INFORMATION TECHNOLOGY PAPER 2 GRADE 12 QUESTIONS - NSC EXAMS PAST PAPERS AND MEMOS MAY/JUNE 2021
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINFORMATION TECHNOLOGY PAPER 2
GRADE 12
NATIONAL SENIOR CERTIFICATE EXAMINATIONS
MAY/JUNE 2021
INSTRUCTIONS AND INFORMATION
- This question paper consists of SIX sections:
SECTION A: Short questions (15)
SECTION B: System Technologies (25)
SECTION C: Communications and Network Technologies (24)
SECTION D: Data and Information Management (27)
SECTION E: Solution Development (25)
SECTION F: Integrated scenario (34) - Read ALL the questions carefully.
- Answer ALL the questions.
- The mark allocation generally gives an indication of the number of facts/ reasons required.
- Number the answers correctly according to the numbering system used in this question paper.
- Write neatly and legibly.
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1 Choose a term from COLUMN B that matches the description in COLUMN A. Write only the letter (A–R) next to the question numbers (1.1.1 to 1.1.10) in the ANSWER BOOK, e.g. 1.1.11 S.
| COLUMN A | COLUMN B |
| 1.1.1 Someone who uses a variety of tools to plan, structure, create and maintain website content 1.1.2 An update that can be downloaded to fix a specific bug in software 1.1.3 The use of social media to spread false information that seems truthful 1.1.4 A certain amount of high-speed memory built into every hard drive to speed up access to data on a disk 1.1.5 Software that downloads and bombards your computer with advertisements that pop up while connected to the internet 1.1.6 A standard language used for querying and manipulating data in a database 1.1.7 Data capture technology designed to store more data and to work more effectively than barcode systems 1.1.8 An organisation's network which is accessible to users outside the organisation 1.1.9 A collection of programs designed to obtain administrator rights to control a computer for malicious purposes 1.1.10 Wireless technology that allows devices to communicate with each other over a short distance |
|
(10 x 1) (10)
1.2 Give ONE word/term for each of the following descriptions. Write only the word/term next to the question numbers (1.2.1 to 1.2.5) in the ANSWER BOOK.
1.2.1 A high-capacity storage device that uses flash memory chips instead of magnetic metal hard disks (1)
1.2.2 Software that enables an operating system to communicate with a specific hardware device (1)
1.2.3 The concept of 'renting' software instead of buying a license to use it forever (1)
1.2.4 A trend whereby separate technologies and functions from multiple devices are combined into a single multi-purpose device (1)
1.2.5 A text file (max. 4 Kb) used to store customised settings for a website on your local computer (1)
TOTAL SECTION A: 15
SECTION B: SYSTEM TECHNOLOGIES
QUESTION 2
2.1 Explain why point-to-point connections are used between components that exchange large amounts of data. (2)
2.2 A CPU is regarded as the 'heart' of a computer.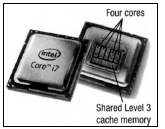
2.2.1 What is a CPU with four cores called? (1)
2.2.2 Explain why a CPU with more than one core can process a task faster than a single-core processor. (2)
2.2.3 Give TWO reasons why the cache memory on the CPU speeds up processing. (2)
2.3 What are the electronic paths that transfer data between components on the motherboard called? (1)
2.4 Discuss TWO characteristics of RAM. (4)
2.5 State why developers can benefit from using virtualisation. (2)
2.6 Firmware is software found in different devices.
2.6.1 State the purpose of firmware. (1)
2.6.2 Where is firmware located in a device? (1)
2.7 Explain the relationship between the CMOS and the BIOS by referring to the purpose of EACH. (2)
2.8 You need to be prepared for a situation where your primary hard disk fails and nothing on your hard disk can be recovered.
