3)
5.2.2 Debugging is a technique/process of finding/locating ✔ and resolving ✔defects/problems/errors/bugs. (2)
5.3
5.3.1 Creates a link between an external/physical/permanent/textfile ✔ and variable textfile/logical file ✔ in the program (2)
5.3.2 Reset opens ✔ a variable textfile and moves the file pointer/cursor to the start/beginning of the file, ✔ ready to start reading. (2)
5.4
5.4.1
- Array – a data structure that contains a group of variables containing values of the same data type ✔
- Index – an ordinal value indicating the position of the element in the array ✔ (2)
5.4.2 Subscript ✔ (1)
5.5
5.5.1
- Space is created in memory ✔ to keep the attributes of a specific object ✔
OR
A constructor is used to create an instance of the object class/a space is reserved in memory which is allocated to the properties of an object class. (2)
Constructor ✔ (1)
5.5.2
- Auxiliary method – methods (procedures or functions) in the class that can assist with calculations and formatting.✔
OR
Methods which perform specific tasks without modifying the state of the object (i.e. the content of any of the instance fields).
Example: toOutputString ✔ (2)
5.6
Line | iCount | iCount > 5? | iNumber | Output redOut |
1 | 1 | No✔ | ||
2 | 1 ✔ | |||
3 | 1 ✔ | |||
1 | 2 ✔ | No ✔ | ||
2 | 4 ✔ | |||
3 | 4 ✔ | |||
1 | 3 ✔ | No ✔ | ||
2 | 9 ✔ | |||
3 | 9 ✔ | |||
1 | 4 ✔ | No ✔ | ||
2 | 16 ✔ | |||
3 | 16 ✔ | |||
1 | 5 ✔ | No ✔ | ||
2 | 25 ✔ | |||
3 | 25 ✔ | |||
1 | 6 ✔ | Yes ✔ |
(21÷3) = (7)
TOTAL SECTION D: 26
SECTION F: INTEGRATED SCENARIO
QUESTION 6
6.1
6.1.1 orico.co.za ✔ (1)
6.1.2 Classen Jim and Breeze Kelly ✔ (1)
6.1.3 Spoofing ✔ (1)
6.2
6.2.1 Secure Sockets Layer is an encryption protocol ✔ for managing the transmission of sensitive data over the Internet ✔ (2)
6.2.2 Any TWO ✔✔
- DRM (Digital Rights Management)
- ATM
- Internet browsers
- Skype calls
- Online storage devices (2)
6.3 Any TWO ✔✔
- Network engineer
- Network architect
- Network administrator
- Network analyst (2)
6.4
6.4.1 Biometrics refers to the use of personal characteristics ✔ to authenticate the identity of a person. (1)
6.4.2 Any ONE suitable example ✔
- Retina/Eye
- Fingerprint
- Voice recognition
- Facial recognition
- Palm readers (1)
6.4.3 Any TWO ✔✔
- Cards can be cloned
- Cards can be stolen/lost
- Inconvenience of carrying cards around
- Cots of manufacturing cards
- Cards do not validate the identity of the user
- RFID cards can be read from a distance that can trigger the unlocking of the room even when not required (2)
6.5
6.5.1 Computer drone – is an unmanned aerial vehicle or is an aircraft without a human pilot aboard. ✔ (1)
6.5.2 It is used to gather information especially where the environment may be dangerous for humans. ✔ (1)
6.5.3 Any THREE ✔✔✔
|
|
|
(3)
6.6
6.6.1 Distributed database refers to parts of the database ✔ that are spread over multiple servers in different locations. ✔ (2)
6.6.2 Any TWO ✔✔
- Eliminate congestion on a single server
- Can handle a large number of simultaneous users
- The branches of a company can be spread over a large geographical area
- If one server is down, other databases can be used
- Lower cost of communication as less data is being communicated. (2)
6.7
6.7.1 Wiki – a web application that allows people to add to and modify the content of an online knowledge resource. ✔ (1)
6.7.2 Any TWO ✔✔
- Free access or low cost access to information
- Collaboration
- Publish and share documents
- Flexible tool which can be used for a wide range of applications
- Knowledge centre (2)
6.7.3 Any TWO ✔✔
- Poor quality
- Poor standard
- Information not properly researched and approved (2)
6.8 Click farms refer to businesses that use groups of low paid workers whose work is to repetitively click on links ✔ to fake high web traffic. ✔ (2)
6.9
6.9.1 Any TWO ✔✔
- Limit time on the web
- Turn off notifications when doing important work
- Remove yourself from FOMO
- Refrain from insulting other people/bullying
- Be aware that all posts are public
- Do not befriend strangers
- Do not share personal information e.g. ID number, bank account numbers, address etc.
- Be aware that the Internet never forgets information/cannot delete information from the Internet. (2)
6.9.2 Piggybacking ✔ (1)
6.10 Telecommuting – working in decentralised locations e.g. from home, ✔ but using modern communication ✔ to check in at a physical office. (2)
6.11 Virtual office refers to a fixed physical address, ✔ containing minimal office setup which is used as a shared space ✔ by people who work from a mobile office. (2)
6.12
- Fix errors or bugs in our existing programs ✔
- Close/seal security loopholes that hackers and malware might try to exploit ✔
- Add new features and improvements to existing software ✔ (3)
TOTAL SECTION F: 39
GRAND TOTAL: 150