INFORMATION TECHNOLOGY PAPER 2 GRADE 12 QUESTIONS - NSC PAST PAPERS AND MEMOS FEBRUARY/MARCH 2018
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINFORMATION TECHNOLOGY
PAPER 2
GRADE 12
NSC PAST PAPERS AND MEMOS
FEBRUARY/MARCH 2018
INSTRUCTIONS AND INFORMATION
- This question paper consists of SIX sections:
SECTION A: Short Questions (15)
SECTION B: Systems Technologies (24)
SECTION C: Communication and Network Technologies (24)
SECTION D: Data and Information Management (25)
SECTION E: Solution Development (23)
SECTION F: Integrated Scenario (39) - Answer ALL the questions carefully.
- Read ALL the questions.
- The mark allocation generally gives an indication of the number of facts/reasons required.
- Number the answers correctly according to the numbering system used in this question paper.
- Write neatly and legibly.
QUESTIONS
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1 Various options are provided as possible answers to the following questions. Choose the answer and write only the letter (A–D) next to the question number (1.1.1–1.1.5) in the ANSWER BOOK, for example 1.1.6 D.
1.1.1 Rooting and jail breaking have the following effect on devices:
- Prevents malicious programs from being installed
- Freezes the software installed on the device
- Voids the manufacturer's warranty
- Causes a virus to be installed on the device (1)
1.1.2 What would be the effect on the network in the diagram below if one of the computers malfunctioned?
- The entire network will malfunction.
- The network will function as normal, excluding the faulty node.
- All the nodes will need to be replaced.
- The server will need to be replaced. (1)
1.1.3 Which ONE of the following will indicate that the motherboard battery has failed?
- Operating system passwords are lost.
- Files on the hard disk are lost or corrupted.
- Virtual memory on the hard disk is not accessible any longer.
- Hardware settings, including the current date and time, revert to default values. (1)
1.1.4 Which ONE of the following statements will NOT give the result of 10?
- 64 div 6
- Floor (64/6)
- Trunc (64/6)
- 64 mod 6 (1)
1.1.5 Which set of initial values assigned to variables L and N will result in the while-loop never being executed?
L ? ..
N ? ..
While (L < 2) OR (N < 5) do
…
end loop
- L = 1 and N = 5
- L = 2 and N = 4
- L = 2 and N = 5
- L = -2 and N = -5 (1)
1.2 Give ONE word/term for each of the following descriptions. Write only the word/term next to the question number (1.2.1–1.2.10) in the ANSWER BOOK.
1.2.1 Programs that are part of system software and do maintenance and administrative tasks (1)
1.2.2 The most common protocol used for downloading e-mail via the Internet (1)
1.2.3 A technology strategy used to obtain a high-ranking placement in the search results page of a search engine, such as Google (1)
1.2.4 A peer-to-peer protocol used to transfer and share large files across a network, such as the Internet (1)
1.2.5 A fixed physical address containing minimal office setup, which is used as shared space by people who work from a mobile office (1)
1.2.6 Specialised software and hardware designed to be used at a till point (1)
1.2.7 The combination of more than one field to identify a record in a database table uniquely (1)
1.2.8 A permanent digital connection to the Internet using a telephone line (1)
1.2.9 Compressing data by sacrificing some insignificant portions of the data (1)
1.2.10 A central registry that keeps track of all the URLs on the Internet (1)
TOTAL SECTION A: 15
SECTION B: SYSTEMS TECHNOLOGIES
QUESTION 2
In the first round of the Computer Olympiad, the participants are expected to have some knowledge of system technologies.
2.1 One of the functions of the motherboard is to provide connectors which allow components to be connected to the computer.
Name TWO other functions of a motherboard. (2)
2.2 Name ONE device that is connected to an expansion slot on the motherboard. (1)
2.3 EEPROM is a special type of PROM that can be electronically erased.
2.3.1 What is the software called that is saved on an EEPROM? (1)
2.3.2 What is the process called that involves the overwriting of existing data contained in EEPROM? (1)
2.4 Many laptop computers have an integrated video adaptor and a video card.
2.4.1 What does the term integrated refer to in this context? (1)
2.4.2 Explain why a laptop computer may have both an integrated video adaptor and a video card by referring to the different functions and its use of resources. (2)
2.5 'Cache' is a computer term that is often referred to when discussing the performance of a computer.
