Information Technology Paper 2 Memorandum - Grade 12 September 2021 Preparatory Exams
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupMEMORANDUM
QUESTION 1
1.1
1.1.1 Encapsulation (1)
1.1.2 Record (1)
1.1.3 Seek time (1)
1.1.4 Green computing (1)
1.1.5 Virtual Reality/(VR) (1)
1.1.6 Internet Service Provider/(ISP) (1)
1.1.7 IT waste/E-waste/E-scrap (1)
1.1.8 Software as a Service (SaaS) (1)
1.1.9 Fuzzy logic (1)
1.1.10 Router (1)
1.2
1.2.1 B – (rapid application development) (1)
1.2.2 A – (Comma Separated Values) (1)
1.2.3 C – (multitasking) (1)
1.2.4 C – (Wireless Access Point/Protocol) (1)
1.2.5 B – (5) (1)
TOTAL SECTION A: 15
SECTION B: SYSTEM TECHNOLOGIES
QUESTION 2
2.1
2.1.1 Cloud application is software, where most of the processing is done in the cloud by one or more servers on the internet. (1)
2.1.2
- Gmail
- Facebook (2)
2.1.3 Local front-end means that the cloud application has a part of the program that is stored and run locally on a device or it might run entirely as a page in a web browser. (1)
2.1.4 Any TWO:
- Google Docs
- Office 365
- Microsoft Office Online
- iWork
- Google G Suite
- Smart Sheet
- Feng Office
- Zoho Workplace
- Quip (2)
2.1.5 Any TWO:
- Scalability
- Ubiquity (Anywhere/anytime)
- Enables collaboration
- Outsource maintenance and upgrades of hardware
- Outsource software installation and upgrades (2)
2.1.6 Service Level Agreement (1)
2.2
2.2.1 Any ONE:
- Augmented Reality technology superimposes/covers a computer- generated image onto a user’s view of the real world.
- It provides a composite 3D view that provides full immersion.(1)
2.2.2 Any TWO:
- Product View
- Enhance content
- Training
- Productivity
- Engage the audience (2)
2.2.3 Any TWO:
- To get or enhance creativity
- Provide a new product experience
- Able to preview the product visually
- Build real-time data experience
- Enjoy experimental experiences
- Functional uses demo (2)
2.2.4 Any TWO:
- Battery life
- Bluetooth connectivity/Wi-Fi
- Field of view in 3D view
- On board OS/Web Browser
- On-board storage capacity
- Inputs/outputs (button, eye tracking, accelerometer)
- Microphone
- Sound capacity
- Display capacity
- Visual tracking (2)
2.3
- Archiving is the process of moving data that is no longer actively used to a separate storage device for long term retention.
- Back-up is the process of making copies/duplicates of data storing it on a different device in different geographical area/location. (2)
2.4
2.4.1 Virtualisation is the process of running multiple computing environments (called virtual machines) on a single set of hardware. (1)
2.4.2 Any TWO:
- Testing different operating systems and hardware
- Cloning computers
- Hosting cloud applications
- Allow multiple people to use the same computer at the same time (2)
2.4.3 Any TWO:
- Less expenditure
- Save assets
- Disaster recovery
- Green IT
- Long term benefits (2)
2.5
- Disk Check
- SMART scan (2)
TOTAL SECTION B: 25
SECTION C: COMMUNICATION AND NETWORK TECHNOLOGIES
QUESTION 3
3.1
3.1.1
- Switch
- Network cable
- Wireless base station (3)
3.1.2 World Wide Web (1)
3.2
3.2.1 BitTorrent is a peer-to-peer protocol used to transfer and share large files across a network such as the Internet. (1)
3.2.2 Any THREE:
- The data used to upload the file is shared between all the users downloading the file.
- The bandwidth is also shared, allowing users to download the file more quickly.
- Since the file is not uploaded to a single website or hosted by a single user, people may continue to share it for years after it was first shared.
- For websites using torrents to share pirated material, the website itself is not sharing the illegal materials nor the files linking to illegal materials.
