INFORMATION TECHNOLOGY PAPER 2 GRADE 12 QUESTIONS - NSC PAST PAPERS AND MEMOS FEBRUARY/MARCH 2016
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINFORMATION TECHNOLOGY P2
FEBRUARY/MARCH 2016
NATIONAL SENIOR CERTIFICATE
GRADE 12
INSTRUCTIONS AND INFORMATION
- This question paper consists of SIX sections:
SECTION A:Short questions (15)
SECTION B:Systems Technologies (24)
SECTION C:Communication and Network Technologies (25)
SECTION D:Data and Information Management (27)
SECTION E:Solution Development (25)
SECTION F:Integrated Scenario (34) - Read ALL the questions carefully.
- Answer ALL the questions.
- The mark allocation generally gives an indication of the number of facts/reasons required.
- Number the answers correctly according to the numbering system used in this question paper.
- Write neatly and legibly.
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1 Give ONE word/term for each of the following descriptions. Write only the word/term next to the question number (1.1.1–1.1.10) in the ANSWER BOOK.
1.1.1 A company that has a permanent, fast connection to the Internet and sells Internet access and services at a monthly fee (1)
1.1.2 Initiatives to design, use and dispose of technology in an environmentally friendly way (1)
1.1.3 A series of steps that need to be followed when designing a database to ensure that no data redundancy occurs (1)
1.1.4 Software that is stored permanently on the ROM chip of a device, such as a printer, to control the basic operation of the device (1)
1.1.5 A protocol used for the transfer of large files between computers by means of an Internet connection (1)
1.1.6 Software that translates programming instructions written in a high-level language into a file with an '.exe' extension that can be run independently of the programming language (1)
1.1.7 A field of study that involves simulation of human decision-making processes by a computer system that is programmed to react on input received from sensors (1)
1.1.8 This component generates pulses at regular frequencies to control the activities of the motherboard (1)
1.1.9 A technology used by devices to automatically give a notification that a new message has arrived (1)
1.1.10 The key field in a database table that links to the primary key in another database table in order to create a relationship between the two tables (1)
1.2 Various options are provided as possible answers to the following questions. Choose the answer and write only the letter (A–D) next to the question number (1.2.1–1.2.5) in the ANSWER BOOK, for example 1.2.6 E.
1.2.1 The concept of packaging data and procedures into a single object to prevent access from outside the object is called …
- an object code.
- encapsulation.
- an object program.
- a control structure. (1)
1.2.2 This type of test is performed by end-users and focuses on the functionality of a system and the validation of the fitness for use:
- Integration
- Systems
- Unit
- Acceptance (1)
1.2.3 A range check ...
- ensures that users enter only alphabetic data into a field.
- determines whether the data entered is within a fixed set of values.
- ensures that users enter only numeric data into a field.
- verifies that a required field contains data. (1)
1.2.4 The deliberate disruption of computer access to an Internet service such as the Web or e-mail by overloading the network with a large number of requests is known as a …
- zombie.
- virus hoax.
- trojan horse.
- denial-of-service attack.
1.2.5 Determine the number of times the instructions inside the nested loop below will be executed:
Loop with counter1 from 1 to 4
Loop with counter2 from (counter1 + 1) to 5
Instructions to be executed
End loop
End loop
- 10
- 20
- 12
- 9 (1)
TOTAL SECTION A: 15
| SCENARIO At the end of each year your school updates the stock registers for all departments. The IT learners have been asked to help with the stocktaking process. |
SECTION B: SYSTEMS TECHNOLOGIES
QUESTION 2
The laptop computer used by the Mathematics department for stocktaking purposes has the following technical specifications and software installed:
| 15.6" 360º rotating touch-screen monitor Core i7 4510U 3.1 GHz processor 8 GB DDR3 RAM 1 TB 7200 rpm HDD USB 3.0 port and USB 2.0 port HDMI port and an SD card reader RJ45 LAN jack and Gigabit Ethernet Bluetooth 4.0 Integrated graphics processor Windows 8.1 operating system Instant-on functionality |
2.1 Explain why each of the following components is essential for the functioning of any computer:
2.1.1 ROM (1)
2.1.2 RAM (1)
2.2 State ONE advantage of a touch-screen monitor. (1)
2.3 State ONE disadvantage of using a mechanical/conventional hard disk drive (HDD) in a laptop computer. (1)
2.4 Windows 8.1 is the operating system on the laptop computer. 2.4.1
State TWO aspects of memory management that the operating system is responsible for. (2)