2.5.1 Explain the purpose of caching. (2)
2.5.2 When the Delphi text editor is closed and then opened again, it opens up much faster the second time. Give a detailed explanation of why the program opens up much faster the second time. (2)
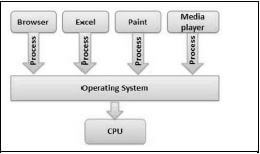
2.6 Operating systems use different processing techniques to handle many tasks at the same time.
2.6.1 Identify each of the processing techniques illustrated below.
 (1)
(1) (1)
(1)
2.6.2 Explain how an operating system working with a multicore processor incorporates the processing techniques above for maximum performance. (2)
2.7 Choose a term/concept from COLUMN B that matches the description in COLUMN A. Write only the letter (A–D) next to the question number (2.7.1–2.7.4) in the ANSWER BOOK, for example 2.7.5 E.
COLUMN A | COLOMN B |
2.7.1 Example of a programming language that uses a virtual machine to compile programming code |
(4 x 1) (4) |
2.8 123D Catch is an example of a consumer cloud application. Define the term cloud application. (2)
2.9 Dropbox is an example of an online storage service that allows for the synchronisation of files. What is the advantage of file synchronising services? (2)
TOTAL SECTION B: 24
SECTION C: COMMUNICATION AND NETWORK TECHNOLOGIES
QUESTION 3
The main office used to distribute the Olympiad data to regional offices countrywide will have cabled LAN access to the Internet.
The diagram below shows the layout of the network and some of the devices that will be used. 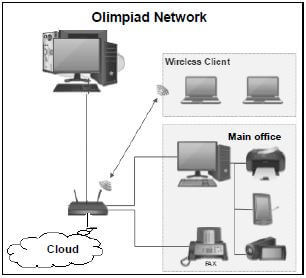
3.1 Would you classify the network in the diagram above as a LAN, WAN, MAN or PAN? Motivate your answer. (2)
3.2 Many different users involved in the Olympiad need access to the network. This resulted in setting up the network as an intranet and extranet.
3.2.1 Distinguish between intranet, extranet and the Internet. (3)
3.2.2 Give an example of a possible user of the extranet in the Olympiad scenario. (1)
3.3 A client-server network is used in the main office.
3.3.1 Motivate the choice of using a client-server network rather than a peer-to-peer network. (1)
3.3.2 The desktop computers in the office are fat clients. State TWO differences between a thin client and a fat client. (2)
3.4 UTP cables are used for the LAN in the main office.
3.4.1 Signal attenuation is one of the weaknesses of UTP cables. State TWO other weaknesses of UTP cables. (2)
3.4.2 If UTP cables are to be used over a very long distance, suggest how the signal attenuation problem can be solved without replacing them with fibre-optic cables. (1)
3.5 The office network speed is very slow. Replacing the cables has been suggested. What else can be done in terms of hardware to improve the speed of the network? (1)
3.6 Is it possible that network cards for both wired and wireless network connections are installed in a computer? Motivate your answer. (1)
3.7 The administrator must decide whether to use cloud services or a VPN to access information regarding the Olympiad.
3.7.1 State TWO disadvantages of using cloud storage. (2)
3.7.2 If the administrator decides to use cloud services, choose a cloud storage service from the list below that would be the most suitable to store critical data, such as the question paper for the Olympiad. (1)
| Office 365; Google Docs; YouTube; Facebook; Gmail |
3.7.3 Suggest ONE technology that can be used to connect two devices to share files. (1)
3.7.4 Explain the benefit of using a VPN for sharing information. (2)
3.8 The Olympiad network could be subject to spyware and malware attacks.
3.8.1 Briefly explain the term spyware. (1)
3.8.2 State TWO ways in which to minimise the risk of a computer becoming infected with spyware. (2)
3.8.3 How will a firewall help protect the Olympiad data against malware attacks? (1)
TOTAL SECTION C: 24
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
Visitors and participants attending the final round of the Olympiad will need accommodation in guesthouses. A database is required to facilitate bookings.