- BitTorrent allows many users to download popular files quickly because it eliminates the bottleneck problem that you get when a file is shared from a single source/server.
- It reduces the cost to the host (no single host has to pay for millions of people downloading the file from their server).
- It forces some equality in sharing (every time you run the client software, others can download the files in your shared folder and in your downloaded files folder).
- It offers an effective use of available download bandwidth.
- BitTorrent client software is usually free. (3)
3.2.3 Any THREE:
- Many users have used torrent files to share viruses.
- Many ISPs throttle or shape torrent downloads, preventing you from downloading them at high speed.
- Torrents are often used to pirate videos and music.
- Torrenting is only legal if you have a licence to use the content which you torrent.
- BitTorrent is purely a content distribution method and does not incorporate any technology to monitor or restrict any activity. (3)
3.3
3.3.1 Remote access refers to several technologies or applications that allow you to connect to a computer over the network. (1)
3.3.2 Any THREE:
- Opening applications
- Sending e-mails
- Fixing problems
- Use the computer as if it is your computer
- See the remote computer’s display on your monitor or view the screen of the remote target computer on your local computer.
- Use the local computer’s mouse and keyboard to control the target computer remotely. (3)
3.3.3
- Local network – is a remote access that allows you to connect to a computer on your local network and use it as if it was your own computer.
- Online remote access/Virtual Private network – allows you to connect and manage a computer anywhere in the world. (4)
3.4 Any TWO:
- Software firewall installed on the user’s computer OR (Firewall installed on user’s computer).
- Software firewall that is installed on a server or router
- Hardware firewall installed between a local computer and the Internet. (2)
3.5 Network Topology refers to the layout/structure of a network. (1)
TOTAL SECTION C: 22
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
4.1 Any TWO:
- Accuracy
- Consistent
- Current
- Complete
- Relevant (2)
4.2
4.2.1 Data verification is a manual technique that is used to make sure that the data on a database is correct and accurate. (1)
4.2.2
- Full verification – requires that each piece of data that is entered into a database is read and checked by someone.
- Sample verification – a process in which randomly selected samples of data is checked to ensure that there are no systematic errors. (2)
4.2.3 Any TWO:
- Records who made changes to the system
- Records what the user changed from the system
- Records when they made changes (2)
4.3 Any TWO:
- Designing a database
- Security or setting up and enforcing user rights, encryption etc.
- Backup, restoration plans and policies to determine whether the database is out-growing the hardware that it runs
- General maintenance of the database
- Monitoring the database performance (2)
4.4
4.4.1 Any FOUR:
- Primary key
- Alternate key
- Synthetic OR Surrogate key
- Foreign key
- Composite key OR Concatenated key (4)
4.4.2 Field OR Column (1)
4.5
4.5.1 (True/False) OR (Yes/No) OR (Boolean) (1)
4.5.2 (a) In the diagram below (Marks allocation):
tblCustomer table
- CustNo(PK)
tblOrders table
- OrderNo(PK)
- CustNo(FK)
tblPrint table
- PrintNo(PK)
- OrderFormNo(FK) (5)
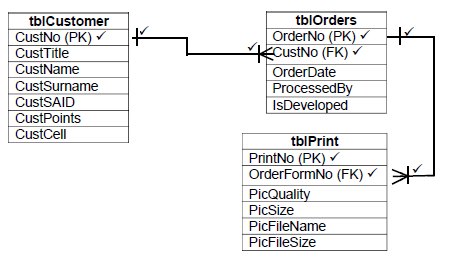
4.5.2 (b) In the diagram above (ERD mark allocation): (4)
(4)
TOTAL SECTION D: 24
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
5.1
5.1.1 Debugging refers to the process of locating and removing errors found in a program. (1)
5.1.2 Exception handling (1)
5.1.3 Try..Except block/statement (1)
5.1.4 Exception (1)
5.2
5.2.1
- Class name section
- Attributes section
- Methods section (3)
5.2.2 Any ONE:
- toString is used to format the output of a class by converting selected attributes of a class into string format.