2.4.2 State TWO other functions (except memory management) of the operating system. (2)
2.5 There is no DVD drive in the specifications above.
Give a reason why DVD drives are no longer included in modern devices. (1)
2.6 What is the purpose of the Ethernet port? (1)
2.7 What effect would the use of a separate graphics processor have on the functioning of the laptop computer? (1)
2.8 A flash disk is normally plugged into a USB port.
2.8.1 How will a flash disk communicate that it requires the attention of the operating system? (1)
2.8.2 Explain why a flash disk is known as a plug-and-play device. (2)
2.9 Cache memory is found on, or near, the CPU in a computer.
2.9.1 What is the purpose of cache memory? (2)
2.9.2 Briefly explain what disk caching is. (2)
2.10 ScanDisk, that checks the hard drive for errors, is an example of utility software on a computer.
2.10.1 Explain the term utility software. (2)
2.10.2 Give an example of utility software that rearranges the files on a disk for faster retrieval. (1)
2.11 Many applications use complex graphics that require a large amount of RAM storage when executed.
Explain how virtual memory is used to allow large applications to be executed. (3)
TOTAL SECTION B: 24
SECTION C: COMMUNICATION AND NETWORK TECHNOLOGIES
QUESTION 3
| The school has set up a network for all classrooms and computer centres in the building. There is a computer in each classroom and each computer centre has 40 computers linked in a network. |
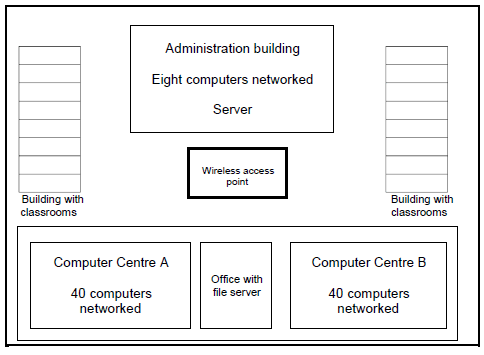
3.1 Motivate the setup of the network by answering the following questions:
3.1.1 What is the primary function of a file server? (1)
3.1.2 A star topology is used in the computer centres.
- Describe the term topology. (1)
- State TWO advantages of a star topology.(2)
- Name ONE network device that is an essential part of a network using a star topology. (1)
3.1.3 Each computer needs an NIC to be part of the cabled network.
What is the specific role of the NIC in a network, other than connecting the cables to the computer? (1)
3.1.4 The following Internet protocol (IP) address has been assigned to one of the computers in Computer Centre A:
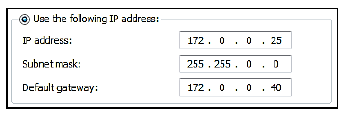
(a) What is an IP address?(1)
(b) Why should another computer on the same network (LAN) not be assigned the same IP address? (1)
3.2 The server in the administration building is connected to an ADSL Internet line with a 2 Mbps connection speed. The data package used by the school can either be capped or uncapped.
3.2.1 Explain the meaning of the term data cap. (1)
3.2.2 The administration staff is complaining about the low bandwidth of the connection.
What does bandwidth refer to? (1)
3.3 A wireless access point has been installed in the middle of the school grounds (see diagram on previous page) to enable the computers in the classrooms to share the Internet connection with the administration building.
3.3.1 Explain a possible problem with sharing the Internet access. (2)
3.3.2 Due to the poor Internet connection, some teachers requested to have a 3G connection in their classrooms.
What would be a disadvantage of using a 3G connection? (1)
3.4 Stock data is available online to the learners who are helping with the stocktaking process.
3.4.1 State TWO advantages of storing data online rather than locally on a hard drive. (2)
3.4.2 Which technique is used to ensure that all the devices have access to the most up-to-date information when stored data is shared between devices? (1)
3.5 With Internet access available on the school grounds, learners are using e-mail facilities, downloading educational material and attending online lessons. All these services use specific protocols.
3.5.1 What is a protocol? (1)
3.5.2 Differentiate between a POP3 and an SMTP protocol. (2)
3.5.3 VoIP is also used when lessons are presented over the Internet.
State TWO implications/disadvantages of using VoIP. (2)
3.6 The table below shows some network vulnerabilities and ways/techniques to solve or prevent these problems.
Choose a solution/preventative measure from COLUMN B that matches the network vulnerability in COLUMN A. Write only the letter (A–F) next to the question number (3.6.1–3.6.4) in the ANSWER BOOK, for example 3.6.5 antispam.
| COLUMN A: NETWORK VULNERABILITY | COLUMN B: SOLUTION/PREVENTION |
3.6.1 Trojan applications that install themselves on the system 3.6.2 Hacking into the system from outside the network 3.6.3 Unexpected breaks in the power supply 3.6.4 Get access to confidential information which is sent across the Internet |
|
(4 x 1) (4)
TOTAL SECTION C: 25
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
A central database has been created for the school to record the stock items of each department during the stocktaking process.
