COMPUTER APPLICATION TECHNOLOGY PAPER 2 GRADE 12 QUESTIONS - NSC PAST PAPERS AND MEMOS FEBRUARY/MARCH 2017
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupCOMPUTER APPLICATION TECHNOLOGY
PAPER 2
GRADE 12
NSC PAST PAPERS AND MEMOS
FEBRUARY/MARCH 2017
INSTRUCTIONS AND INFORMATION
- This question paper consists of:
SECTION A: (25 marks)
SECTION B: (75 marks)
SECTION C: (50 marks) - Answer ALL the questions.
- Number the answers correctly according to the numbering system used in this question paper.
- Start EACH question on a NEW page.
- Do NOT write in the right-hand margin of the ANSWER BOOK.
- Leave a line after EACH subquestion.
- In general, a mark is allocated per fact. A 2-mark question would therefore require TWO facts, et cetera.
- Write neatly and legibly.
QUESTIONS
SECTION A
QUESTION 1: MULTIPLE-CHOICE QUESTIONS
Various options are provided as possible answers to the following questions. Write down the question number (1.1.1–1.1.10), choose the answer and make a cross (X) over the letter (A–D) of your choice in the ANSWER BOOK.
EXAMPLE:
1.1.11 ![]()
1.1 Which ONE of the following applications does NOT logically belong with the others (in other words, the odd one out)?
- Mozilla Firefox
- Adobe Reader
- Google Chrome
- Microsoft Edge (1)
1.2 Which ONE of the following is NOT a wireless Internet connection?
- LTE
- ADSL
- 3G
- WiMAX (1)
1.3 The downloading of large files has an impact on …
- ergonomics.
- bandwidth.
- resolution.
- recycling. (1)
1.4 Which ONE of the following is NOT a security measure used with online banking?
- Password
- Pin code
- OTP (one-time password)
- Fingerprint recognition (1)
1.5 Which ONE of the following functions will calculate the number of cells in the range A1:A13 that has a value of 5 or more?
- =COUNTIF(A1:A13, ''<5'')
- =COUNTIF(A1:A13, ''>5'')
- =COUNTIF(A1:A13, ''>=5'')
- =COUNTIF(A1:A13, ''<>5'') (1)
1.6 Which ONE of the following is NOT an example of a multipurpose device/ computer?
- Webcam
- Phablet
- Netbook
- Tablet (1)
1.7 The … tab on the Microsoft Word ribbon includes functions such as accepting or rejecting changes.
- Insert
- Review
- References
- Mailings (1)
1.8 Which ONE of the following is the most likely to cause compatibility problems or to have compatibility problems when upgrading to a new version of an operating system?
- Word processing files
- Firewall
- Drivers
- Browser (1)
1.9 Which of the following will always be TRUE regarding open-source software?
- It is free of charge.
- The source code is made available.
- Changes can be made and distributed.
- It is distributed only with new computers.
- (i) and (ii)
- (iv) and (ii)
- (iv) and (iii)
- (ii) and (iii) (1)
1.10 Which ONE of the following specifications is the most likely to indicate that a computer is a notebook?
- 1 TB HDD
- Touchpad
- Windows 10 Home (64 bit)
- USB 3.0 (1)
[10]
QUESTION 2: MATCHING ITEMS
Choose a term/concept from COLUMN B that matches the description in COLUMN A. Write only the letter (A–S) next to the question number (2.1–2.10) in the ANSWER BOOK, for example 2.11 T.
COLUMN A | COLUMN B |
2.1 An accessibility option that allows a user to press key combinations such as Ctrl+Alt+Delete, one key at a time | A spyware |
(10 x 1) (10)
QUESTION 3: TRUE/FALSE ITEMS
Indicate whether the following statements are TRUE or FALSE. Choose the answer and write 'true' or 'false' next to the question number (3.1–3.5) in the ANSWER BOOK. Correct the statement if it is FALSE. Change the underlined word(s) to make the statement TRUE. (You may not simply use the word 'NOT' to change the statement. NO mark will be awarded if only FALSE is written down.)