List THREE essential things that you should do to ensure that you will be prepared to rebuild your system after installing a new primary hard disk. (3)
2.9 Study the following screenshot: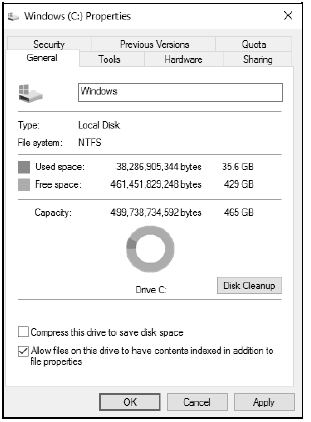
2.9.1 The capacity of the disk is shown in terms of gigabytes. The smallest storage unit is a bit. How many bits are in ONE byte? (1)
2.9.2 Explain why it is a good idea to make sure that the contents of a drive is indexed. (2)
2.9.3 Give ONE reason why you will run a disk clean-up utility. (1)
TOTAL SECTION B: 25
SECTION C: COMMUNICATIONS AND NETWORK TECHNOLOGIES
QUESTION 3
3.1 A network is formed when connecting two or more devices to make communication between the devices possible.
3.1.1 Which LAN standard is commonly used in a cabled network? (1)
3.1.2 Give TWO reasons why a star topology is popular in networks. (2)
3.1.3 Explain why the use of a switch will be an advantage in a network. (2)
3.2 Networks make it possible to transfer data, information and software.
3.2.1 Who is a seeder when downloading files from the internet when using BitTorrent? (1)
3.2.2 State the difference between the internet and an intranet. (2)
3.3 A company decides that their employees must rather work from home for health reasons.
3.3.1 Employees will need to have access to their documents stored on the server at the office.
Name the type of network with which they can access these documents through the internet. (1)
3.3.2 What is a back door when referring to network security? (2)
3.3.3 One team member said that while working from home, files would synchronise automatically when saved in online storage.
Explain what is meant by files being synchronised when saved in this context. (2)
3.4 Search engines, such as Google, are used by many users each day.
3.4.1 Explain the difference between a customised search and a context-aware search. (2)
3.4.2 Why does a sponsored link affect the results obtained from a search engine? (2)
3.5 To enable a web page to be interactive, the web page needs to include specific programming instructions.
3.5.1 Name TWO different scripting languages. (2)
3.5.2 Briefly explain how server-side scripting is implemented to establish an interactive web page. (2)
3.6 Management of many retail companies has to make informed decisions every day. State TWO advantages of using a DSS. (2)
3.7 Give ONE reason why the quality of information presented by wikis, such as Wikipedia, are NOT always reliable. (1)
TOTAL SECTION C: 24
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
A database is used at a mall to store details of stores, staff, clients and other information. A staff member can work at only one store. One of the tables is called tblStores and has the following table design:
Table: tblStores
| Field name | Data type | Description |
| StoreName | Short Text (30) | The name of the store at the mall |
| NumOfSquareMetres | Number (Double) | The total number of square metres the store occupies |
| RentalAmount | Number (Double) | The monthly rent for the store |
| DateOpened | Date/Time | The date on which the store opened for the first time |
| NumYearsOpen | Number (Integer) | The number of completed years the store has been doing business at the mall |
4.1 The DateOpened field has been selected as a primary key field.
4.1.1 Explain the purpose of a primary key. (1)
4.1.2 Give a reason why using the DateOpened field as a primary key may be inappropriate. (1)
4.1.3 Recommend a more suitable primary key for the table tblStores, that could have been included in the tblStores table. (1)
4.2 Normalisation is a term that is commonly used in the context of relational databases.
4.2.1 Explain the term normalisation. (2)
4.2.2 Why does the inclusion of the NumYearsOpen field violate normalisation rules? (2)
4.3 Data needs to be validated to ensure that we have quality data.
Name TWO validation tests that can be performed on the DateOpened field when data is entered into the field. (2)
4.4 A table, tblStaff, was created to save the information of the staff members of each store. Use the ERD diagram below to answer QUESTION 4.4.1 and QUESTION 4.4.2.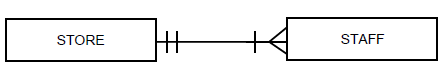
4.4.1 Describe the relationship between the tables using a suitable action verb. (1)
4.4.2 What is the type of relationship between the STORE entity and the STAFF entity? Choose the answer and write only the letter (A–C) next to the question number, e.g. 4.4.2 D.
- Many-to-one relationship
- One-to-many relationship
- Many-to-many relationship (1)
4.5 Indicate whether the following statements are TRUE or FALSE. Write only 'true' or 'false' next to the question numbers (4.5.1 to 4.5.5) in the ANSWER BOOK.
