INFORMATION TECHNOLOGY PAPER 2 GRADE 12 QUESTIONS - NSC PAST PAPERS AND MEMOS FEBRUARY/MARCH 2017
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINFORMATION TECHNOLOGY
PAPER 2
GRADE 12
NSC PAST PAPERS AND MEMOS
FEBRUARY/MARCH 2017
INSTRUCTIONS AND INFORMATION
- This question paper consists of SIX sections:
SECTION A:Short Questions (15)
SECTION B:Systems Technologies (25)
SECTION C:Communication and Network Technologies (20)
SECTION D:Data and Information Management (25)
SECTION E:Solution Development (27)
SECTION F: Integrated Scenario (38) - Read ALL the questions carefully.
- Answer ALL the questions.
- The mark allocation generally gives an indication of the number of facts/reasons required.
- Number the answers correctly according to the numbering system used in this question paper.
- Write neatly and legibly.
QUESTIONS
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1 Various options are provided as possible answers to the following questions. Write down the question number (1.1.1–1.1.10), choose the answer and make a cross (X) over the letter (A–D) of your choice in the ANSWER BOOK.
EXAMPLE:
1.1.11 ![]()
1.1.1 Which ONE of the following does NOT conform to sound network etiquette?
- Send short attachments in e-mails.
- Always add a subject in the subject line of an e-mail.
- Always perform a spell check on an e-mail before sending.
- Respond only to high-priority e-mail messages. (1)
1.1.2 Which ONE of the following is a technique that is classified as social engineering?
- Analysing a password by using a round-robin attack tool
- Acquiring a username by calling a person and posing as a system administrator
- Accessing a system by using software vulnerabilities, such as buffer overflow
- Using a backdoor to gain access to a system to restore data (1)
1.1.3 Which ONE of the following has the largest storage capacity?
- 200 KB folder
- 32 GB flash disk
- 2 TB hard drive
- 740 MB DVD (1)
1.1.4 Which ONE of the following represents access speed in descending order?
- Cache, RAM, hard disk, magnetic tape
- RAM, cache, magnetic tape, hard disk
- Magnetic tape, hard disk, RAM, cache
- RAM, cache, hard disk, magnetic tape (1)
1.1.5 A software company requires '1 GB RAM minimum and 2 GB RAM recommended' for its new operating system. Which ONE of the following will be the likely outcome of attempting to install the operating system on a computer with 1 GB RAM?
- Files will fail to save.
- Peripheral devices will not work.
- The computer will not function at its optimum performance.
- The operating system will fail to install. (1)
1.1.6 The acronym for the connection on the motherboard between the CPU and the RAM is …
- USB.
- FSB.
- ZIF.
- NIC. (1)
1.1.7 Which ONE of the following icons represents a network drive? 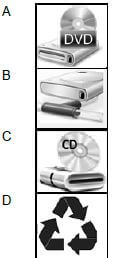
1.1.8 The correct conversion of D416 to a decimal number is …
- 212.
- 228.
- 77.
- 3 392. (1)
1.1.9 Which ONE of the following logic statements can be used to do a search for blue cars owned by a person with the surname Thomas or Moore?
- (CarColour = blue OR Surname = Thomas) OR Surname = Moore
- CarColour = blue OR (Surname = Thomas OR Surname = Moore)
- CarColour = blue AND (Surname = Thomas AND Surname = Moore)
- CarColour = blue AND (Surname = Thomas OR Surname = Moore) (1)
1.1.10 Which ONE of the following statements will calculate the bonus of a staff member correctly, if all staff members get a R100 bonus and a further 2% of their salary for each year of service?
- Bonus = Salary * 0.02 + YearsOfService + 100
- Bonus = (100 + YearsOfService) * Salary * 0.02
- Bonus = YearsOfService * Salary + 100 * 0.02
- Bonus = 100 + YearsOfService * Salary * 0.02 (1)
1.2 Give ONE word/term for each of the following descriptions. Write only the word/term next to the question number (1.2.1–1.2.5) in the ANSWER BOOK.
