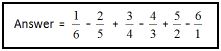INFORMATION TECHNOLOGY PAPER 2 GRADE 12 QUESTIONS - NSC PAST PAPERS AND MEMOS NOVEMBER 2016
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINFORMATION TECHNOLOGY
PAPER 2
GRADE 12
NSC PAST PAPERS AND MEMOS
NOVEMBER 2016
INSTRUCTIONS AND INFORMATION
- This question paper consists of SIX sections:
SECTION A: Short Questions (15)
SECTION B: Systems Technologies (25)
SECTION C: Communication and Network Technologies (25)
SECTION D: Data and Information Management (25)
SECTION E: Solution Development (20)
SECTION F: Integrated Scenario (40) - Read ALL the questions carefully.
- Answer ALL the questions.
- The mark allocation generally gives an indication of the number of facts/reasons required.
- Number the answers correctly according to the numbering system used in this question paper.
- Write neatly and legibly.
QUESTIONS
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1 Various options are provided as possible answers to the following questions. Write down the question number (1.1.1–1.1.5), choose the answer and make a cross (X) over the letter (A–D) of your choice in the ANSWER BOOK.
EXAMPLE: ![]()
1.1.1 The type of system software that can be used to perform routine maintenance tasks is known as …
- the database management system.
- utility software.
- device drivers.
- communication software. (1)
1.1.2 Intellectual property rights refer to the …
- permission granted to an individual to refer to a document created by another author.
- rights of the author of a software application, claiming ownership of the idea behind the program.
- rights a website has over the pictures on their site.
- permission granted to an individual to copy part of a published document. (1)
1.1.3 Bandwidth in e-communication refers to …
- media where one is able to surf the net and make telephone calls at the same time.
- the total number of files that can be transferred by one user.
- the width of the cable transferring the data.
- the total amount of data that can be carried from one point to another in a given period of time.
1.1.4 The conversion of binary number 10111 to a decimal number is ...
- 23.
- 22.
- 30.
- 11. (1)
1.1.5 How many times will the loop below be executed?
Q?1
While Q > 0 do
…
Q ? Q * 3 – 1
End While
- Once
- Not at all
- Infinitely
- Three times (1)
1.2 Give ONE word/term for each of the following descriptions. Write only the word/term next to the question number (1.2.1–1.2.10) in the ANSWER BOOK.
1.2.1 The unnecessary repetition of data in a database file (1)
1.2.2 The process of maximising the number of visits to a particular website by ensuring that the site appears high on the list of results returned by a search engine (1)
1.2.3 A software update that is designed to correct a certain or specific problem/error that occurs in software that has been released or is in use (1)
1.2.4 The type of software provided at no cost by a company where the company retains all rights to the software (1)
1.2.5 A signal created and sent to the CPU that is caused by some action taken by a hardware device (1)
1.2.6 Part of an organisation's intranet that is made available to users outside the organisation (1)
1.2.7 Computing where the physical location of a person or object is determined and used (1)
1.2.8 The protocol used to transfer large files between remote computers that have an Internet connection (1)
1.2.9 A copyright licence that allows one to use parts of, copy and distribute work for non-profit purposes (1)
1.2.10 A system where parts of a database are spread across servers in separate locations (1)
TOTAL SECTION A: 15
SCENARIO |
SECTION B: SYSTEMS TECHNOLOGIES
QUESTION 2
Learners from the IT class need to man the help desk at the exhibition and answer a variety of computer-related questions.