OR - toString method is used to display the state of the class, i.e. displays the values currently held by each of the attributes. (1)
5.2.3 Unified Modelling Language (1)
5.2.4
- Getters (1)
- Setters (1)
- Helper (1)
5.3
5.3.1 11 (1)
5.3.2 25 (1)
5.3.3 Digital World (1)
5.4
5.4.1
Line No | Item | Num | Price | Cost | Total | redOut |
1 | 0 | |||||
2 | Baked beans | |||||
3 | 3 | |||||
4 | 3,29 | |||||
5 | 9,87 | |||||
6 | 9,87 | |||||
7 | Kewl Drink | |||||
8 | 5 | |||||
9 | 1,95 | |||||
10 | 9,75 | |||||
11 | 9,87 | |||||
12 | Total amount to pay: R | |||||
13 | 9 | |||||
14 ÷ 2 (7)
5.4.2 Logical error (1)
5.4.3
- Total := Total + Cost;
- redOut.Lines.Add(FloatToStr(Total)); (2)
TOTAL SECTION D: 25
SECTION F: INTEGRATED SCENARIO
QUESTION 6
6.1
6.1.1
- Fix errors or bugs in our existing programs
- Close security loopholes that hackers and malware might try to exploit
- Add new features and improvements to the existing software (3)
6.1.2 Patch is an update that can be downloaded to fix a specific bug in your software.
Service pack is a collection of fixes, updates and new features since the release of the original software or previous pack OR is a release of corrections and new features since the release of the original software. (2)
6.2
6.2.1 Computer criminal is anyone who uses ICT to commit a crime. (1)
6.2.2 Any THREE:
- Theft of physical computer equipment
- Theft of intellectual property
- Identity theft
- Financial gain/Theft of money
- Theft of data/Espionage
- Theft of resources (3)
6.2.3
- Backdoor is a hidden way to gain access to a computer, system or software.
- Piggybacking is when criminals gain access to and use someone else’s internet connection without paying for it. (2)
6.2.4 Any THREE:
- Installing and updating anti-virus software
- Using a firewall
- Keeping all your software up-to-date
- Being aware of current trends in computer crime
- Applying common sense
- Following a good password policy (3)
6.2.5
- White hat hacker (Good hacker) – helps companies to improve their security by trying to hack into their computers.
- Black hat hacker (Bad hacker) – illegally break into the computer with malicious intention. (4)
6.2.6 Distributed Denial Of Service/DDOS (1)
6.3
6.3.1 Globalisation is an increase in the rate and ease with which people, companies and governments from different countries interact. (1)
6.3.2
- Transportation
- Improvements in computers and computer networks (2)
6.3.3 Any THREE:
- Allowing families to keep in touch, even over large distances.
- Helping people to keep and maintain larger social networks.
- Increasing people’s social and romantic opportunities.
- Improving job opportunities, with citizens from other countries working in foreign countries.
- Helping people understand different points of view, with research showing how communicating with different people can increase empathy. (3)
6.4
6.4.1 Data cap is a term used to describe the data limit. (1)
6.4.2
- Bitcoin
- Bitcoin is digital money used on the Internet for various services. (2)
6.4.3 Cascading Style Sheets (1)
6.4.4 .js (1)
6.5 Knowledge-based systems (1)
6.6 Identifies and removes temporal files that are no longer needed and cleans out old files, programs and settings that cause a computer to slow down. (1)
6.7
6.7.1 Internet of Things (1)
6.7.2 IoT refers to the billions of devices around the world that are connected to the Internet through sensors or Wi-Fi. (1)
6.7.3 Any TWO:
- Increasing processing power of embedded platforms
- Development of smaller Oss and protocols
- Development of wireless communications (2)
6.8 Memes is an image, video piece or text typically/normally humorous/funny in nature that is copied and spread rapidly by the Internet users. (1)
6.9 Any TWO:
- Use disk clean-up tool
- Uninstall unused software
- Empty recycle bin
- Compress data not frequently used (2)
TOTAL SECTION F: 39
GRAND TOTAL: 150