1.2.1 Copyright license that allows you to use, copy and distribute parts of published work for non-profit purposes (1)
1.2.2 An international community that develops open standards to ensure the long-term growth of the Web (1)
1.2.3 Companies that pay workers to repeatedly click on website elements to artificially increase or boost the status of a product or web page (1)
1.2.4 Increasing the speed of the system bus/clock, hence increasing the speed of all components of a computer system to enhance the performance (1)
1.2.5 The execution of physical tasks by computer-controlled machines rather than by human beings (1)
TOTAL SECTION A: 15
SCENARIO The IT class will be hosting a computer games evening as part of a fundraising campaign for the school. The gamers will be required to bring in their own computers and other devices for the evening. The computers and other devices used for the evening must meet certain basic hardware and software requirements to be used effectively for the selected games. |
SECTION B: SYSTEMS TECHNOLOGIES
QUESTION 2
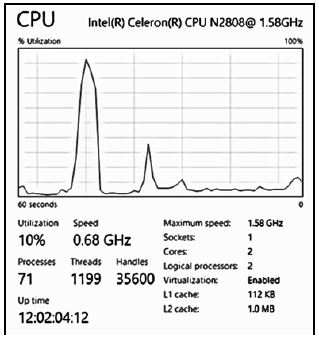
2.1 One of the gamers enquired whether or not his computer had sufficient capacity to be used for a specific game.
In the task manager of the computer system the performance of the CPU is indicated with the image below. Answer the questions that follow based on the information in the image.
2.1.1 Briefly explain what 'Threads' refers to in terms of processing when a program is executed. (2)
2.1.2 At the time when the image was captured, the operating system managed 71 active processes. Explain what process management, as executed by the operating system, entails. (2)
2.1.3 The speed of the processor with two cores is 1.58 GHz. Does the presence of two cores mean that tasks will be processed at double the speed of the CPU, that is 3.16 GHz? Explain your answer. (2)
2.1.4 The image indicates the sizes of L1 and L2 cache memory.
- What is cache memory? (2)
- What is the purpose of caching? (2)
2.2 One of the gamers asked your opinion on the upgrading of the hard drive of his computer. He wants you to explain the image below, which was part of an advertisement.
2.2.1 What does the abbreviation SSD stand for? (1)
2.2.2 Explain why the following will be features of an SSD:
- Silent operation (1)
- Faster performance (1)
2.2.3 All the system software, programs, data and more than one TB of music and videos are saved on the gamer's current hard disk.
He plans to keep the current hard drive and to add an SSD.
Suggest, with reasons, the best way to configure the computer to use the disks optimally. (4)
2.3 Gamers were advised to update the antivirus software on their computers. Why is it necessary to always keep the antivirus software up to date? (2)
2.4 The motherboards of the computers normally used by gamers have high-performance video cards slotted into the expansion slots.
2.4.1 Name the expansion slot provided for a video card. (1)
2.4.2 Explain why most modern laptop computers have a built-in (or integrated) video adaptor as well as a video card. (2)
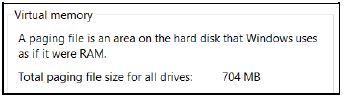
2.5 The performance of a computer used for gaming is important. When opening the performance window, the following is displayed:
2.5.1 When will the operating system use virtual memory? (1)
2.5.2 Does the availability of virtual memory mean that adding more RAM to the computer system to improve the performance is no longer necessary? Motivate your answer. (2)
TOTAL SECTION B: 25
SECTION C: COMMUNICATION AND NETWORK TECHNOLOGIES
QUESTION 3
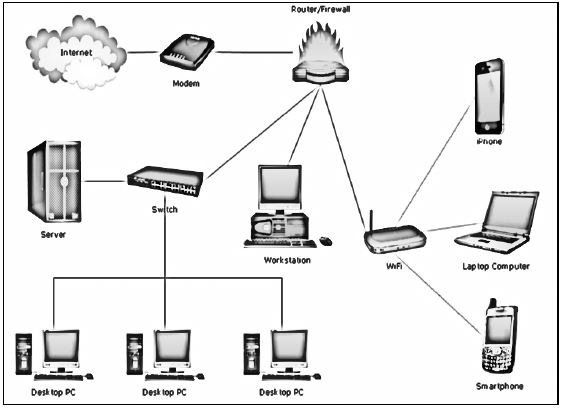
Players who registered for the online gaming event can use any device and can play from any location worldwide. Below is a representation of the different ways communication could take place while playing the games.