EXAMPLES:
QUESTION | ANSWER |
Google is the world's most popular search engine. | True |
An NIC has slots for hardware components such as the CPU. | False – motherboard |
3.1 Distributed computing refers to the process where money is raised via numerous small donations using the Internet. (1)
3.2 The COUNTA spreadsheet function counts how many cells in a given range contain numerical values. (1)
3.3 SATA is a type of interface that connects computers to monitors/ data projectors. (1)
3.4 The contrast ratio of a display device is the relationship between the width and height of an image on the screen, such as 4 : 3. (1)
3.5 The correct spreadsheet function to determine the second fastest time run by a group of 100 metre sprinters is the SMALL function. (1)
[5]
TOTAL SECTION A: 25
SECTION B
QUESTION 4: SYSTEMS TECHNOLOGIES
4.1 Many new cars and taxis have GPS systems and webcams fitted to the dashboards of the vehicle. Data, including the video, is often saved to an SSD.
4.1.1. What is the main reason taxi drivers would use a GPS system? (1)
4.1.2 Give ONE reason why the GPS system should be updated regularly, besides removing bugs and improving the security of the software. (1)
4.1.3 Give THREE reasons why a company would install and use a webcam AND a GPS in a bus or taxi to record the journey. (3)
4.1.4 Why would the bus or taxi company install an SSD rather than an HDD (hard disk drive) to save the video and data within the vehicle? (1)
4.2 Explain why you can still use graphics on your computer even if you take out the graphics card you purchased. (1)
4.3 Study the following specifications of a smartphone:
|
4,3.1 What is a possible disadvantage of the high MP value on the camera on this smartphone? (1)
4.3.2 Give ONE setting that can be changed to make the battery of the smartphone last longer. (1)
4.3.3 State TWO advantages of having a touch screen on a smartphone. (2)
4.4 State TWO potential disadvantages of file synching. (2)
4.5 POS (point of sale) systems are used in most shops.
4.5.1 What other input device can be used by the cashier if the barcode scanner is broken? (1)
4.5.2 Where will the price need to be corrected if it is noted that the price of a product that has been scanned on a POS system is incorrect? (1)
4.6 What does a site licence allow a user to do? (2)
4.7 Why would a user open the Task Manager if his computer is 'running very slowly'? (2)
4.8 What does the term volatile mean when referring to RAM? (1)
4.9 State TWO ways in which user authentication can take place on a smartphone. (2)
4.10 Give TWO reasons why e-mail attachments are often not set to automatically download on mobile devices such as smartphones. (2)
4.11 What is the easiest way to make more USB ports available on a computer? (1)
[25]
QUESTION 5: INTERNET AND NETWORK TECHNOLOGIES
5.1 State TWO advantages of purchasing from an online shop, other than potentially lower prices. (2)
5.2 Explain the significance of the text 'mobi' in the URL 'www.vicbayfm.mobi'. (1)
5.3 Consider the following advertisement:
|
5.3.1 The advertisement indicates that the maximum speed is 'up to 10 Mbps'. Give TWO possible reasons for an ADSL line not performing at its maximum speed. (2)
5.3.2 What is the purpose of the router mentioned above? (1)
5.4 Why do you think cloud storage is not used as much in South Africa as in other countries? Give TWO reasons.
NOTE: One-word answers will NOT be accepted. (2)