4.1 Data integrity is achieved by the correct use of primary and foreign keys in the design of a multitable database.
4.1.1 Explain in broad terms what data integrity refers to. (1)
4.1.2 What is the purpose of the foreign key in the design of a database table? (2)
4.1.3 Explain the term referential integrity. (2)
4.2 The database table below was designed by an apprentice programmer.
Fieldname | Data type | |
| GuesthouseID GuesthouseName TelephoneNum NumberOfRooms WiFiAvailable | Autonumber Text Text Text Text |
4.2.1 The GuesthouseID field has been identified as the primary key. What is the aim of the primary key in a database? (1)
4.2.2 The data types of some of the fields are not suitable. Identify ONE such field by writing down the fieldname and a more suitable data type. (2)
4.2.3 State TWO properties of quality data. (2)
4.3 The relational database, QuestHDB, below was designed to keep track of all the bookings at the various guesthouses. 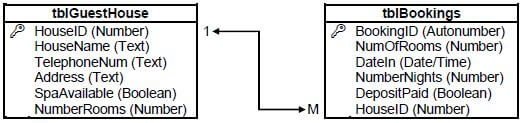
4.3.1 Write SQL statements for the following queries:
- Display ALL details of the guesthouses in alphabetical order of the guesthouse name where a spa is available. (4)
- Add a record for a new booking to tblBookings. A deposit was received for a booking at the guesthouse with HouseID 1212.
The booking is for two rooms from 8 June 2018 for three nights. (4)
4.3.2 An SQL statement has been compiled to display a list of guesthouses with a total monthly income of more than R50 000,00 for May. The cost per room per night is R400,00.
The total monthly income is a new calculated field. The calculation must be done as follows:
The number of rooms is multiplied by the number of nights and the cost per room per night.
Write down only the missing code at (a) to (e) to complete the SQL statement below correctly.  (7)
(7)
TOTAL SECTION D: 25
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
The Computer Olympiad organiser has received many questions that could be included in the Olympiad question paper. Each question needs to be evaluated for future use.
5.1 Write pseudocode to enter a word and then display the word with one less character each time, as shown in the example below.
If the word that is entered is COMPUTER, then the following should be displayed:
COMPUTER
COMPUTE
COMPUT
COMPU
COMP
COM
CO
C (4)
5.2 The results of participants have been saved incorrectly in an array called arrResults. The results of the first participant must be moved to the last index. The results for each of the other participants must be moved to the previous index.
For example, in the diagram below Brandon's results are actually Amy's results and must be moved to the first index. Claire's results are actually Brandon's results and must be moved to the second index, and so on for all the participants. Amy's results must be moved to the last index.
Write pseudocode to move the results to the correct positions in the arrResults array with an unknown number of results. (6)
5.3 An array called arrNumbers is populated with the following five values:
8 | 5 | 3 | 12 | 2 |
Another array called arrTemp is an empty array that can store five values.
The algorithm below extracts specific data from arrNumbers and stores the extracted data in arrTemp.
Loop x from 1 to length(arrNumbers)
If arrNumbers[x] modulus 4 = 0
arrTemp[x] = arrNumbers[x]
Redraw the trace table below in your ANSWER BOOK.
x | arrNumbers[x] | arrNumbers[x] modulus 4 = 0? | arrTemp[x] |
Complete the trace table above to show the contents of array arrTemp. (4)
5.4 The incomplete code given below is used to create a new file called Results.txt.
Line 1: Assignfile(TFile, 'Results.txt');
Line 2: ……………
Line 3: Writeln(TFile, 'Koos Jenkins: 78');
Line 4: Writeln(TFile, 'Amanda Smith: 78');
Line 5: ……………
Write down the statements to complete the following lines of code:
5.4.1 Line 2: Create an empty text file called Results.txt. (1)
5.4.2 Line 5: Ensure that the data will be saved to the text file. (1)
5.5 The class diagram below was designed for a school registration system.
TSchool |
- fSchoolCode - fRegDate (format dd/mm/yyyy) - fNumberOfEntries:integer - fPaid:boolean |
+ <<Constructor>> create(sCode:string;iNumEntries:integer;bPaid:boolean) + calcAmount(rFeePerEntry:real):real - determineRegDate:integer + getCode:string + getNumEntries:real + isPaid:boolean + toString:string |