4.5.1 A primary key and a foreign key used to establish a relationship between two tables must have the exact same field name in both tables. (1)
4.5.2 Data saved in a foreign key field in a table can contain duplicates. (1)
4.5.3 Referential integrity can be applied in a single table. (1)
4.5.4 Database redundancy can lead to database anomalies. (1)
4.5.5 An advantage of data independence is that multiple applications can interface to the same data, as the physical structure of the database is independent of the application. (1)
4.6 Most chain stores at malls use data warehousing, which provide storage for large amounts of data. Records that are outdated in the current database need to be moved to the data warehouse.
Give TWO reasons why the outdated records need to be transformed before it is combined with the data in the data warehouse. (2)
4.7 Transactions in a database management system include deleting records. When a record is deleted, it is only flagged as deleted.
Why are these records flagged as deleted and not removed from the database? (1)
4.8 State TWO potential problems in using a single centralised database serving a large number of connected users and requests. (2)
4.9 The mall needs to take measures to ensure that the information stored in the database will not be compromised.
State TWO ways of preventing an SQL injection attack on the database by hackers. (2)
4.10 Online data collection takes place at the pay point in a supermarket.
4.10.1 Define the term online data collection. (2)
4.10.2 Give ONE example of online data collection at the pay point in a supermarket AND explain how the data can be used to the benefit of the supermarket. (2)
TOTAL SECTION D: 27
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
5.1 An algorithm is a step by step breakdown to solving a problem.
5.1.1 Name ONE technique/tool/diagram that can be used to represent an algorithm. (1)
5.1.2 Give ONE reason why algorithms should NOT be language specific. (1)
5.2 Study the following Delphi code and answer the questions that follow:
5 Procedure TForm1.btnCalculateClick(Sender: TObject);
6 Var
7 iSum:integer;
8 begin
9 iSum := 5+7;
10 displayAnswer;
11 end;
12
13 Procedure TForm1.displayAnswer;
14 Var
15 iSum:integer;
16 begin
17 ShowMessage('The sum is: '+ intToStr(iSum));
18 end;
5.2.1 What can be done to make the code in the example above more readable? (1)
5.2.2 When the program is executed, the output displayed in line 17 will be 0.
- What type of error is this? (1)
- Give TWO reasons why the sum is displayed as 0, even though the sum is calculated correctly in line 9. (2)
5.3 The following incomplete Delphi solution is provided for a problem that should display 15 randomly generated odd numbers in the range 10 to 40 (inclusive):
1 iCountOdd := 0;
2 While iCountOdd < 15 do
3 Begin
4
5 iRandom := …………
6 if (………) then
7 Begin
8
9 showMessage(IntToStr(iRandom));
10 End;
11 End;
12
5.3.1 Line 5 needs to be completed. Write Delphi code to generate a random number in the range 10 to 40. (1)
5.3.2 Select the correct option for EACH of the following questions and write down only the CORRECT answer/option in the ANSWER BOOK:
- The IF statement to determine if the randomly generated number is an odd number will be …
- if (iRandom DIV 2 = 1) then
- if (iRandom MOD 2 = 0) then
- if (iRandom MOD 2 <> 0) then (1)
- The statement inc(iCountOdd) should be added to the code above.
Choose the line number for the correct position of the statement:- 4
- 8
- 12 (1)
- Which ONE of the following will provide the correct solution if the While statement in the given code on the previous page must be replaced by a Repeat..Until statement:
- Repeat
…
Until iCountOdd > 15; - Repeat
…
Until iCountOdd >= 14; - Repeat
…
Until iCountOdd = 15; (1)
- Repeat
5.4 Write down the most suitable data types for variables X and Y in the following statements where the data type of the Number variable is not known:
5.4.1 X := Floor(80/12*2); (1)
5.4.2 Y := Sqr(Sqrt(Number)); (1)
5.5 Consider the following UML-diagram and answer the questions that follow:
| TStaff |
| - StaffID - StaffName - StaffSurname + ContactNumber + DateAppointed |
| + create; + getStaffID:String; + setContactNumber(sContactNumber:String); + isValidDate(iDay, iMonth, iYear:integer): boolean; + calcYearsOfExp:integer; |
5.5.1 Differentiate between an accessor method and a mutator method. (2)
5.5.2
- What does the positive sign (+) and the negative sign (-) refer to in the UML diagram? (1)
- Refer to the answer to QUESTION 5.5.2(a) and motivate why instance fields/attributes should rather be declared with the negative sign (-) rather than with the positive sign (+). (1)