5.5 State TWO ways in which a user can convey emotions in an IM (instant messaging). (2)
5.6 Teachers at a local school post assignments on the intranet for learners to access.
5.6.1 What type of application would be used to access the assignments on the intranet? (1)
5.6.2 Explain how learners could still access their assignments on the intranet using their home computers AND motivate your answer. (2)
5.7 What are FTP servers and services used for? (1)
5.8 Which hardware or software technology is often used to control and monitor access between a network and the Internet? (1) [15]
QUESTION 6: INFORMATION MANAGEMENT
6.1 Part of a form that was designed to capture data for a poll on the matric farewell is shown below. 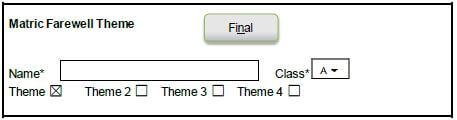
6.1.1 Explain why the control(s) used to get the user's response for the theme was a poor choice. (1)
6.1.2 Give ONE reason why the button control ('Final') on this form may be confusing to a user. (1)
6.1.3 Explain why a list box would have been a better choice to select the class rather than the combo box in the example above. (3)
6.2 The caching of web pages can mean that previously accessed web pages might be displayed in a web browser.
Explain how this might affect the quality of information on the web page. What can one do if one suspects that he/she is viewing a cached web page? (2)
6.3 A teacher wishes to analyse the performance of the 27 learners in her class according to the levels that they achieved in the examination, using the data below.
A | B | C | |
1 | Level | Number | |
2 | 1 | 2 | |
3 | 2 | 3 | |
4 | 3 | 4 | |
5 | 4 | 5 | |
6 | 5 | 6 | |
7 | 6 | 4 | |
8 | 7 | 3 | |
9 | Total | 27 |
6.3.1 Give the name of the function cell B2 that could have been used to determine the number of learners who performed on level 1. (1)
6.3.2 The teacher wants to use a graph to analyse the performances of the learners. 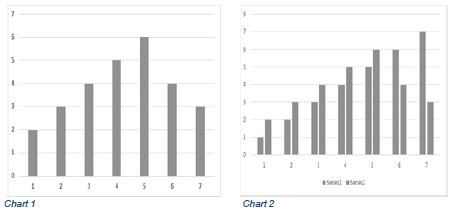
The teacher knows the graph should look like Chart 1 (on the left), but whenever she tries to draw it, it turns out like Chart 2 (on the right).
Explain what the likely problem is AND how to correct the problem. (2)
[10]
QUESTION 7: SOCIAL IMPLICATIONS
7.1 Why would keylogger software not have any harmful effects if it is installed on a computer that is never networked or connected to the Internet? (1)
7.2 Green computing is every user's concern.
7.2.1 What is meant by the term green computing? (1)
7.2.2 Give TWO reasons why unwanted or disused ICT devices should NOT be thrown into a rubbish bin. (2)
7.3 State TWO potential ways in which telecommuting can be of benefit to an employer (a business owner). (2)
7.4 Explain what phishing is AND why updating your antivirus program will not prevent you from becoming a victim of phishing. (2)
7.5 State TWO ethical considerations to keep in mind when connecting to someone else's Internet connection. (2)
[10]
QUESTION 8: SOLUTION DEVELOPMENT
8.1 The following error message appears when trying to insert an automatic table of contents in a word processing document, even though styles have been added to the headings:
'No table of contents entries found'
Explain how you would fix this error. (1)
8.2 What is the best way to move a heading that appears in a column of text to the top of the next column in a word processing document? (1)
8.3 Name TWO word processing features that can be used to position text 'away from the margin', other than using the space bar. (2)
8.4 What is a bookmark AND how is it used in a word processing document? (2)
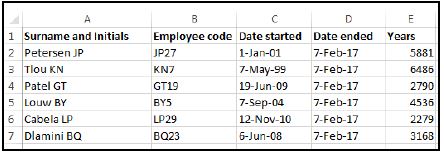
8.5 Study the extract from a spreadsheet below and answer the questions that follow.
8.5.1 The employee code in column B is created by combining the initials of the employee with a random number smaller than 30.