2.1 Users want to know whether the BIOS is still required in a computer system today. Motivate the need for the BIOS by stating TWO important tasks it performs. (2)
2.2 How does the use of virtual memory prevent the problem of the operating system running out of memory when executing programs? (3)
2.3 The performance of a computer depends on the performance of the CPU. How does EACH of the following contribute to improving the performance of the CPU:
2.3.1 Cache memory (3)
2.3.2 Hyperthreading (2)
2.3.3 Dedicated video/graphics cards (2)
2.4 Users often complain that their computers initially performed well, but were very slow after some time.
Give TWO possible reasons for this AND explain how to solve this problem. (4)
2.5 Most computer users use USB flash disks which are plug-and-play compliant. Briefly explain what plug-and-play compliance means. (2)
2.6 The reliable storage and backup of data are important in any IT environment.
2.6.1 RAID technology is often used to improve the reliability of data storage. Briefly explain the concept of mirroring used in RAID technology. (2)
2.6.2 Other than RAID technology, state TWO techniques that have been introduced to improve the reliability of hard disk drives as storage devices. (2)
2.6.3 A network-attached storage (NAS) device could be used to backup data on-site. State TWO advantages of using network-attached storage devices to backup data on-site. (2)
2.7 Software as a Service (SaaS) is used at the school. Motivate the use of SaaS at a school. (1)
TOTAL SECTION B: 25
SECTION C: COMMUNICATION AND NETWORK TECHNOLOGIES
QUESTION 3
A peer-to-peer LAN, which may be used by the exhibitors, will be provided in the school hall. The LAN in the hall will be connected to the school's client-server network.
3.1 One advantage of using a network is that one is able to share hardware, such as printers.
3.1.1 State TWO other advantages of networking computers. (2)
3.1.2 Explain why a client-server network is more suitable than a peer-to-peer network to host a school's administration system. (2)
3.2 TCP/IP is one of the standard protocols currently used in networks.
3.2.1 Briefly explain the purpose of TCP/IP. (2)
3.2.2 SMTP is one of the protocols in the TCP/IP suite. What is the purpose of the SMTP? (1)
3.3 The school uses copper cables as a communication medium in their LAN.
3.3.1 State TWO weaknesses/disadvantages of copper cables as a communication medium. (2)
3.3.2 Fibre-optic cables were installed in the area around the school as part of a WAN that the school will be able to use.
- What medium is used to transfer data in fibre-optic cables? (1)
- Motivate why fibre-optic cables would be advisable to use in a WAN. (1)
3.4 The school's administration data needs to be kept safe on their network. State TWO possible ways in which data could be tampered with on a LAN. Suggest a precautionary measure that could be taken in EACH case to prevent these problems. (4)
3.5 The exhibitors can use laptop computers to connect to the Internet, using the school's wireless connection.
3.5.1 What hardware will a laptop computer require to connect wirelessly to the Internet? (1)
3.5.2 State TWO disadvantages of wireless communication. (2)
3.6 Many visitors at the exhibition will use their mobile devices to access the Internet and interact with the presentations by the exhibitors.
3.6.1 Explain the term convergence relating to mobile devices. (2)
3.6.2 State TWO constraints users normally experience when using mobile devices. (2)
3.7 There are several free public Wi-Fi hotspots with limited data per day that visitors can use in the area where the school is situated.
3.7.1 What is a public Wi-Fi hotspot? (2)
3.7.2 Motivate the reason for limiting the data per day for the users of these Wi-Fi hotspots. (1)
TOTAL SECTION C: 25
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
The information on the exhibition is stored in a database.
4.1 Quality data is needed for useful information to be extracted from a database. List THREE characteristics of quality data. (3)
4.2 While testing the database one of the users complained about an update anomaly that occurred.
What is an update anomaly? (2)
4.3 The school runs their DBMS (database management system) on their server. What is the advantage of running a DBMS on a server? (1)
4.4 Many learners are interested in careers in the database environment.
4.4.1 What is the responsibility of a database administrator? (1)
4.4.2 State TWO tasks specific to the job description of a database analyst. (2)
4.5 After extensive use of a database where the data rapidly accumulates, the database may become large and slow. Suggest a solution to scale down the size of the database without losing the functionality of the database. (1)
4.6 The data for the exhibition has been recorded in a database consisting of two tables, tblExhibitors and tblStands, in a one-to-many relationship. The structure of the tables and its content are shown below.