3.1 Gamers at the school will link their desktop and laptop computers into a LAN that will be set up in the school hall.
3.1.1 Give TWO reasons why UTP cables will be the most suitable type of cable to connect the computers in the school hall. (2)
3.1.2 Explain why the school LAN would require both a router and a switch by referring to the function of each device. (3)
3.1.3 Explain the purpose of TCP/IP in a LAN setup. (2)
3.2 Different types of communication will take place using different types of media during the gaming event.
3.2.1 What type of network would use a 3G modem? (1)
3.2.2 One of the media types used for wireless communication in networks is radio waves. Name TWO other types of wireless media used in networks. (2)
3.3 Gamers will be required to locate at least one Pokémon at some stage during the gaming event. To take part in the Pokémon GO location-based augmented reality game, a mobile device with GPS technology is required.
3.3.1 What does the abbreviation GPS stand for? (1)
3.3.2 Briefly explain how a GPS can determine your physical position. (2)
3.4 Online media stores, like iTunes and Amazon, that provide the facility of media repositories, will be used to play music in the school hall during the event.
3.4.1 Explain what a media repository is in this context. (2)
3.4.2 Why is it acceptable to use this type of repository for music files, but not for video files? (2)
3.5 The IT learners have been tasked to investigate RIA as a possible feedback mechanism to evaluate the success of the event.
3.5.1 Briefly describe what an RIA is. (2)
3.5.2 Give ONE example of a well-known RIA. (1)
TOTAL SECTION C: 20
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
A database will be used to store the details of the participants and to keep a record of the games played.
The following tables have been designed for the database:
tblPlayers | ||
Key | FieldName | DataType |
PlayerID | Text | |
PName | Text | |
PSurname | Text | |
tblGames | ||
Key | FieldName | DataType |
GameID | Text | |
GameTitle | Text | |
GameMaker | Text | |
tblGamesPlayed | |||
Key | FieldName | DataType | Description |
GameNumber | Number | A unique number allocated for each game played in sequence starting from 1 | |
GameID | Text | The ID of the game that was played | |
PlayerID | Text | The ID of the player who played the game | |
TimePlayed | Date/Time | The starting time of the game | |
Score | Number | The score the player obtained for the game | |
Example of data from the tblPlayers table:
PlayerID | PName | PSurname |
X782 | Yeng | Xu |
D901 | Marilyn | Fredriks |
F566 | Loyiso | Nkosi |
G639 | Lenny | Govender |
Example of data from the tblGames table:
GameID | GameTitle | GameMaker |
G101 | Arche Adventure | Lee Andrew |
G102 | 3D Electro Sim | Kernal Yen |
G103 | Car frenzy | Ney Abramo |
G104 | Shadow Impact | Jian Shume |
Example of data from the tblGamesPlayed table:
GameNumber | GameID | PlayerID | TimePlayed | Score |
1 | G102 | D901 | 09:45 | 156 |
2 | G104 | X782 | 10:06 | 567 |
3 | G102 | F566 | 12:57 | 233 |
4 | G103 | X782 | 13:23 | 134 |
4.1
4.1.1 What is the term given to the GameID field in the tblGamesPlayed table? (1)
4.1.2 How many games will each player be able to play per day based on the construction of the database? Choose the answer from the options (A–C) provided below.