4.1 The following tables have been designed for the database:
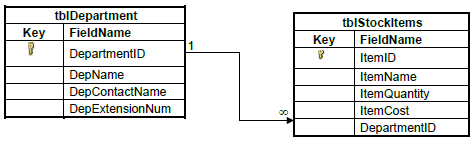
Example of data in the tblDepartment table:
| tblDepartment | |||
| DepartmentID | DepName | DepContactName | DepExtensionNum |
| D12 | Afrikaans | Mrs De Bruin | X201 |
| D15 | History | Mr J Pillay | X206 |
| D16 | Civil Technology | Mr K Mahlangu | X214 |
Example of data in the tblStockItems table:
| tblStockItems | ||||
| ItemID | ItemName | ItemQuantity | ItemCost | DepartmentID |
| A1 | Desktop MN073X | 4 | R2500 | D12 |
| B2 | Laptop HP 64 bit | 3 | R8000 | D17 |
| B4 | Laptop Acer 32 bit | 5 | R4500 | D06 |
| C5 | Printer HP F370M | 2 | R2090 | D12 |
| D6 | Scanner LG253 | 1 | R1050 | D11 |
| B5 | Laptop Computer Lenovo i5 | 1 | R6300 | D16 |
NOTE:
- The ItemQuantity field refers to the number of items for each item indicated in the ItemName field.
- The ItemCost field refers to the cost of a single item.
4.1.1 Suggest a suitable data type for the ItemCost field. (1)
4.1.2 Use the data in the tables (on the previous page) and give an example that explains the one-to-many relationship that exists between the tblDepartment and the tblStockItems tables. (2)
4.1.3 Write SQL statements for each of the following queries:
- Display all details from the tblStockItems table sorted in alphabetical order by ItemName. (3)
- An HP F370M printer of the Afrikaans department (D12) was left off the stock list and must be included.
Change the existing number of printers for this specific department by updating the quantity.(4) - Display the department name and the total stock value for each department in a new field called TotalValue. (6)
4.1.4 An incomplete SQL statement that displays a list of all the laptop computers and the number of laptop computers is given below.
| SELECT ItemName, ItemQuantity FROM tblStockItems WHERE ___(a)___ |
Write only the missing code at (a) to complete the statement. (2)
4.2 Due to the number of people who need access, the database has been moved from a stand-alone desktop to a server. DBMS software was installed on the server to handle access to the database.
4.2.1 Expand the acronym DBMS. (1)
4.2.2 Name TWO actions that the DBMS software allows the user to perform on the data in the database. (2)
4.3 Larger businesses will use a database distributed over several servers.
4.3.1 Give TWO reasons why it might not be feasible to have a larger number of users accessing a single database on a single server. (2)
4.3.2 Name TWO models that can be used for data synchronisation in a distributed database. (2)
4.3.3 Explain how transaction processing ensures data integrity in a distributed database model. (2)
TOTAL SECTION D: 27
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
| The IT learners are writing programs to assist with the stocktaking process. |
5.1 A two-dimensional array called arrStock has been used to record the quantities of the four items for the four departments, as shown in the table below.
NOTE: The array contains only the values shown in the table below.
| Afrikaans | History | Tourism | Design | Total | |
| Desktop | 4 | 0 | 12 | 0 | |
| Laptop | 0 | 2 | 1 | 5 | |
| Printer | 2 | 1 | 1 | 0 | |
| Scanner | 0 | 1 | 0 | 1 |
Write pseudocode to calculate the total stock per item and store these values in the array. (5)
5.2 Various errors can occur while coding and executing a program.
5.2.1 The three common types of errors are syntax, logical and runtime errors.
Identify the type of error for each process in the table below. Write down only the correct answer next to the question numbers (5.2.1(a)–5.2.1(c)).
| TYPE OF ERROR | ERROR | ERROR MESSAGE |
| (a) | No semicolon entered at the end of an instruction | Missing semicolon |
| (b) | The stock value is calculated incorrectly as stockValue = quantity – itemPrice | No error message |
| (c) | A variable is created as an integer data type to store the number of items. When the program runs, the user enters the word 'seventeen' instead of the number 17 in the GUI component. | Data-type mismatch |
(3)
5.2.2 When writing methods, parameters are sometimes used to obtain values from the calling statement.
Name TWO aspects that must be taken into consideration when providing the arguments (actual parameters) in a call statement. (2)
5.3 Each line of the text file called StockDetails.txt is used to store the room number, the description of the items and the quantity of the stock item issued to the room.