tblExhibitors | |||
Name of field | Data type | Description | |
| ExhibitorNo | Autonumber | Unique exhibitor's number |
CompanyName | Text | Name of company | |
ContactNo | Text | Contact number of company | |
Data of four records in the tblExhibitors table:
ExhibitorNo | CompanyName | ContactNo |
1 | Funda | 0246523652 |
2 | MoreDevices | 0117857411 |
3 | NewWiz | 0121234565 |
4 | BooksForAll | 0164525263 |
tblStands | |||
Name of field | Data type | Description | |
| StandNo | Text | Unique stand number |
ExhibitorNo | Number | Exhibitor number | |
PlugPoint | Yes/No | Plug point required or not | |
Assistants | Number | Number of assistants required | |
The tblStands table below shows all the stands allocated to the exhibitors at the exhibition.
StandNo | ExhibitorNo | PlugPoint | Assistants |
A01 | 4 | ✔ | 2 |
A03 | 2 | ✔ | 0 |
A04 | 2 | ✔ | 1 |
B01 | 3 | ✔ | 1 |
B02 | 3 | 0 | |
C01 | 1 | 2 | |
C02 | 2 | ✔ | 2 |
C03 | 4 | ✔ | 4 |
4.6.1 The organiser is concerned that the same stand might be allocated to more than one exhibitor. Explain why the current design of the database will not allow for the same stand to be allocated to more than one exhibitor. (2)
4.6.2 Use the tblExhibitors and tblStands tables above and write SQL statements to perform the following tasks:
- Display the stand numbers that require a plug point. (3)
- Allocate an additional assistant to each stand. (3)
- The NewWiz company has incorrectly reserved an extra stand for the exhibition. Remove the stand with stand number B02 from the database. (2)
4.6.3 The following SQL statement was entered:
SELECT CompanyName, Count(StandNo) AS NumStands,
Sum(Assistants) AS SumAssistants
FROM tblExhibitors, tblStands WHERE
tblExhibitors.ExhibitorNo = tblStands.ExhibitorNo
GROUP BY CompanyName;
Use the example data provided for the tblExhibitors and tblStands tables and give the exact output for the SQL statement above. (5)
TOTAL SECTION D: 25
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
5.1 Exhibitors must register with the committee to ensure that no double bookings occur.
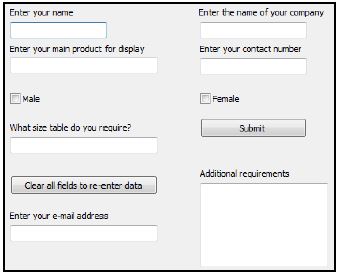
5.1.1 The electronic form below was designed to be used for online registration.
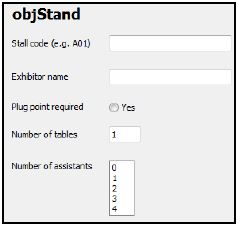
- 5.1.2 The form below was designed to capture the data of a stand object named objStand. Critically comment on the layout of the components of the form, by indicating TWO ways in which the layout can be improved. (2)
- Critically evaluate the components on the form that are used to obtain data from the user. Identify TWO poorly chosen components and suggest a more suitable component in EACH case. Motivate EACH suggestion. (2)
Using the above form, draw a UML (unified modelling language) diagram for the objStand object class.
The diagram must contain the following:
- All the attributes for this object according to the specifications of a UML diagram
- An accessor method for the 'Stall code' attribute
- A mutator method for the 'Plug point required' attribute (4)
5.2 A number of competitions will be run during the course of the exhibition. The IT learners are requested to assist in developing apps for these competitions.
5.2.1 The answer to a mathematical sequence is required. The program must randomly generate a number in the range from 1 to 10 (inclusive) and use this value to generate the terms of the sequence and the required answer.
Example:
If the random number generated is 6, the answer must be calculated as follows:
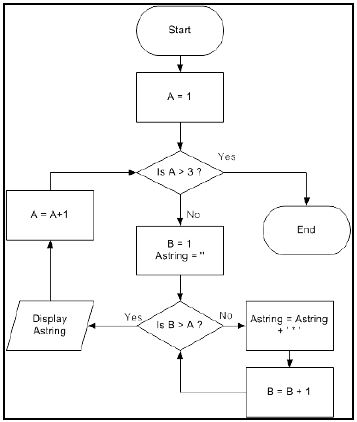
5.2.2 One of the competitions will require that the learners determine the output for a program segment represented by the flowchart below. Write pseudocode to generate the random number and calculate the answer for the sequence generated. Do NOT display the sequence of terms. (7)
Copy and complete the trace table below to determine what the output of this program segment will be.