Name any TWO spreadsheet functions that could possibly have been used to create the employee codes. (2)
8.5.2 Column E should show the number of years that an employee has worked at the company.
The following formula was used in cell E2, but it gives the wrong
answer:
=D2-C2
Explain what the current values in column E represent AND state ONE way in which the correct answer could be displayed. (2)
8.6 Reports allow one to summarise and present data in a database.
8.6.1 Explain what the result of or answer to the following function in the report footer of a database report represents:
=Count([Pay])
NOTE: 'Pay' is a field in the database table that the report is based on. (2)
8.6.2 What would the function =Now() in the page footer of a database report display? (1)
8.7 In an HTML document the <b> tag was used to display the heading in bold. Give the most likely reason why the rest of the text below the heading also appears in bold. (1)
8.8 What is the most likely reason for a picture not to display in a browser, even if the correct HTML code was used? (1)
[15]
TOTAL SECTION B: 75
SECTION C: INTEGRATED SCENARIO
QUESTION 9
Your school is hosting a Science expo. Participants will be able to bring their own devices to demonstrate their projects. Internet access will be required for all participants and judges.
9.1 The most important part of the expo setup will be to share Internet access (provided by an ISP) with all the devices that will be used in the venue using the Wi-Fi facilities of the school.
9.1.1 State TWO advantages of using Wi-Fi to connect the devices in this situation. (2)
9.1.2 Some participants are too far away from the main venue to pick up the Wi-Fi signal. Suggest ONE technology they could use to still have 'wireless' Internet access without using Wi-Fi. (1)
9.1.3 Name TWO hardware components that might be needed to increase or expand the Wi-Fi coverage to all the locations used for the expo. (2)
9.1.4 Name TWO services an ISP can provide other than Internet access. (2)
9.1.5 What is the main reason for setting up and using an AUP in the context of Internet usage? (1)
9.1.6 People anywhere in the world can follow the expo by watching a live stream on a website. State TWO potential disadvantages of using live streaming. (2)
9.2 The organisers have been offered free use of online applications for the duration of the expo.
Explain TWO advantages of online applications compared to applications installed on the computers. (2)
9.3 The school has implemented a BYOD policy to allow participants to bring their own devices to access the network.
Outline ONE of the most likely technical problems that the school may encounter when the participants connect their devices. (1)
9.4 Participants and guests will vote for the projects at the expo.
The IT department has found an Android app to manage the voting. This app can be downloaded from the school's network server to cellphones and tablets of the participants and guests.
9.4.1 What is the general role of a server in any network? (1)
9.4.2 State TWO advantages for the guests of downloading the app from the school's network server as opposed to having to download the app from the app store. (2)
9.4.3 Many guests are concerned that the app may be a potential Trojan. What is a Trojan AND how is it typically installed? (2)
9.5 The organisers of the expo will use a computer to receive the votes from all the devices, and to collect and process all data of the expo.
Study the following specifications for the computer which will be used for these purposes:
|
9.5.1 How much permanent storage is available on the computer? (1)
9.5.2 The Windows 10 operating system was not installed on the 1 TB HDD.
On which device in the list above was the operating system loaded? (1)
9.5.3 Which component must be added to the list of specifications to enable the computer to connect to the school's network without using Wi-Fi? (1)
9.5.4 What change in specifications in the list above will have the biggest effect in terms of improving the overall performance of the computer? (1)
9.6 The following statement was made by one of the participants at the expo: 'Windows 10 has no option to turn off automatic system updates.'
9.6.1 Give TWO reasons for a software developer to release updates. (2)
9.6.2 Why would a software developer NOT give a user the choice to disable automatic updates? (1)
9.6.3 State ONE potential disadvantage of not being able to disable automatic updates. (1)
[26]
QUESTION 10
The organisers of the expo will be responsible for all managerial tasks at the expo, including registrations and the voting process.