- One game per day
- Two games per day
- Any number of games per day (1)
4.1.3 The following message is displayed when attempting to delete the player with PlayerID F566 from the tblPlayers table: ![]()
- Explain why this message is displayed. (2)
- State a possible solution to delete a record from the tblPlayers table successfully. (2)
4.2 Write SQL statements for EACH of the following queries, using the tables provided:
4.2.1 Display all details of the games played from 12:00 to 15:00. (4)
4.2.2 The scores for games with GameID G103 were processed incorrectly. All scores for records with this GameID must be increased by 15%. (4)
4.3 The following SQL statements were given to the administrator to interpret:
4.3.1 Explain what will be the output of the following SQL statement:
SELECT GameID, MAX(Score) as Maximum
FROM tblGamesPlayed
Group by GameID
Order by Max(Score) DESC (3)
4.3.2 Write down the output of the SQL statement given below, using the tblPlayers table and the first record from tblGamesPlayed table.
SELECT GameNumber, Left(PName,1) & Left(PSurname,1) & Right(PSurname,1) & "-" & Score AS Reference
FROM tblPlayers, tblGamesPlayed
WHERE tblPlayers.PlayerID = tblGamesPlayed.PlayerID (4)
4.4 It has been suggested that an ID number field and a date of birth field should be included in the tblPlayers table. Explain why adding the suggested fields to the tblPlayers table will result in data redundancy. (2)
4.5 The school needs to take measures to ensure that the player and game information stored in the database will not be compromised. State TWO ways of preventing an SQL injection attack on the database by hackers. (2)
TOTAL SECTION D: 25
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
The IT learners will write application programs to assist with organising the gaming event and processing information.
5.1 The following data structures can be used in the application programs:
- One-dimensional array
- Two-dimensional array
- Variable
- Text file
Which ONE of the data structures above will be the most suitable to use in EACH of the following cases?
NOTE: Each data structure from the list above can be used once only as an answer.
5.1.1 A large amount of data about the participants needs to be saved to be used at a later stage. (1)
5.1.2 An alphabetically-sorted list of names of the organisers is required. (1)
5.1.3 The scores of participants need to be stored in rows and columns. (1)
5.1.4 Find the name of the player who achieved the highest score. (1)
5.2 Two object classes need to be designed: one for the players and one for the games.
5.2.1 Object-orientated programming uses encapsulation. Give the definition of encapsulation. (2)
5.2.2 State TWO advantages of using object-orientated programming when multiple developers are involved in coding an application. (2)
5.2.3 Indicate whether the following statements about object-orientated programming are TRUE or FALSE. Write down only 'true' or 'false' next to the question number (5.2.3(a) and 5.2.3(b)).
- More than one object of a class can be instantiated. (1)
- The number of parameters received by a constructor must always be the same as the number of private attributes. (1)
5.3 In one of the games played, the user needs to enter the number of rows of a figure. The figure is made up of a sequential list of numbers starting from the value of 1 and must contain the number of rows that was entered. Each row in the figure will have 2 x (row number) – 1 number of numbers.
Example of output if the value of 5 has been entered. 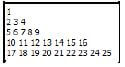
Write a solution to the problem in the form of pseudocode.
NOTE:
- The number of numbers per row can be calculated using the formula 2 x (row number) – 1.
- There is one number in row 1, three numbers in row 2, five numbers in row 3 and so on. (10)
5.4 Another part of the game requires that a random number in the range of 4 to 50 be generated. Determine whether the number generated randomly is a perfect number, or not.
NOTE: A perfect number is when the number is equal to the sum of the factors of the number, excluding the number itself.
Example:
The number 6 was randomly generated.
The sum of the factors of 6, excluding 6, is: 1 + 2 + 3 = 6
The number 6 is therefore a perfect number.
The following pseudocode was given to solve the problem:
| Row Instruction |
|
5.4.1 Use the following headings and complete the trace table with the number 4 as the randomly generated number. Show EACH step of your trace.
number | sum | Loop index | number modulus index = 0? | number = sum? | Display |
| 4 |
(5)
5.4.2 One of the players presented an alternative solution. The suggestion is that line 3 of the solution should read as follows:
3. Loop index from 1 to num
In order to display the same results as in QUESTION 5.4.1, one other line in the pseudocode would need to be changed as well.