A | Is A>3? | B | Astring | Is B>A? | Display |
(5)
TOTAL SECTION E: 20
SECTION F: INTEGRATED SCENARIO
QUESTION 6
The exhibition will showcase a variety of topics and new technologies. A separate help desk will be available to assist with Internet-related aspects.
6.1 The school hosts a dynamic website and will use this website to promote the exhibition.
6.1.1 Explain the difference between a dynamic website and a static website. (2)
6.1.2 Important information regarding the exhibition will appear on the school website and an RSS facility will be provided. What is an RSS facility? (2)
6.1.3 It has been suggested that a blog should be used to promote the exhibition.
- Give an example of how a blog can be used for this purpose. (2)
- Discuss scalability with reference to the virtual server hosting a blog and the traffic reacting to a blog post. (2)
6.2 Each exhibitor will be issued with a wrist band containing an RFID tag to allow the exhibitor access to the canteen for lunch.
6.2.1 What technology is used by RFID tags? (1)
6.2.2 Motivate the use of RFID tags instead of tickets with bar codes. (1)
6.3 A number of Internet-related questions were submitted to the IT learners at the help desk.
6.3.1 The Internet provides various online storage facilities.
- Briefly discuss TWO advantages of using cloud storage. (2)
- Motivate why the following TWO issues would be important when choosing a specific online storage facility:
- Speed
- Security (2)
6.3.2 The Internet of Things is one solution for information overloading. (a) Briefly explain what the Internet of Things is. (2) (b) What is meant by information overloading? (2)
6.3.3 The graph below shows some VOD services that are available on the Internet. 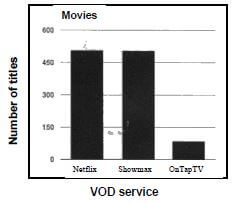
- What is a VOD service? (1)
- Netflix is a streaming service.
Differentiate between using a streaming service and downloading movies. (2)
6.3.4 HTML (hypertext mark-up language) and JavaScript, which is a scripting language, are often mentioned in terms of web page design.
- Why does one need HTML to display web pages? (1)
- Why is JavaScript regarded as a scripting language? (1)
6.4 One of the exhibitors will do a presentation on the capabilities of intelligent self-driven vehicles. 
6.4.1 State ONE essential intelligent task that the software designed for a self-driven vehicle should be able to perform. (1)
6.4.2 Self-driven vehicles use GPS devices.
Name TWO other hardware devices that this type of vehicle should have in order to perform the intelligent tasks required. (2)
6.4.3 It has been stated that there will be fewer accidents with self-driven vehicles as human error will be eliminated.
State ONE disadvantage of self-driven vehicles. (1)
6.5 A cybercrime expert will compile a poster about computer crimes committed by means of ICT as a tool.
6.5.1 Give ONE example of cybercrime that affects society negatively. (1)
6.5.2 Discuss ONE way in which cybercrime can have a negative influence on a business. (2)
6.5.3 Explain how phishing is used in online fraud scams. (2)
6.5.4 How would an audit trail assist when the hacking of a database is investigated? (2)
6.5.5 Explain what a denial-of-service attack is. (2)
6.6 An environmental agency requested a stand to promote the responsible use of computers in the environment. Suggest TWO ways in which the negative effects of computers on the environment can be minimised. (2)
6.7 The Department of Home Affairs will attend the exhibition to encourage people to apply for their new smart ID cards.
6.7.1 Briefly explain what a smart card is. (1)
6.7.2 Explain the advantage for citizens to have smart ID cards. (1)
TOTAL SECTION F: 40
GRAND TOTAL: 150