10.1 State ONE potential disadvantage of using WhatsApp to promote the expo. (1)
10.2 One of the participants in the expo has done a study on information overload.
10.2.1 What is information overload? (1)
10.2.2 State TWO ways in which information overload can be reduced. (2)
10.3 Each participant in the expo needs to pay a registration fee a week before the expo starts.
10.3.1 Suggest TWO technologies that participants can use to pay the registration fee if they cannot get to the school or a bank during office hours. (2)
10.3.2 How could the organisers of the expo confirm that the registration fee has been paid, other than phoning the bank? (1)
10.4 An entry form for the expo is shown below.
Surname: | ||||||||||||||||||||
Initials: | Cell No: | |||||||||||||||||||
Expo Type: | XP1 | XP2 | XP3 | XP4 | XP5 | XP6 | XP7 | XP8 | XP9 | |||||||||||
e-mail: | ||||||||||||||||||||
Fax No: | Date: | YYYY | MM | DD | ||||||||||||||||
10.4.1 Explain why using a table format for the user to enter the cellphone number is a good idea. (1)
10.4.2 Suggest TWO ways in which to improve the layout of the form. (2)
10.5 All the data on the administration computer must be kept strictly confidential.
State TWO ways in which the organisers can be sure that the data on this computer cannot be stolen or accessed illegally, other than protecting it against physical theft. (2)
10.6 A database table was created to store the votes received. The table definition is shown below.
Field Name | Data Type | Description |
Name | Text | Name of the person voting |
Surname | Text | Surname of the person voting |
DOB | Date/Time | Date of birth of the person voting |
Date | Date/Time | Date on which the vote was cast |
Favourite Project | Text | Name of the project voted for |
10.6.1 Why is the DOB field not suitable to act as a primary key? (1)
10.6.2 Each project will receive a unique code which voters will use to vote in the Favourite Project field, e.g. Sci312.
Which database feature can be used to ensure that a user will have to enter three letters followed by three digits? (1)
10.6.3 Which database feature can be used to ensure that the Name and Surname fields are NOT left blank? (1)
10.6.4 Which database feature can be used to ensure that typing errors do not occur when data is entered in the Favourite Project field? (1)
10.7 A participant asked the organiser to make a printout of a document which he brought in on his flash drive. When trying to open the file with the 'Open With' option, the following dialog box appeared: 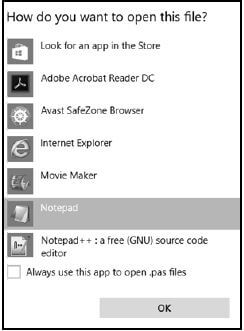
10.7.1 Explain why or when one would generally try to use the 'Open With' option to open a file. (1)
10.7.2 One of the options provided is the Adobe Acrobat Reader, which reads PDF files. Give TWO reasons for using the PDF file format. (2)
10.7.3 Why would one tick the check box towards the bottom left-hand corner of the dialog box? (1)
10.8 The following spreadsheet was created to keep track of paid registration fees: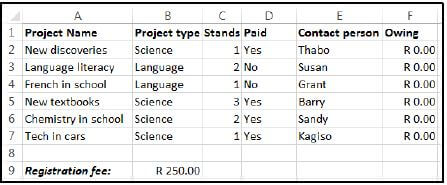
The following function was used in cell F2 and then copied down to the rest of the cells in column F:
=IF(D2="Yes",0,C2*B9)
The function should multiply the number of stands in column C with the registration fee in cell B9 if a 'No' is shown in column D.
10.8.1 Why is it better to use the cell reference B9 in the function instead of just the value of 250? (1)
10.8.2 The function returns the correct answer in cell F2.
Explain why the function is not calculating the correct amounts for some cells in column F AND rewrite the function so that it would copy down correctly. (2)
10.8.3 Explain if it would be possible to create a meaningful graph from the data in the range B2:B7. (1)
[24]
TOTAL SECTION C: 50
GRAND TOTAL: 150