5.5.3 Identify ONE procedure in the UML diagram above. (1)
5.6 The Fibonacci sequence is a series of numbers: 1, 1, 2, 3, 5, 8, 13, 21, 34, ...
The next number in the series is calculated by adding up the two preceding numbers.
The following incomplete algorithm has been provided:
The number of terms/numbers in the sequence must be entered and the series displayed.
input iNumTerms //number of terms in sequence
iTerm1← 1;
iTerm2← 1;
if iNumTerms = 1 then
sLine ← iTerm1
display sLine
else if iNumTerms = 2 then
sLine iTerm1 + ' ' + iTerm2
display sLine
else
...
...
...
...
...
...
Complete the algorithm above to display the required output. (8)
TOTAL SECTION E: 25
SECTION F: INTEGRATED SCENARIO
QUESTION 6
A new shopping mall has been built in your area. The availability of computer services and Wi-Fi to businesses and visitors are one of the most important issues to consider.
6.1 The diagram below is an example of a WLAN. Wi-Fi access points have been placed at various places in the shopping mall.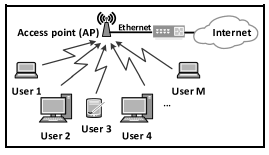
6.1.1 What medium is used to transfer Wi-Fi data? (1)
6.1.2 Give TWO reasons why there may be a need for many access points in the network environment of the mall. (2)
6.2 The local shopping mall allows you to download an app to make navigating the mall easy and it can help customers to have a more enjoyable visit to the mall.
6.2.1 Which type of device will most likely be used to run this app? (1)
6.2.2 What does the term appification of the Web refer to? (2)
6.2.3 You are requested to improve the app by applying defensive programming.
What is defensive programming? (2)
6.2.4 Briefly describe TWO examples of defensive programming techniques. (2)
6.3 Transactions are mostly done electronically. Any data that is sent over a network passes through different nodes. Encryption is necessary to ensure that all transactions are secure.
6.3.1 Name an encryption protocol commonly used to encrypt private data that is sent over the internet. (1)
6.3.2 Briefly explain how public key encryption works. (3)
6.4 GPS and location-based computing are terms that are often used together.
6.4.1 Define location-based computing. (2)
6.4.2 Give an example of the use of location-based computing in a mall environment. (1)
6.5 Staff in different shops must be made aware of cybercrime, such as hacking and DDoS attacks.
6.5.1 Explain the difference between a white hat hacker and a black hat hacker. (2)![]()
6.5.2 Explain the effect of a DDoS attack. (1)
6.5.3 The effects of cybercrime are largely the same as those of normal crime.
Name TWO negative effects that cybercrime can have on businesses. (2)
6.6 MyVSpace is a virtual office space in the mall.
Define the term virtual office. (2)
6.7 During the Covid-19 pandemic, employees of a law firm were requested to work from home. The employees need to have a Google Meet session at 09:00 every work day. These meetings must be recorded.
6.7.1 What is the term used to indicate that an employee uses technology to work from home? (1)
6.7.2 All employees have been provided with a laptop, data and software applications to attend the meetings. What other hardware device would you recommend to be used in a home environment during these meetings, and why? (2)
6.7.3 Name ONE video conferencing platform, other than Google Meet, that can be used for the meetings. (1)
6.7.4 Give ONE example of a cloud storage space/service that could be used for saving the records of the meetings. (1)
6.8 Augmented reality and virtual reality are two of the most promising technologies available to mobile app developers.
6.8.1 Explain the difference between virtual reality and augmented reality. (2)
6.8.2 How can the app improve the shopping experience at the mall by using augmented reality? (1)
6.8.3 Augmented reality is made possible by fusing data from multiple sensors. Name TWO applicable sensors available on a mobile device. (2)
TOTAL SECTION F:34
GRAND TOTAL:150