Indicate the line number and the edited contents of this line to provide the same output as the given solution. (2)
TOTAL SECTION E: 27
SECTION F: INTEGRATED SCENARIO
QUESTION 6
The school will host a website and be a part of a social network to allow for players to register and to play games online. |
6.1 One of the players sent an e-mail with the following e-mail address to the organisers:
This email address is being protected from spambots. You need JavaScript enabled to view it.
6.1.1 State the domain name of the e-mail. (1)
6.1.2 Name the e-mail recipients below that will not be disclosed in the e-mail to others. 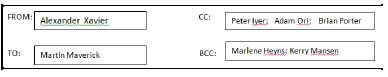 (1)
(1)
6.1.3 What is the general name of malware that refers to the forging of an e-mail header, so that the e-mail appears to originate from a different source? (1)
6.2 The host school has a website with SSL where participants can register and make the required payments.
6.2.1 Explain what SSL is. (2)
6.2.2 A digital certificate will be accessible to the browser to verify the website from which the school wants to download the game. State TWO pieces of information that can be found on a digital certificate. (2)
6.3 The games administrator wants to archive certain files on the server to free up disk space.
6.3.1 Explain what is meant by archiving files. (2)
6.3.2 Will more disk space be saved if archived files are moved from a physical server to a virtual server? Motivate your answer. (2)
6.4 At a previous gaming event gamers complained that too much bandwidth was used while streaming games.
6.4.1 For the current gaming event gamers were informed that they can configure the settings on their computers to optimise game play. Explain what can be done to save bandwidth while streaming. (1)
6.4.2 The gamers want to restrict the websites that can be accessed in order to reduce network traffic. Explain how a firewall could be used for this purpose. (2)
6.4.3 Why is it usually quicker to use BitTorrent protocol to download a file rather than downloading the file directly from a server? (2)
6.4.4 Someone mentioned that BitTorrent protocol should be avoided as it is illegal to use. Is this statement true? Motivate your answer. (2)
6.5 The IT learners will make gamers aware of the NFC (near field communication) feature that is available on their tablets and other hand-held devices. 
6.5.1 Explain what near field communication (NFC) means. (2)
6.5.2 NFC originated from a communication standard that uses radio waves. What is this communication standard called? (1)
6.6 Separate versions of some of the gaming software applications have been developed to provide for different operating systems, such as Android and IOS.
6.6.1 Motivate why the same application needs to be programmed differently for different operating systems. (2)
6.6.2 An important feature of an operating system is backward compatibility. Use an example to explain the concept of backward compatibility. (2)
6.7 During an interview with the author of one of the games, the response to a question on the features of a successful online game was as follows:
'Scalability, fast response time, security and low cost to set up'
6.7.1 Why is scalability important when designing online games? (2)
6.7.2 Why will security be a challenge for a peer-to-peer network? (1)
6.8 'The "app-ification" of the Web' has seen many well-known websites developing apps that people can use to access the information on their websites.
6.8.1 Briefly explain what an app is. (1)
6.8.2 Give TWO reasons why gamers wanting to register for the gaming event might prefer to use an app instead of the website. (2)
6.9 One of the gamers will use the headset in the illustration below. 
[Source: http://www.bestbuy.com/site/ video-games-accessories/gaming-headset]
6.9.1 Many of these types of devices contain firmware. Explain what firmware is. (2)
6.9.2
- The headset supports plug-ins. Explain what a plug-in is. (1)
- How does the fact that the headset supports plug-ins benefit the gamer? (1)
6.9.3 These types of devices normally contain sensors. Name TWO possible types of sensors found on gaming devices. (2)
6.9.4 What is the field called when a computer system simulates human decision-making and reacts on the basis of input gained from sensors? (1)
TOTAL SECTION F: 38
GRAND TOTAL: 150