5.5.1 What is the implication for the method determineRegDate being private (-) instead of public (+)? (1)
5.5.2 The number of entries was captured incorrectly.
The following method was created to change the number of entries
to the correct value received as a parameter:
Line
|
- Statement 3 is incorrect. Rewrite the statement so that the method will perform the task correctly. (1)
- What type of method is setEntries? Use a word in the list below. (1)
accessor; mutator; auxiliary
5.5.3 Analyse the declaration of the methods in the class diagram. Identify TWO possible mistakes and suggest ways in which to correct the mistakes. (2)
5.5.4 An object called objSchool of data type TSchool is used in the form class. The isPaid method is called in the OnClick event of a button.
Given:
var
bPaid: Boolean;
Explain why EACH of the following statements is INCORRECT:
- If TSchool.isPaid then … (1)
- bPaid := objSchool.isPaid := true; (1)
TOTAL SECTION E: 23
SECTION F: INTEGRATED SCENARIO
QUESTION 6
The Computer Olympiad will be managed from a main office and all communications will be sent from this office. On the day of the event the data will be distributed electronically to all institutions that have registered to participate in the Computer Olympiad.
6.1 The Olympiad website is a dynamic website which contains a link to a podcast and a video of the previous year's prize giving ceremony and links to the Olympiad's social networking tools. The instructions for the Olympiad are provided as a podcast.
6.1.1 What is a podcast? (2)
6.1.2 Name ONE file format that is used for podcasts. (1)
6.1.3 The video of the prize-giving ceremony can be streamed. Explain the concept of streaming. (2)
6.1.4 There was a request to develop an app for the Olympiad. Give TWO reasons why participants prefer to use an app instead of a web browser. (2)
6.1.5 Users want to receive automatic notifications of the latest results for the Olympiad. What technology is used to provide automatic notifications? (1)
6.1.6 Explain the difference between a dynamic website and a static website. (2)
6.1.7 Other than switching off their phones, describe TWO ways in which the office workers could manage the flood of social networking communication on their phones that can interfere with their work. (2)
6.2 Participants will need to access an encrypted file containing the Olympiad data. An 8-character password required to access the file will be sent to participants as an SMS.
6.2.1 Apart from the number of characters, state TWO other requirements for the password to be a strong password. (2)
6.2.2 Motivate the decision to send the password as an SMS rather than in an e-mail attachment if a receiver will access it on a phone. (1)
6.2.3 Explain the concept of public key encryption. (2)
6.3 Some participants may access the Olympiad questions using mobile devices.
6.3.1 State TWO disadvantages of using a mobile device for this purpose. (2)
6.3.2 How would location-based computing assist the organisers in gathering information about the participants using mobile devices? (1)
6.3.3 Suggest TWO ways in which to improve the battery life of mobile devices. (2)
6.4 A computer being used for the Olympiad displays a message indicating that the computer is low on virtual memory.
6.4.1 Define virtual memory. (2)
6.4.2 Explain why the use of virtual memory could affect the performance of a computer negatively. (2)
6.5 Cloud computing relies heavily on virtualisation technologies.
6.5.1 Name and discuss TWO ways in which virtualisation technologies can be used to benefit multiple users. (4)
6.5.2 State TWO benefits for the organisers of using SaaS (Software as a Service). (2)
6.6 One of the main reasons for the WannaCry ransomware attack was that the software on many networks and personal computers had not been updated.
6.6.1 What is ransomware? (2)
6.6.2 Why could updating the operating system software possibly prevent malicious software, such as ransomware, from accessing your computer? (1)
6.7 A DBMS for the Olympiad was designed, amongst other things, to enable the database administrator to create and edit the distributed database.
6.7.1 Name ONE other function that DBMSs allows the administrator to do. (1)
6.7.2 Explain what a distributed database system is. (2)
6.7.3 While saving data in the database, a power failure occurred. In order to protect the data integrity, a rollback of the transaction needed to be performed. Explain what a rollback of the transaction is. (1)
TOTAL SECTION F: 39
GRAND TOTAL: 150
 (1)
(1)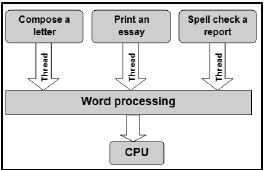 (1)
(1)