The format of the data in each line of the text file is as follows:
<Room number>;<Description>#<Quantity Issued>
Example of data in the text file:
101;Laptop#5 : |
5.3.1 The following incomplete algorithm has been supplied:
| 1.Open the text file StockDetails.txt for reading 2. Counter ← 0 3.Loop until the end of the StockDetails.txt file 4.… |
The number of tablets and the room numbers where the tablets are used must be stored in two parallel arrays.
Complete the algorithm to read the text file and populate the arrays with the room numbers and the stock quantity of tablets issued to those room numbers.
NOTE: Do NOT rewrite the first three statements of the algorithm. (6)
5.3.2 Although the text file was created and the filename was spelt correctly, when trying to access the file from another program the following message was displayed:
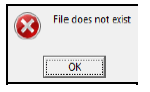
Give a possible reason why this message was displayed. (1)
5.4 The following pseudocode was given to develop a program that must generate four numeric values:
arrNumbers is declared as an array that can store the four numeric values as integer values.
j←1 Loop from first position of array to last position of array k←square(j) arrNumbers[loop counter] ←number of values + k if j modulus 2=0 then arrNumbers[loop counter] ← round(arrNumbers[loop counter -1]/3) j←j+1 |
NOTE: The modulus operation gives the remainder as a result of division by an integer.
Redraw and complete the trace table below to determine the four numeric values in the arrNumbers array if number of values has a value of 4.
| number of values | j | loop counter | k | j modulus 2 = 0? | arrNumbers[loop counter] |
| 4 | |||||
(8)
TOTAL SECTION E: 25
SECTION F: INTEGRATED SCENARIO
QUESTION 6
| The learners who are helping with stocktaking are using their own mobile devices to record data and to communicate with each other and the administrators. |
6.1 Surveillance cameras and other mechanisms have been installed in the school buildings as part of the security process to monitor all the stock.
6.1.1 Name TWO security techniques that the school could implement to provide access control to the server room. (2)
6.1.2 The Mpeg 4 compression standard used for the recorded security videos uses lossy compression.
- Explain the benefit of using compression. (2)
- Briefly explain what lossy compression entails. (1)
6.1.3 The administrators used an audit trail to keep track of the stock throughout the year.
- Explain what an audit trail is. (1)
- Name TWO types of information that should be recorded for audit purposes. (2)
6.2 Encryption is used when data about stock values are communicated over the Internet.
6.2.1 What does it mean to encrypt data? (2)
6.2.2 A technique such as SSL uses public/private key encryption.
Briefly explain the difference between the public key and private key in this security standard. (3)
6.3 The school principal wants to be able to access security video footage after school hours from his home. School staff members and security personnel from outside the school also need access to this material.
6.3.1 Suggest TWO different techniques that will make secure access to the server containing the security video footage possible. (2)
6.3.2 Differentiate between an intranet and an extranet. Also, indicate who would be included in an intranet and an extranet in this context. (2)
6.4 Learners spend a lot of time using their mobile devices to do stocktaking.Suggest TWO ways in which the learners can extend the battery life of their mobile devices while they are using these devices. (2)
6.5 Some of the stock items have been fitted with RFID tags.
6.5.1 Briefly explain what RFID technology is. (2)
6.5.2 State TWO advantages of using RFID technology when doing stocktaking. (2)
6.6 Bluetooth technology is used to transfer the data from the mobile devices to the data server.
6.6.1 Explain what Bluetooth technology is. (2)
6.6.2 Give ONE reason why Bluetooth is a suitable technology to use in this case. (1)
6.7 The database administrator has decided to rent a server from a cloud-based service in which to store the stock database.
6.7.1 To what does a cloud-based service refer?(1)
6.7.2 Using cloud-based services is a form of outsourcing.
Explain what outsourcing is in this context. (2)
6.7.3 State TWO benefits for the school if they were to outsource the data server. (2)
6.7.4 Companies that provide cloud services split the resources of a powerful machine between users to make it appear as if each user has access to his/her own web server.
What is this technique called? (1)
6.7.5 State TWO duties of the database administrator. (2)
TOTAL SECTION F: 34
GRAND TOTAL: 150